154
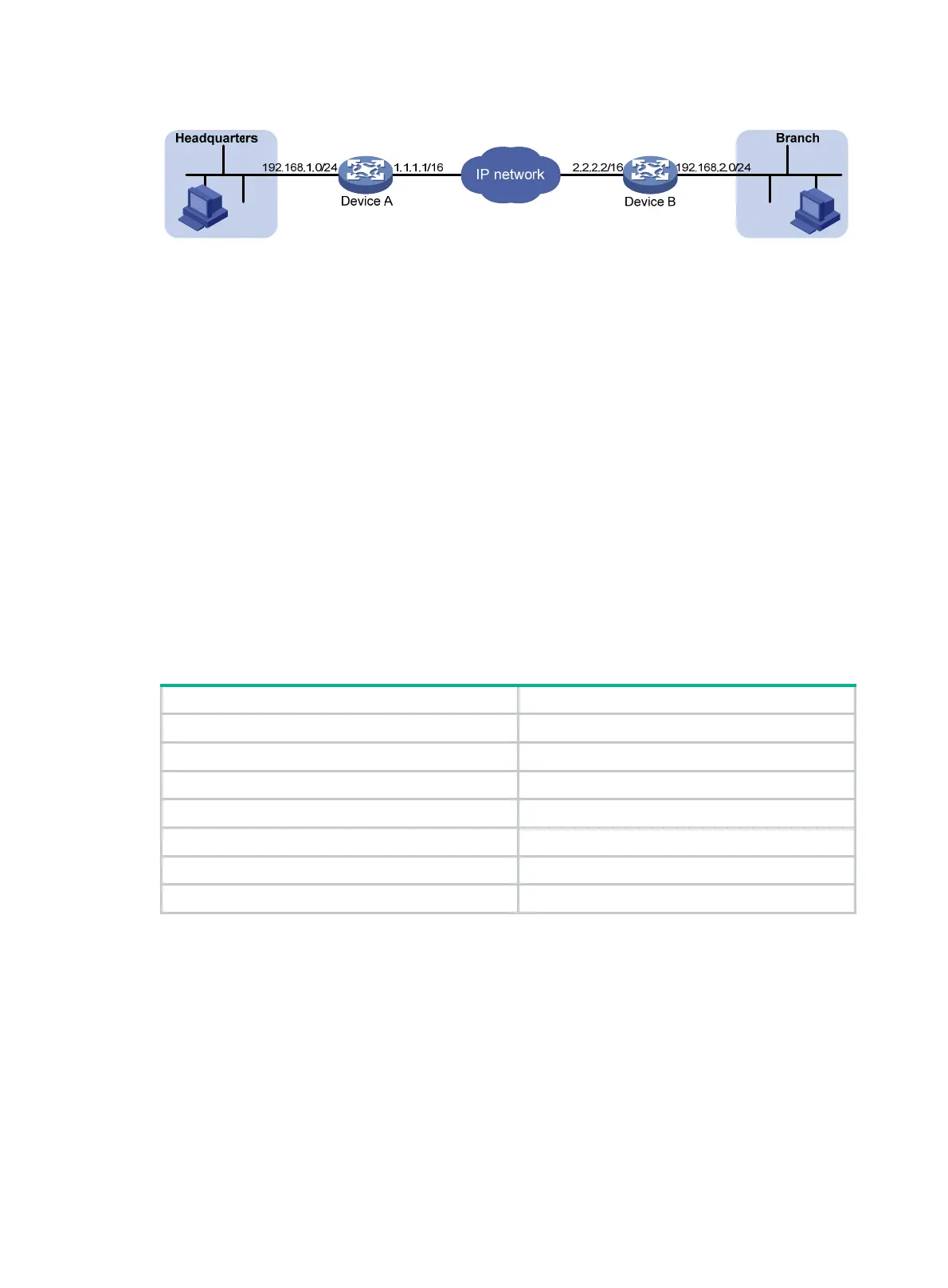
Figure 55 An IPsec VPN
You can advertise the static routes created by IPsec RRI in the internal network. IPsec RRI can
quickly create new routes for forwarding IPsec VPN traffic when an active link fails in a load balanced
environment, or when IPsec VPN traffic cannot reach the peer gateway through the default local
gateway.
Protocols and standards
• RFC 2401, Security Architecture for the Internet Protocol
• RFC 2402, IP Authentication Header
• RFC 2406, IP Encapsulating Security Payload
• RFC 4552, Authentication/Confidentiality for OSPFv3
FIPS compliance
Table 12 shows the support of MSR routers for the FIPS mode that complies with NIST FIPS 140-2
requirements. Support for features, commands, and parameters might differ in FIPS mode (see
"Configuring FIPS") and non-FIPS mode.
Table 12 Hardware and FIPS mode compatibility matrix
Hardware FIPS mode compatibility
MSR900 No
MSR93X No
MSR20-1X No
MSR20 Yes
MSR30 Yes (except the MSR30-16)
MSR50 Yes
MSR1000 Yes
Implementing IPsec
IPsec can be implemented based on ACLs, tunnel interfaces, or applications:
• ACL-based IPsec uses ACLs to identify the data flows to be protected. To implement
ACL-based IPsec, configure IPsec policies, reference ACLs in the policies, and apply the
policies to physical interfaces (see "Implementing ACL-based IPsec"). By using
ACLs, you can
customize IPsec policies as needed, implementing IPsec flexibly.
• Tunnel interface-based IPsec, or routing-based IPsec, depends on the routing mechanism to
select the data flows to be protected. To implement tunnel interface-based IPsec, configure
IPsec profiles and apply them to IPsec tunnel interfaces (see "Implementing tunnel

 Loading...
Loading...




