202
Relationship between IKE and IPsec
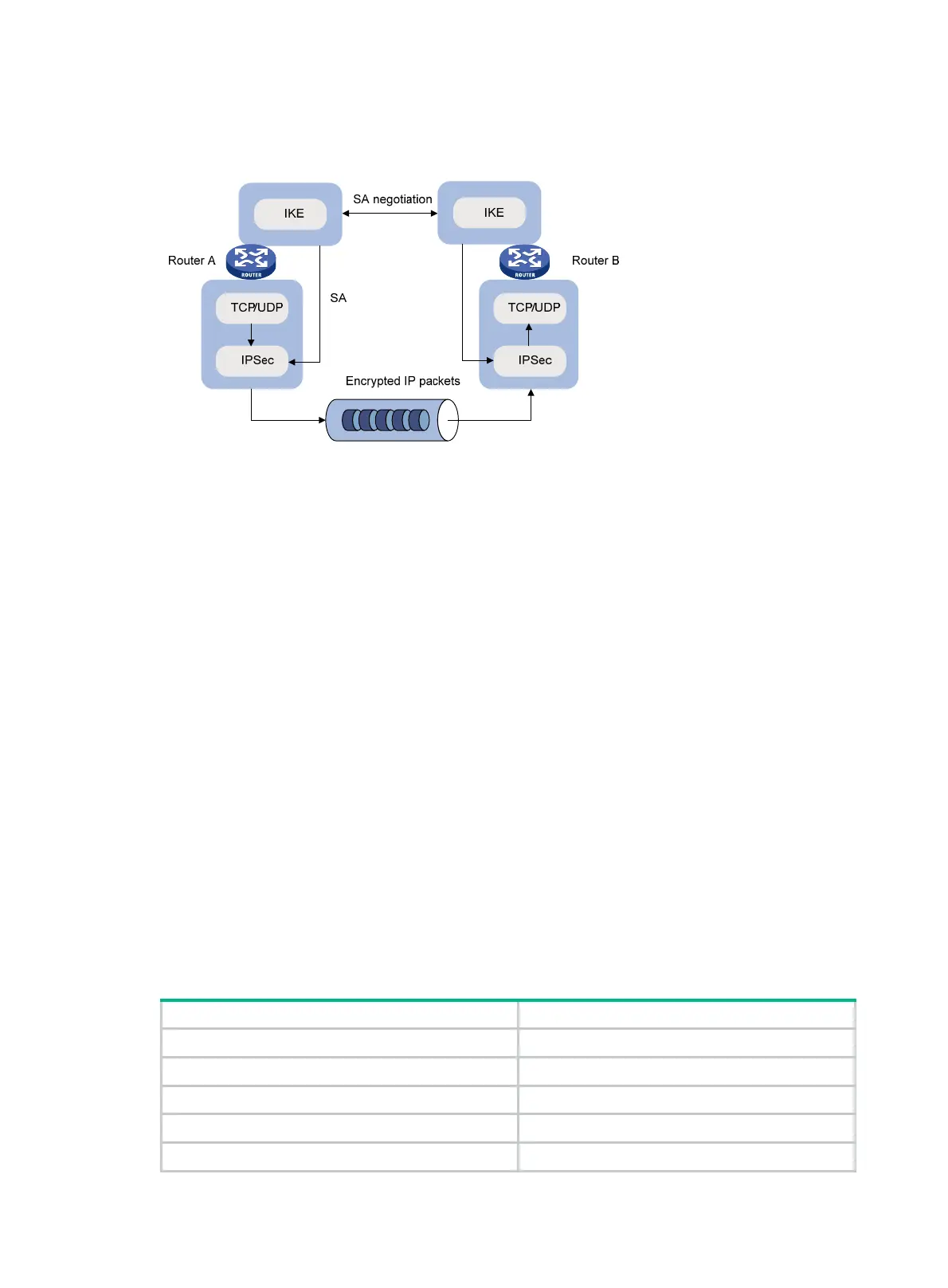
Figure 65 Relationship between IKE and IPsec
Figure 65 illustrates the relationship between IKE and IPsec:
• IKE is an application layer protocol using UDP and functions as the signaling protocol of IPsec.
• IKE negotiates SAs for IPsec and delivers negotiated parameters and generated keys to IPsec.
• IPsec uses the SAs set up through IKE negotiation for encryption and authentication of IP
packets.
• When IPsec SAs are traffic expired:
{ In FIPS mode, both the IPsec SAs and the corresponding IKE SAs are renegotiated.
{ In non-FIPS mode, only the IPsec SAs are renegotiated.
Protocols and standards
• RFC 2408, Internet Security Association and Key Management Protocol (ISAKMP)
• RFC 2409, The Internet Key Exchange (IKE)
• RFC 2412, The OAKLEY Key Determination Protocol
FIPS compliance
Table 12 shows the support of devices for the FIPS mode that complies with NIST FIPS 140-2
requirements. Support for features, commands, and parameters might differ in FIPS mode and
non-FIPS mode. For more information about FIPS mode, see HPE FlexNetwork MSR Router Series
Comware 5 Security Configuration Guide.
Table 13 Hardware and FIPS mode compatibility matrix
Hardware FIPS mode
MSR900 No
MSR93X No
MSR20-1X No
MSR20 Yes
MSR30 Yes (except the MSR30-16)

 Loading...
Loading...




