453
Configuring group domain VPN
Group domain Virtual Private Network (group domain VPN) provides a point-to-multipoint tunnel-less
VPN solution. It is mainly used to protect multicast traffic.
Overview
Group domain VPN uses a group-based IPsec model. Members in a group use a common IPsec
policy, which includes security protocols, algorithms, and keys.
Group domain VPN has the following advantages over conventional IPsec VPN:
• Better network scalability—Conventional IPsec VPNs require that each pair of
communication peers establish independent IKE SAs and IPsec SAs. In group domain VPNs,
members in a group use the same pair of IPsec SAs, simplifying network management and
improving scalability.
• Without routing re-deployment—Conventional IPsec VPNs establish connections over
tunnels that encapsulate new IP headers for packets. You must reconfigure routes to forward
tunneled packets. In group domain VPNs, the outer IP header is the same as the inner IP
header. You do not need to change existing route configurations.
• Better QoS—In conventional IPsec VPNs, you must reconfigure QoS policies because a new
IP header is added before the original IP header. Group domain VPN keeps the original IP
header, simplifying QoS deployment.
• Higher multicast efficiency—Conventional IPsec VPNs use point-to-point tunnels. A
tunnel-end device must send an encrypted multicast packet to each tunnel peer in the multicast
group. Group domain VPNs use tunnel-less connections. A tunnel-end device sends only one
encrypted packet to all members in a group.
• Any-to-any connectivity—In a group domain VPN, all members in a group share the same
pair of IPsec SAs. Any two members in the same group can encrypt and de-encrypt packets of
each other, implementing any-to-any connectivity.
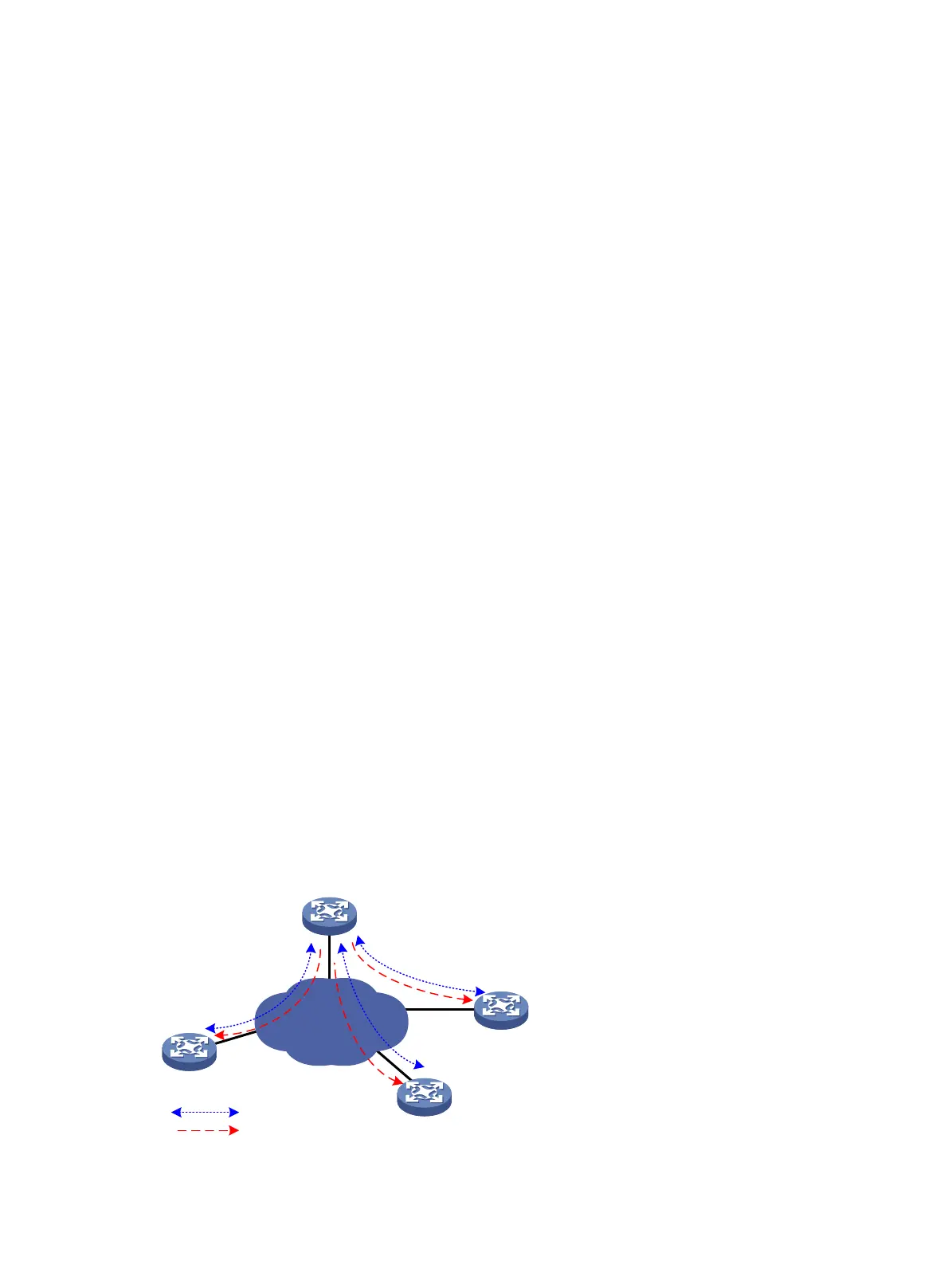
Group domain VPN structure
As shown in Figure 151, a typical group domain VPN comprises a key server (KS) and group
members (GM).
Figure 151 Group domain VPN structure
KS
GM
GM
GM
IP network
Reigster
Update keys

 Loading...
Loading...




