411
0001-0203-0406 192.168.0.1 N/A Eth1/2 Static
N/A 192.168.0.2 N/A Eth1/1 Static
Dynamic IPv4 source guard using DHCP
snooping configuration example
Network requirements
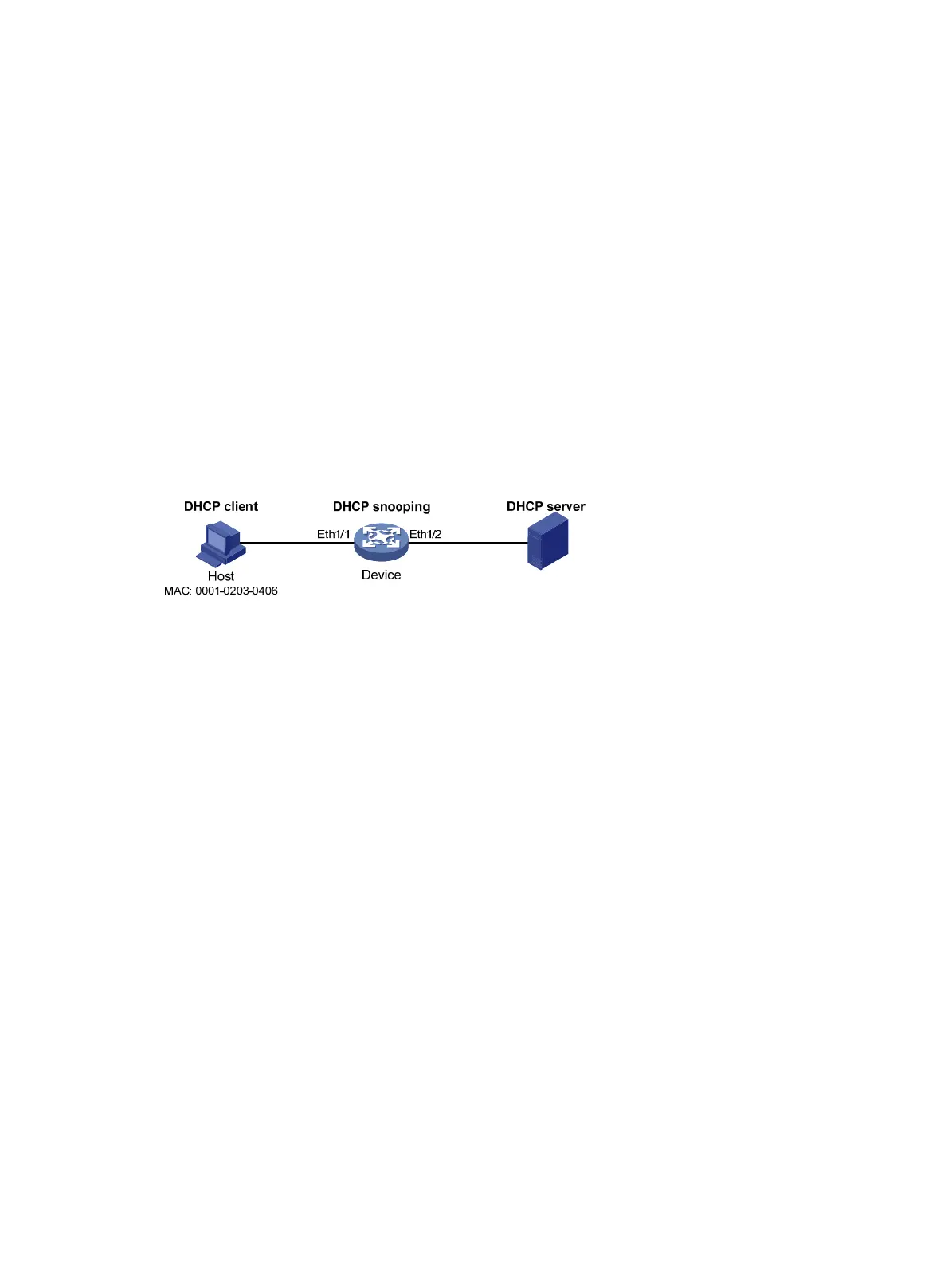
As shown in Figure 140, the device connects to the host (client) and the DHCP server through ports
Ethernet 1/1 and Ethernet 1/2 respectively. The host obtains an IP address from the DHCP server.
Enable DHCP snooping on the device to record the DHCP snooping entry of the host. Enable the
IPv4 source guard function on the device's port Ethernet 1/1 to filter packets based on the DHCP
snooping entry, allowing only packets from clients that obtain IP addresses through the DHCP server
to pass.
For information about DHCP server configuration, see HPE FlexNetwork MSR Router Series
Comware 5 Layer 3—IP Services Configuration Guide.
Figure 140 Network diagram
Configuration procedure
1. Configure DHCP snooping:
# Enable DHCP snooping.
<Device> system-view
[Device] dhcp-snooping
# Configure port Ethernet 1/2, which is connected to the DHCP server, as a trusted port.
[Device] interface ethernet1/2
[Device-Ethernet1/2] dhcp-snooping trust
[Device-Ethernet1/2] quit
2. Enable IPv4 source guard on port Ethernet 1/1 to filter packets based on both the source IP
address and MAC address.
[Device] interface ethernet1/1
[Device-Ethernet1/1] ip verify source ip-address mac-address
[Device-Ethernet1/1] quit
Verifying the configuration
# Display the IPv4 source guard binding entries generated on port Ethernet 1/1.
[Device] display ip source binding
Total entries found: 1
MAC Address IP Address VLAN Interface Type
0001-0203-0406 192.168.0.1 1 Eth1/1 DHCP-SNP
# Display DHCP snooping entries to see whether they are consistent with the dynamic entries
generated on Ethernet 1/1.
[Device] display dhcp-snooping
DHCP snooping is enabled.

 Loading...
Loading...




