283
1. When an unauthenticated user enters a website address in the browser's address bar to access
the Internet, an HTTP request is created and sent to the access device. The access device then
redirects the HTTP request to the portal server's Web authentication homepage. For extended
portal functions, authentication clients must run the portal client software.
2. On the authentication homepage/authentication dialog box, the user enters and submits the
authentication information, which the portal server then transfers to the access device.
3. Upon receipt of the authentication information, the access device communicates with the
authentication/accounting server for authentication and accounting.
4. After successful authentication, the access device checks whether there is a corresponding
security policy for the user. If not, it allows the user to access the Internet. Otherwise, the client
communicates with the access device and the security policy server for security check. If the
client passes security check, the security policy server authorizes the user to access the
Internet resources.
NOTE:
Portal authentication supports NAT traversal whether it is initiated by a Web client or an HPE iNode
client. When the portal authentication client is on a private network, but the portal server is on a
public network and the access device is enabled with NAT, network address translations performed
on the access device do not affect portal authentication. However, in such a case, Hewlett Packard
Enterprise recommends using an interface's public IP address as the source address of outgoing
portal packets. You can also solve this problem by specifying the NAS-IP for outgoing RADIUS
packets.
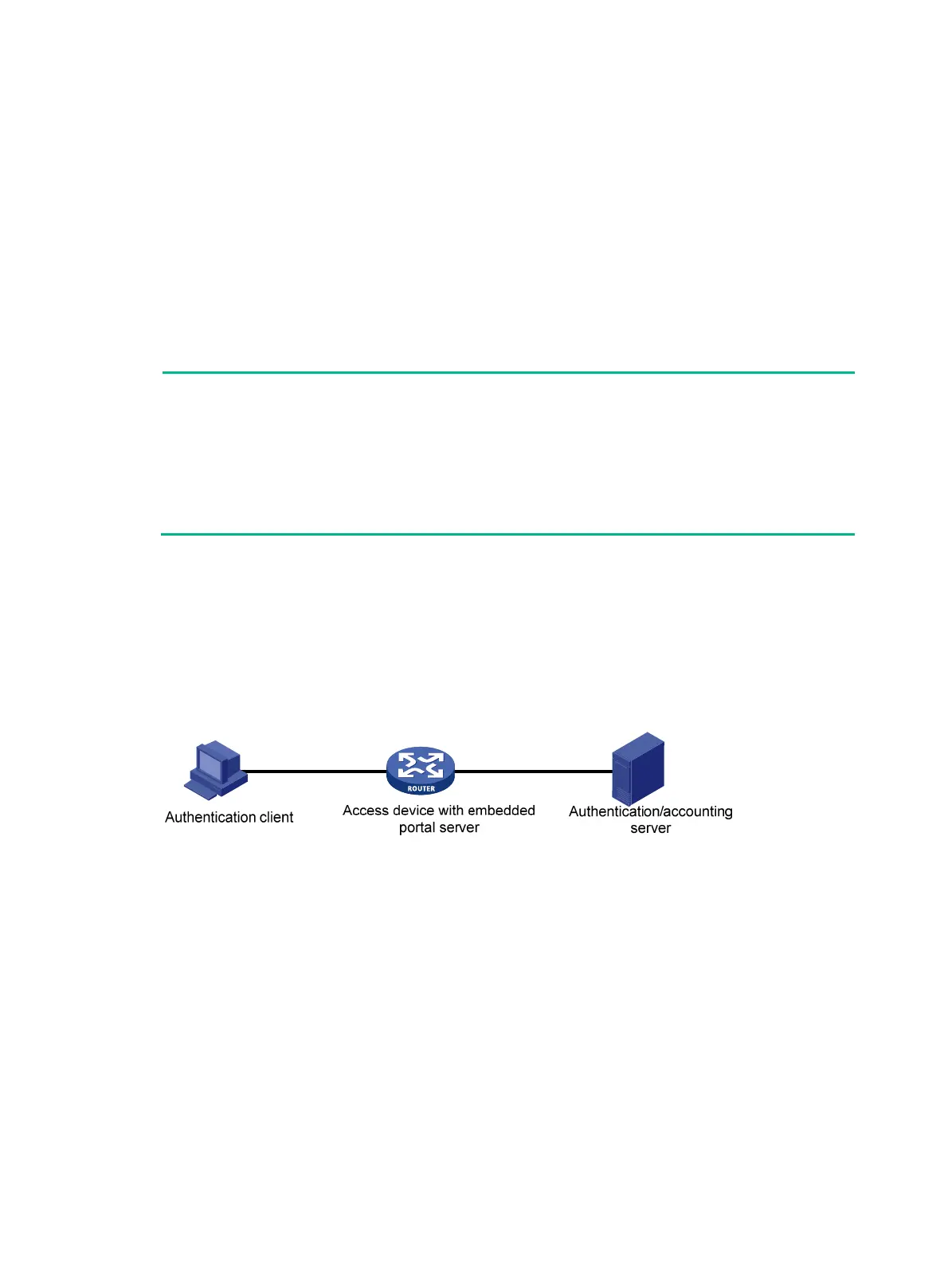
Portal system using the local portal server
In addition to using a separate device as the portal server, a portal system can also use the local
portal server function of the access device to authenticate Web users directly. In this case, the portal
system consists of only three components: authentication client, access device, and
authentication/accounting server, as shown in Figure 86.
Figure 86
Portal system using the local portal server
No security policy server is needed for local portal service, because the portal system using the local
portal server does not support extended portal functions.
The local portal server function of the access device implements only some simple portal server
functions. It only allows users to log on and log off through the Web interface. It cannot take the place
of an independent portal server.
Protocols used for interaction between the client and local portal server
HTTP can be used for interaction between an authentication client and an access device providing
the local portal server function. If HTTP is used, there are potential security problems because HTTP
packets are transferred in plain text.
Authentication page customization support
The local portal server function allows you to customize authentication pages. You can customize
authentication pages by editing the corresponding HTML files and then compress and save the files
to the storage medium of the device. A set of customized authentication pages consists of six
authentication pages: the logon page, the logon success page, the online page, the logoff success

 Loading...
Loading...




