388
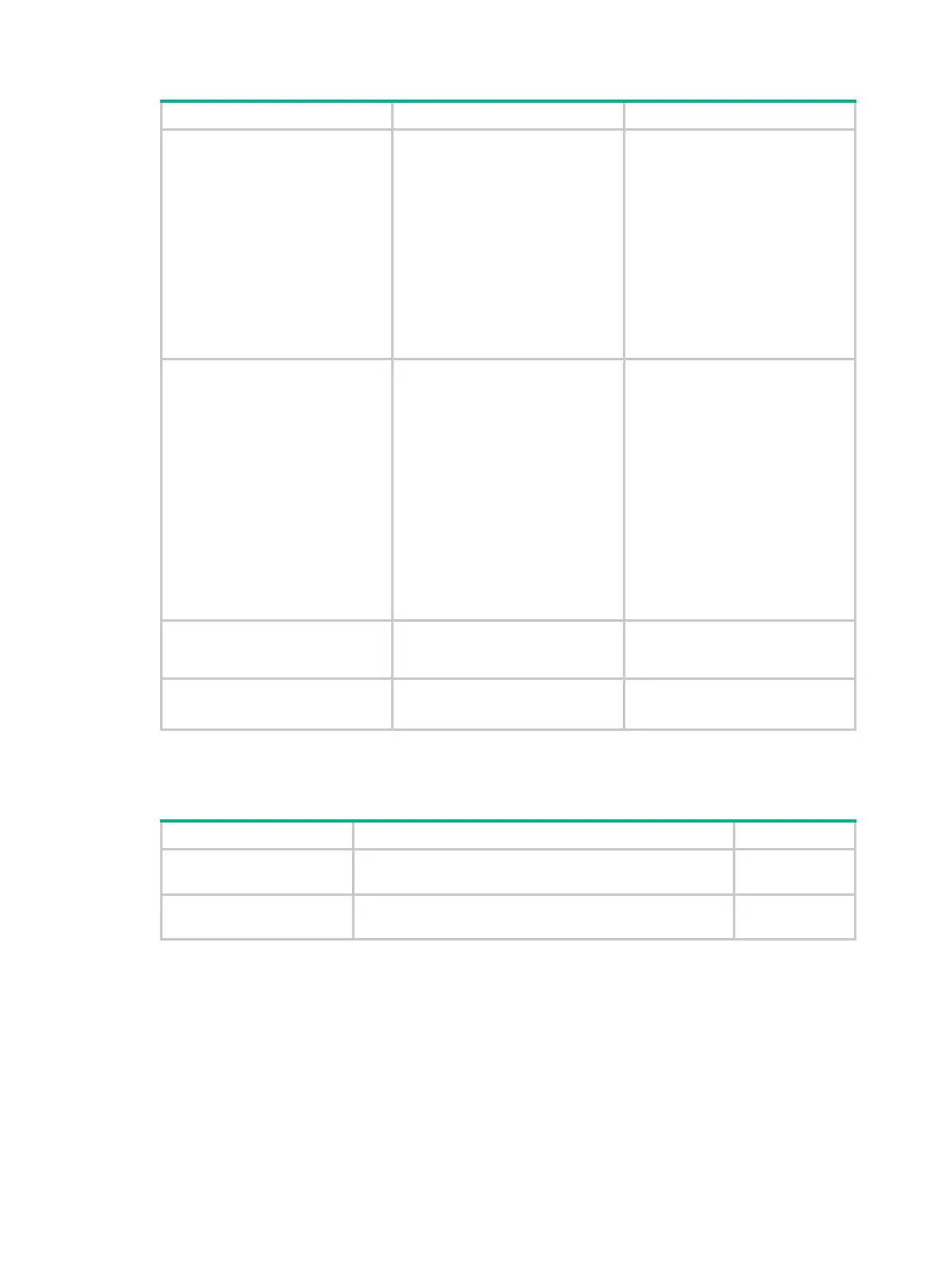
Step Command Remarks
4. Specify a PKI domain for the
SSL client policy.
pki-domain
domain-name
Optional.
No PKI domain is specified by
default.
If the SSL server authenticates
the SSL client through a digital
certificate, you must use this
command to specify a PKI domain
and request a local certificate for
the SSL client in the PKI domain.
For information about how to
configure a PKI domain, see
"Configuring PKI."
5. Specify the preferred cipher
suite for the SSL client
policy.
• In non-FIPS mode:
prefer-cipher
{ rsa_3des_ede_cbc_sha |
rsa_aes_128_cbc_sha |
rsa_aes_256_cbc_sha |
rsa_des_cbc_sha |
rsa_rc4_128_md5 |
rsa_rc4_128_sha }
• In FIPS mode:
prefer-cipher
{ dhe_rsa_aes_128_cbc_s
ha |
dhe_rsa_aes_256_cbc_sh
a | rsa_aes_128_cbc_sha |
rsa_aes_256_cbc_sha }
Optional.
rsa_rc4_128_md5
by default.
6. Specify the SSL protocol
version for the SSL client
policy.
version
{
ssl3.0
|
tls1.0
}
Optional.
TLS 1.0 by default.
7. Enable certificate-based
SSL server authentication.
server-verify enable
Optional.
Enabled by default.
Displaying and maintaining SSL
Task Command Remarks
Display SSL server policy
information.
display ssl server-policy
{ policy-name
|
all
} [
|
{
begin
|
exclude
|
include
} regular-expression ]
Available in any
view.
Display SSL client policy
information.
display ssl client-policy
{
policy-name
|
all
} [
|
{
begin
|
exclude
|
include
} regular-expression ]
Available in any
view.
SSL server policy configuration example
Network requirements
As shown in Figure 133, users need to access and control the device through Web page.
To prevent illegal users' access and to make sure data is not eavesdropped or tampered with,
configure SSL on the device so that users must use HTTPS to log in to the Web interface of the
device.
In this example, the CA server runs Windows Server and has the SCEP plug-in installed.

 Loading...
Loading...




