350
{ The client directly sends the user's public key information to the server, and the server
checks the validity of the user's public key.
{ The client sends the user's public key information to the server through a digital certificate,
and the server checks the validity of the digital certificate. When acting as a client, the
device does not support this method.
• Password-publickey authentication—The server requires clients that run SSH2 to pass both
password authentication and publickey authentication. However, if a client runs SSH1, it only
needs to pass either authentication.
• Any authentication—The server requires the client to pass either of password authentication
and publickey authentication.
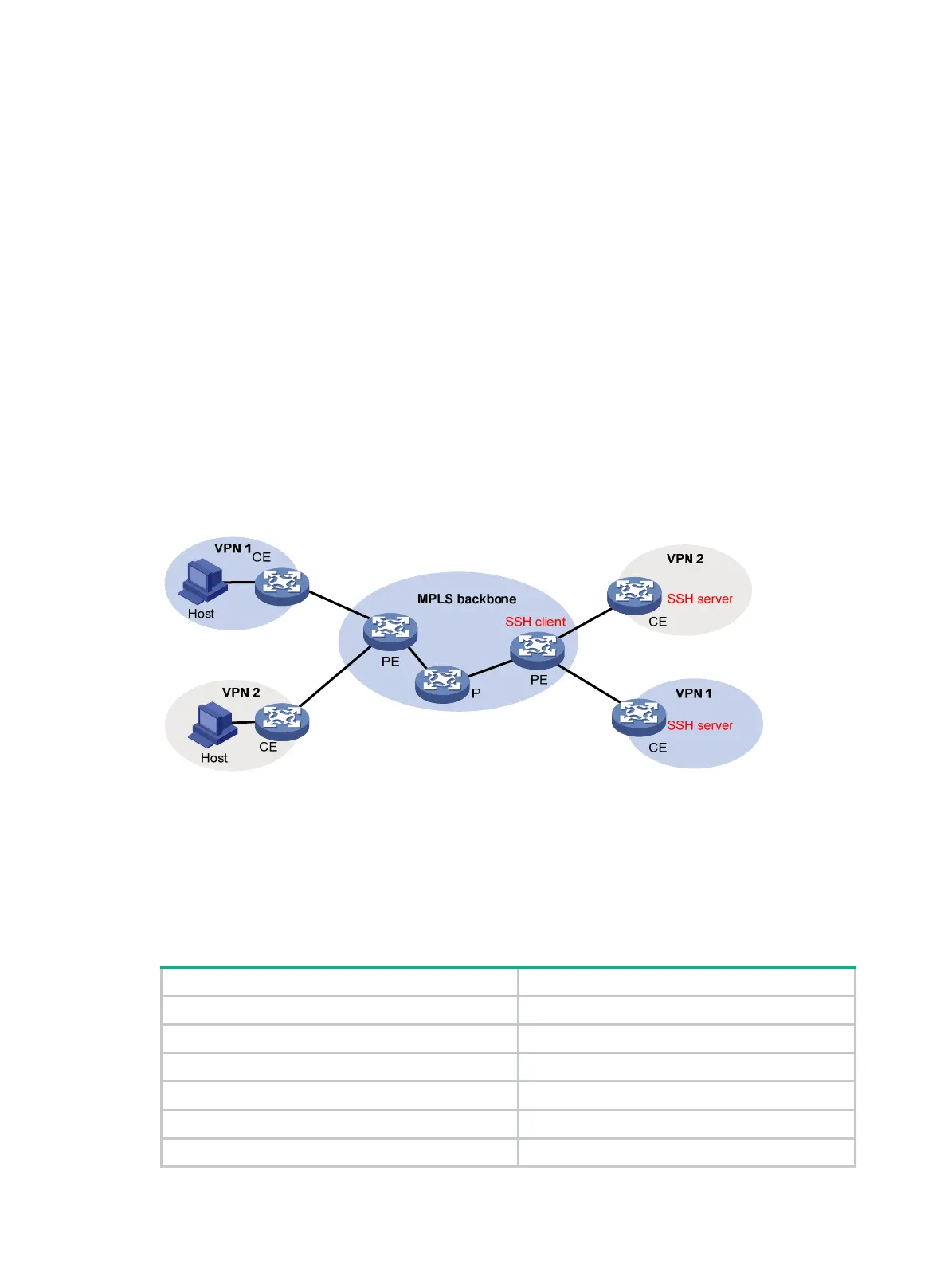
SSH support for MPLS L3VPN
With this function, you can configure the device as an SSH client to establish connections with SSH
servers in different MPLS L3VPNs.
As shown in Figure 116 , the
hosts in VPN 1 and VPN 2 access the MPLS backbone through PEs, with
the services of the two VPNs isolated. After a PE is enabled with the SSH client function, it can
establish SSH connections with CEs in different VPNs that are enabled with the SSH server function
to implement secure access to the CEs and secure transfer of log file.
Figure 116 SSH support for MPLS L3VPN
FIPS compliance
Table 19 shows the support of MSR routers for the FIPS mode that complies with NIST FIPS 140-2
requirements. Support for features, commands, and parameters might differ in FIPS mode (see
"Configuring FIPS") and non-FIPS mode.
Table 19 Hardware and FIPS mode compatibility matrix
Hardware FIPS mode compatibility
MSR900 No
MSR93X No
MSR20-1X No
MSR20 Yes
MSR30 Yes (except the MSR30-16)
MSR50 Yes

 Loading...
Loading...




