454
The KS maintains security policies for groups, and creates and maintains key information. It
responds to registration requests from GMs and sends rekey messages to GMs.
After a GM registers with the KS, the KS sends the IPsec policy and keys to the GM. The keys are
periodically updated. Before the key lifetime expires, the KS notifies all GMs to update keys by
sending rekey messages.
There are two types of rekey messages:
• Traffic encryption key—TEK messages are shared by all GMs in a group and used to encrypt
traffic between GMs.
• Key encryption key—KEK messages are shared by all GMs in a group and used to encrypt
rekey messages sent from the KS to GMs.
You can configure multiple KSs to achieve high availability and load sharing.
GMs are a group of network devices that use the same IPsec policy to communicate with each other.
A GM provides a group ID during registration with the KS. The KS assigns the corresponding IPsec
policy and keys to the GM according to the group ID.
Group domain VPN establishment
Group domain VPN establishment involves the following phases:
• Registration—GMs register with the KS.
• Data protection—GMs protect data.
• Rekey—The KS updates keys.
Registration
After you apply an IPsec policy for group domain VPN to an interface on a GM, the GM registers with
the KS. The registration includes two negotiations: IKE negotiation (phase 1) and Group Domain of
Interpretation (GDOI) negotiation (phase 2).
• IKE negotiation—The GM and KS negotiate keys, perform mutual identity authentication, and
if the authentication succeeds, establish an IKE SA used to protect GDOI negotiation.
• GDOI negotiation—The GM obtains the IPsec policy from the KS by using the GDOI protocol.
For more information, see GROUPKEY-PULL in RFC 3547.
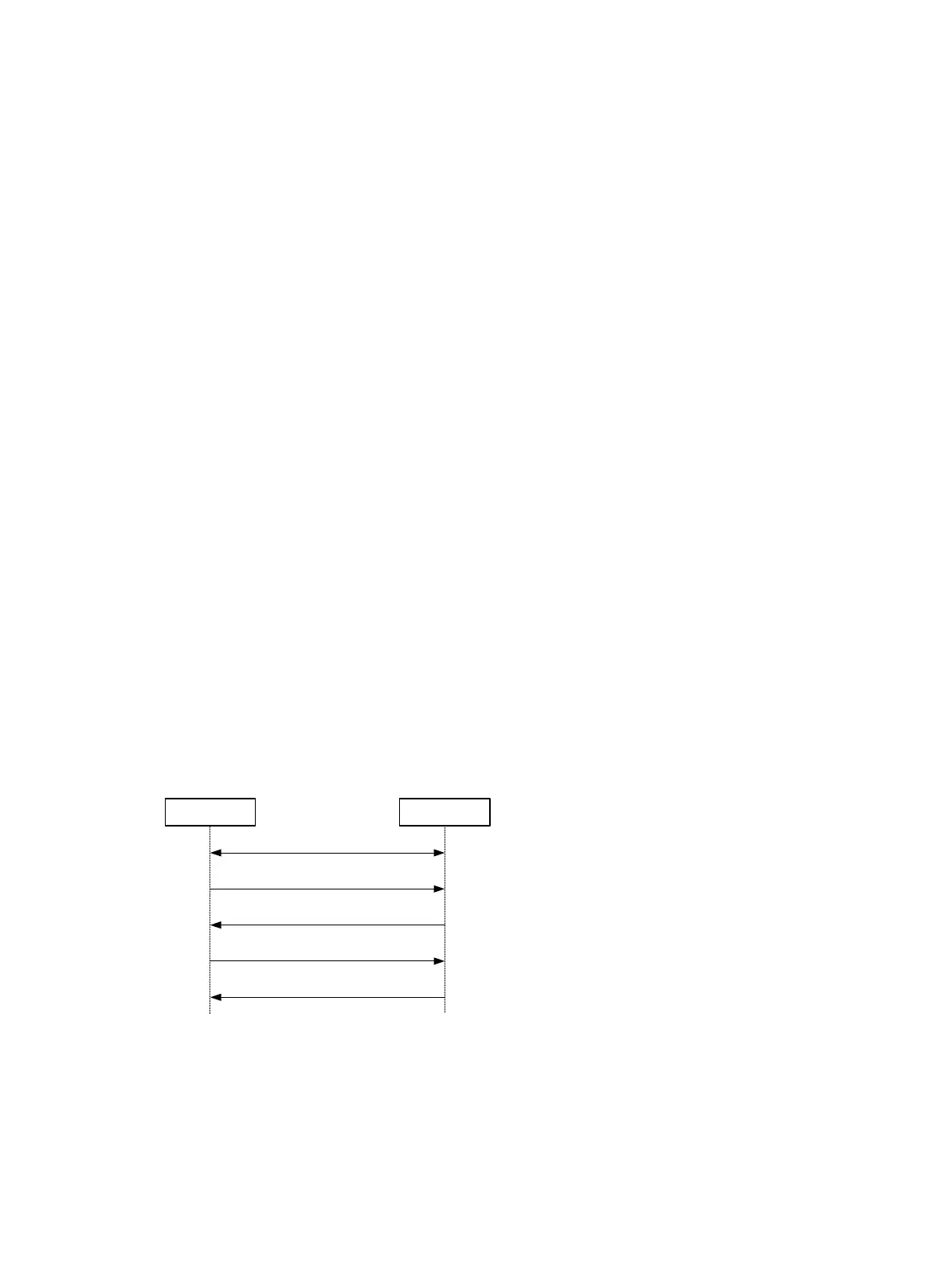
Figure 152 Registration process
As shown in Figure 152,
1. The GM and KS perform IKE negotiation.
2. The GM sends its group ID to the KS.
3. The KS sends an IPsec policy to the GM according to the group ID.
GM KS
2) Group ID
3) SA policy
4) Acknowledgement
5) TEK and KEK
1) IKE negotiation

 Loading...
Loading...




