331
Cross-subnet portal authentication across VPNs
Network requirements
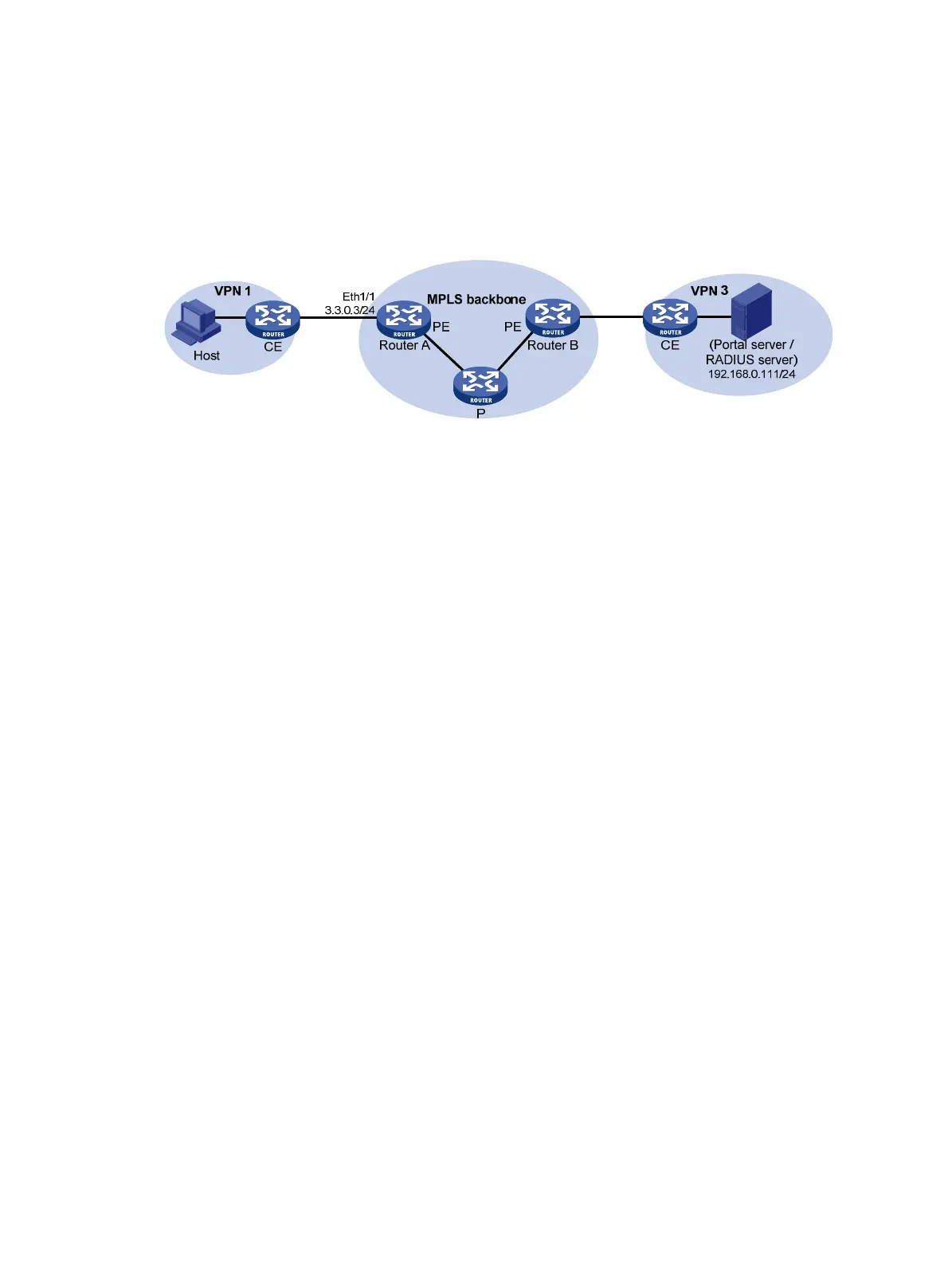
As shown in Figure 111, Router A, as the PE device connecting the user side, needs to provide
cross-subnet portal authentication for hosts in VPN 1. The RADIUS server/portal server is in VPN 3.
Figure 111 Network diagram
Configuration prerequisites
• Before enabling portal authentication, be sure to configure the MPLS L3VPN capabilities
correctly and specify VPN targets for VPN 1 and VPN 3 so that VPN 1 and VPN 3 can
communicate with each other. This example gives only the access authentication configuration
on the user-side PE. For information about MPLS L3VPN, see HPE FlexNetwork MSR Router
Series Comware 5 MPLS Configuration Guide.
• Configure the RADIUS server correctly to provide normal authentication/accounting functions
for users.
Configuration procedure
1. Configure a RADIUS scheme:
# Create a RADIUS scheme named rs1 and enter its view.
<RouterA> system-view
[RouterA] radius scheme rs1
# Configure the VPN instance to which the RADIUS scheme belongs as vpn3.
[RouterA-radius-rs1] vpn-instance vpn3
# Set the server type for the RADIUS scheme. When using the CAMS or IMC server, set the
server type to extended.
[RouterA-radius-rs1] server-type extended
# Specify the primary authentication server and primary accounting server, and configure the
keys for communication with the servers.
[RouterA-radius-rs1] primary authentication 192.168.0.111
[RouterA-radius-rs1] primary accounting 192.168.0.111
[RouterA-radius-rs1] key accounting simple radius
[RouterA-radius-rs1] key authentication simple radius
# Configure the device to not carry the ISP domain name in the username sent to the RADIUS
server.
[RouterA-radius-rs1] user-name-format without-domain
# Specify the source IP address for RADIUS packets to be sent as 3.3.0.3. This address must
be the same as that of the access device specified on the server.
[RouterA-radius-rs1] nas-ip 3.3.0.3
[RouterA-radius-rs1] quit
2. Configure an authentication domain:

 Loading...
Loading...




