466
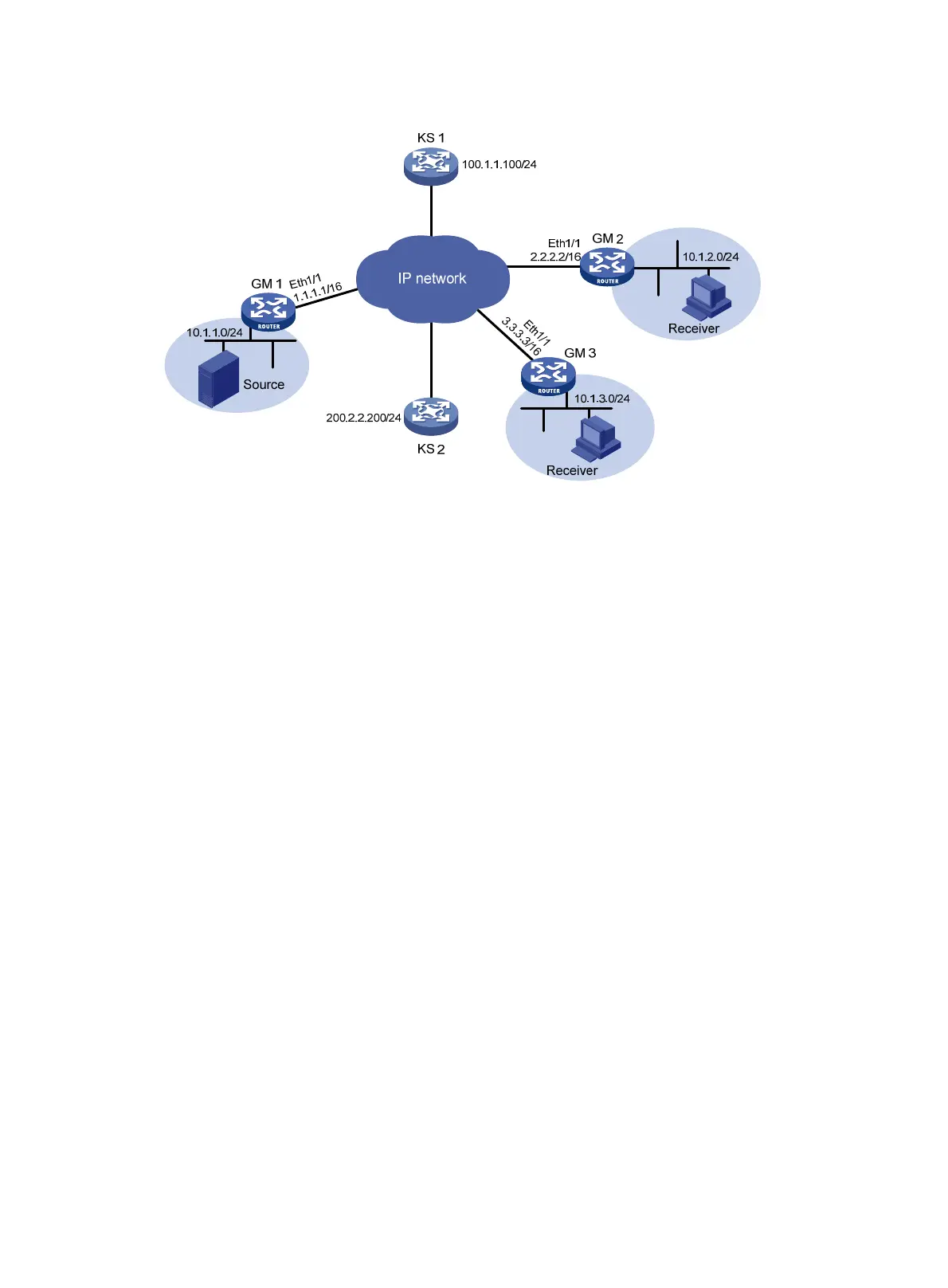
Figure 155 Network diagram
Configuration procedure
Make sure each GM (GM 1, GM 2, and GM 3) and each KS can reach each other, and the two KSs
can reach each other.
Make sure the multicast packets between the GMs and the multicast rekey messages between the
KS and GMs can be forwarded correctly.
By default, the KS multicasts rekey messages. To unicast rekey messages, use the rekey transport
unicast command.
Configuring KS 1
# Configure IP addresses for interfaces. (Details not shown.)
# Configure IKE proposal 1.
<KS1> system-view
[KS1] ike proposal 1
# Specify the encryption algorithm AES-CBC 128 for IKE proposal 1.
[KS1-ike-proposal-1] encryption-algorithm aes-cbc 128
# Specify the authentication algorithm SHA1 for IKE proposal 1.
[KS1-ike-proposal-1] authentication-algorithm sha
# Specify DH group 2 for IKE proposal 1.
[KS1-ike-proposal-1] dh group2
[KS1-ike-proposal-1] quit
# Create the IKE peer toks2 for IKE negotiation with KS 2.
[KS1] ike peer toks2
# Apply IKE proposal 1 to the IKE peer.
[KS1-ike-peer-toks2] proposal 1
# Configure the pre-shared key as tempkey1 in plaintext.
[KS1-ike-peer-toks2] pre-shared-key simple tempkey1
# Specify the IP address of the IKE peer as 200.2.2.200.

 Loading...
Loading...




