234
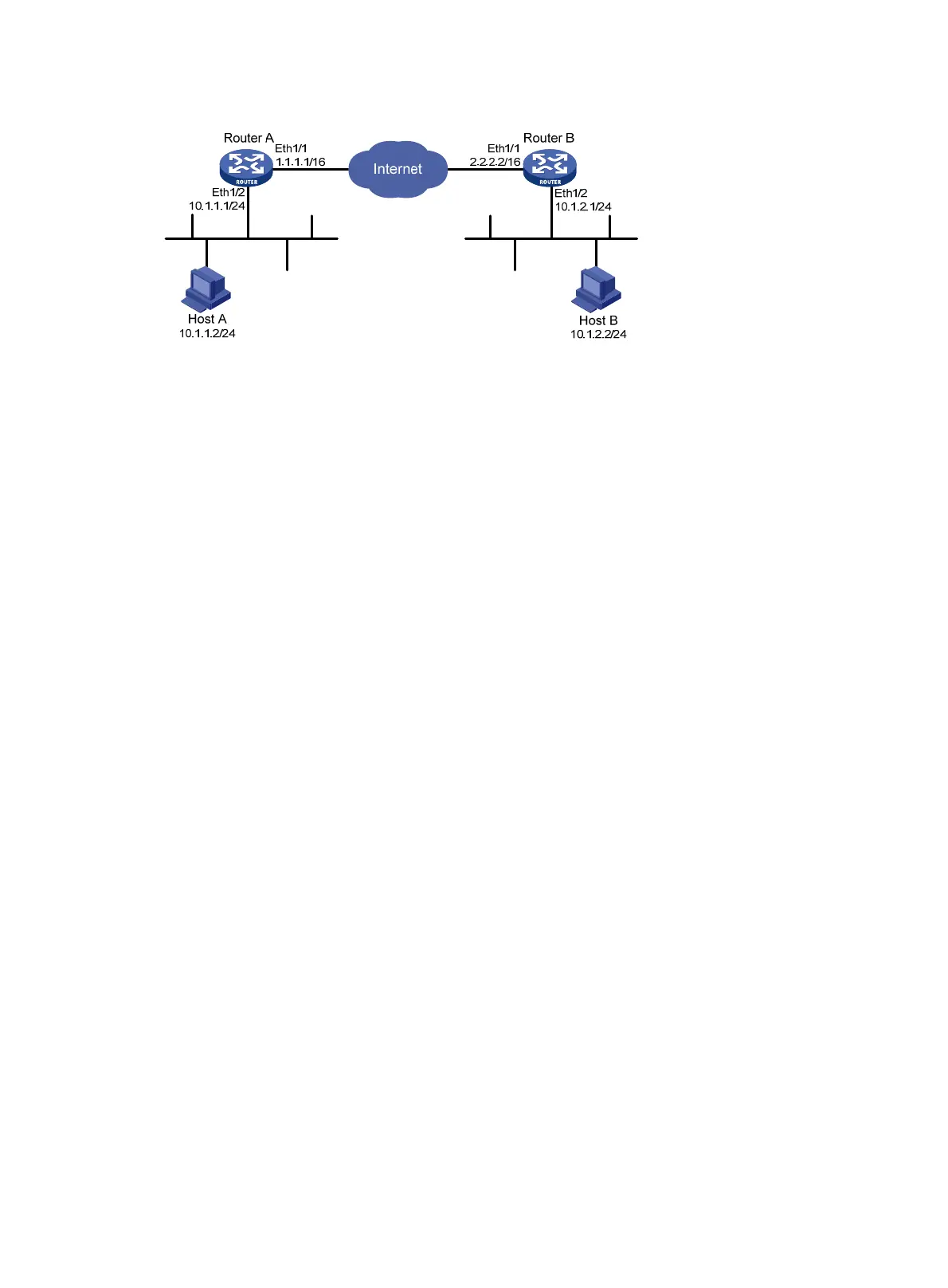
Figure 70 Network diagram
Configuration prerequisites
Make sure Router A and Router B can reach each other.
Make sure both Router A and Router B have the CA certificates for certificate signing and
authentication and have obtained a local certificate for IKEv2 negotiation.
Configuring the security gateway Router A
1. Configure PKI:
# Create PKI entity entity_a.
<RouterA> system-view
[RouterA] pki entity entity_a
[RouterA-pki-entity-entity_a] quit
# Configure PKI domain domain_a, the PKI domain used for certificate signing.
[RouterA] pki domain domain_a
[RouterA-pki-domain-domain_a] certificate request entity entity_a
[RouterA-pki-domain-domain_a] crl check disable
[RouterA-pki-domain-domain_a] quit
# Import the CA certificate for certificate signing in offline mode.
[RouterA] pki import-certificate ca domain domain_a der filename aaa_ca.crt
Is the finger print correct?(Y/N):y
# Import the local certificate in offline mode.
[RouterA] pki import-certificate local domain domain_a p12 filename sec001.docm.pfx
# Create PKI entity entity_b.
[RouterA] pki entity entity_b
[RouterA-pki-entity-entity_b] quit
# Configure PKI domain domain_b, the PKI domain used for certificate authentication.
[RouterA] pki domain domain_b
[RouterA-pki-domain-domain_b] certificate request entity entity_b
[RouterA-pki-domain-domain_b] crl check disable
[RouterA-pki-domain-domain_b] quit
# Import the CA certificate for certificate signing in offline mode.
[RouterA] pki import-certificate ca domain domain_b der filename bbb_ca.crt
Is the finger print correct?(Y/N):y
2. Configure ACL 3101 to identify traffic from subnet 10.1.1.0/24 to subnet 10.1.2.0/24.
[RouterA] acl number 3101
[RouterA-acl-adv-3101] rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0
0.0.0.255

 Loading...
Loading...




