1-19
Catalyst 3750-X and 3560-X Switch Software Configuration Guide
OL-25303-03
Chapter 1 Configuring Switch-Based Authentication
Controlling Switch Access with RADIUS
RADIUS is not suitable in these network security situations:
• Multiprotocol access environments. RADIUS does not support AppleTalk Remote Access (ARA),
NetBIOS Frame Control Protocol (NBFCP), NetWare Asynchronous Services Interface (NASI), or
X.25 PAD connections.
• Switch-to-switch or router-to-router situations. RADIUS does not provide two-way authentication.
RADIUS can be used to authenticate from one device to a non-Cisco device if the non-Cisco device
requires authentication.
• Networks using a variety of services. RADIUS generally binds a user to one service model.
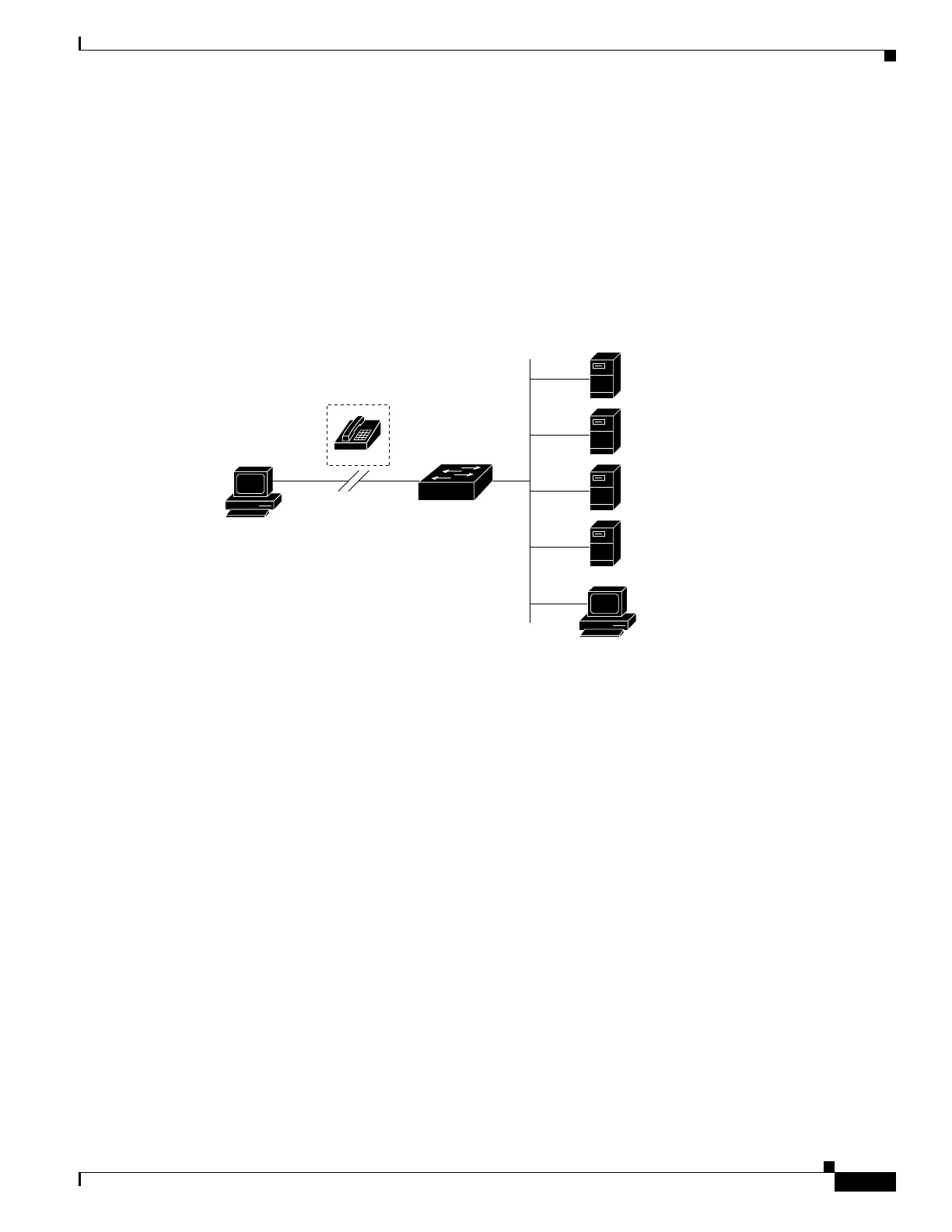
Figure 1-2 Transitioning from RADIUS to TACACS+ Services
RADIUS Operation
When a user attempts to log in and authenticate to a switch that is access controlled by a RADIUS server,
these events occur:
1. The user is prompted to enter a username and password.
2. The username and encrypted password are sent over the network to the RADIUS server.
3. The user receives one of these responses from the RADIUS server:
a. ACCEPT—The user is authenticated.
b. REJECT—The user is either not authenticated and is prompted to re-enter the username and
password, or access is denied.
c. CHALLENGE—A challenge requires additional data from the user.
d. CHALLENGE PASSWORD—A response requests the user to select a new password.
86891
RADIUS
server
RADIUS
server
TACACS+
server
TACACS+
server
R1
R2
T1
T2
Remote
PC
Workstation
 Loading...
Loading...











