1-12
Catalyst 3750-X and 3560-X Switch Software Configuration Guide
OL-25303-03
Chapter 1 Configuring IEEE 802.1x Port-Based Authentication
Understanding IEEE 802.1x Port-Based Authentication
To avoid loss of connectivity to the RADIUS server, you should ensure that there is a redundant
connection to it. For example, you can have a redundant connection to the stack master and another to a
stack member, and if the stack master fails, the switch stack still has connectivity to the RADIUS server.
802.1x Host Mode
You can configure an 802.1x port for single-host or for multiple-hosts mode. In single-host mode (see
Figure 1-1 on page 1-2), only one client can be connected to the 802.1x-enabled switch port. The switch
detects the client by sending an EAPOL frame when the port link state changes to the up state. If a client
leaves or is replaced with another client, the switch changes the port link state to down, and the port
returns to the unauthorized state.
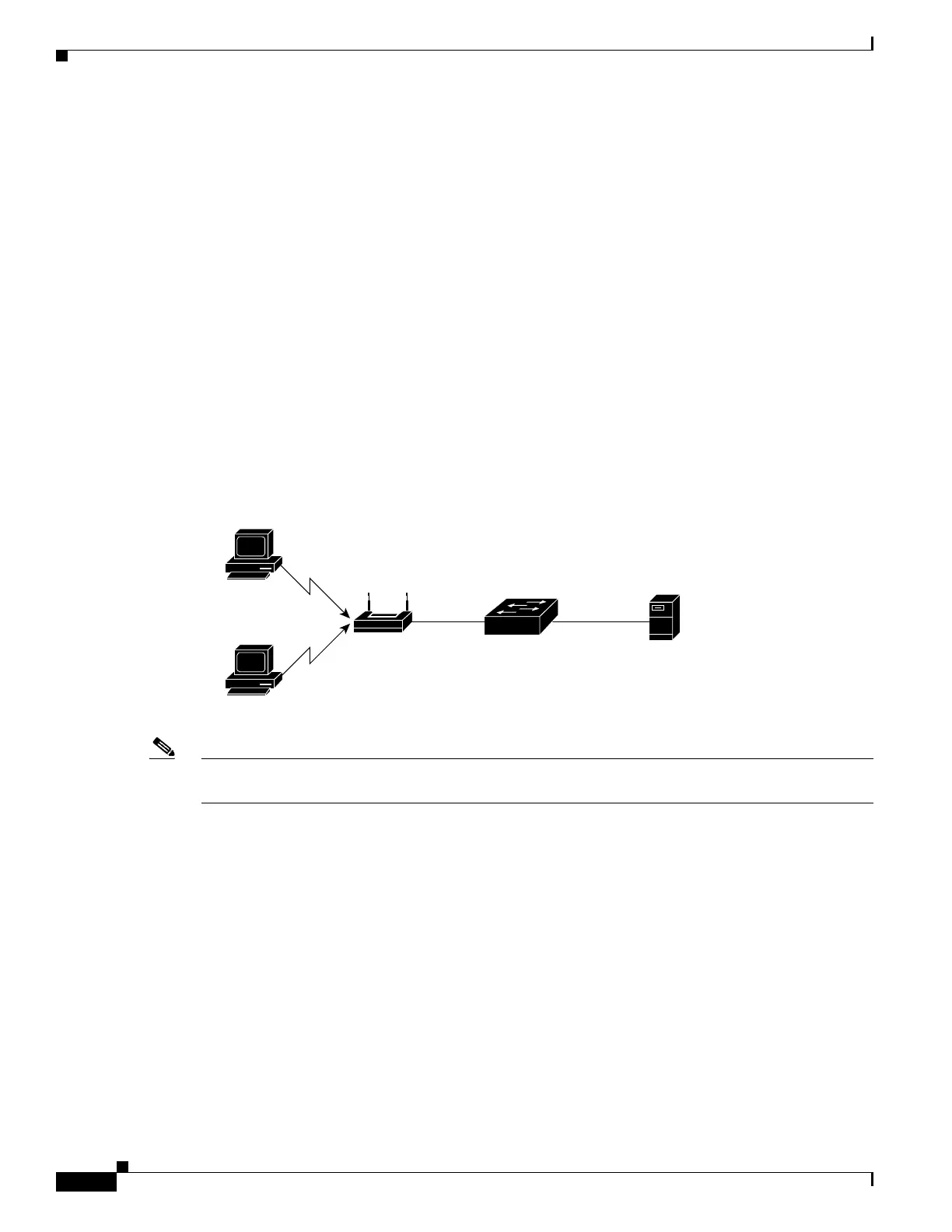
In multiple-hosts mode, you can attach multiple hosts to a single 802.1x-enabled port. Figure 1-5 on
page 1-12 shows 802.1x port-based authentication in a wireless LAN. In this mode, only one of the
attached clients must be authorized for all clients to be granted network access. If the port becomes
unauthorized (re-authentication fails or an EAPOL-logoff message is received), the switch denies
network access to all of the attached clients. In this topology, the wireless access point is responsible for
authenticating the clients attached to it, and it also acts as a client to the switch.
Figure 1-5 Multiple Host Mode Example
Note For all host modes, the line protocol stays up before authorization when port-based authentication is
configured.
802.1x Multiple Authentication Mode
Multiple-authentication (multiauth) mode allows one client on the voice VLAN and multiple
authenticated clients on the data VLAN. When a hub or access point is connected to an 802.1x-enabled
port, multiple-authentication mode provides enhanced security over multiple-hosts mode by requiring
authentication of each connected client. For non-802.1x devices, you can use MAC authentication
bypass or web authentication as the fallback method for individual host authentications to authenticate
different hosts through by different methods on a single port.
Multiple-authentication mode also supports MDA functionality on the voice VLAN by assigning
authenticated devices to either a data or voice VLAN, depending on the VSAs received from the
authentication server.
101227
Wireless clients
Access point
Authentication
server
(RADIUS)
 Loading...
Loading...











