150
Security association
A security association is an agreement negotiated between two communicating parties called IPsec
peers. It comprises a set of parameters for data protection, including security protocols,
encapsulation mode, authentication and encryption algorithms, and shared keys and their lifetime.
SAs can be set up manually or through IKE.
An SA is unidirectional. At least two SAs are needed to protect data flows in a bidirectional
communication. If two peers want to use both AH and ESP to protect data flows between them, they
construct an independent SA for each protocol.
An SA is identified by a triplet, which consists of the security parameter index (SPI), destination IP
address, and security protocol identifier (AH or ESP).
An SPI is a 32-bit number for uniquely identifying an SA. It is transmitted in the AH/ESP header. A
manually configured SA requires an SPI to be specified manually for it. An IKE-created SA will have
an SPI generated at random.
A manually configured SA never ages out. An IKE created SA has a specified period of lifetime,
which comes in two types:
• Time-based lifetime—Defines how long the SA can be valid after it is created.
• Traffic-based lifetime—Defines the maximum traffic that the SA can process.
The SA becomes invalid when either of the lifetime timers expires. Before the SA expires, IKE
negotiates a new SA, which takes over immediately after its creation.
Encapsulation modes
IPsec supports the following IP packet encapsulation modes:
• Tunnel mode—IPsec protects the entire IP packet, including both the IP header and the
payload. It uses the entire IP packet to calculate an AH or ESP header, and then encapsulates
the original IP packet and the AH or ESP header with a new IP header. If you use ESP, an ESP
trailer is also encapsulated. Tunnel mode is typically used for protecting gateway-to-gateway
communications.
• Transport mode—IPsec protects only the IP payload. It uses only the IP payload to calculate
the AH or ESP header, and inserts the calculated header between the original IP header and
payload. If you use ESP, an ESP trailer is also encapsulated. The transport mode is typically
used for protecting host-to-host or host-to-gateway communications.
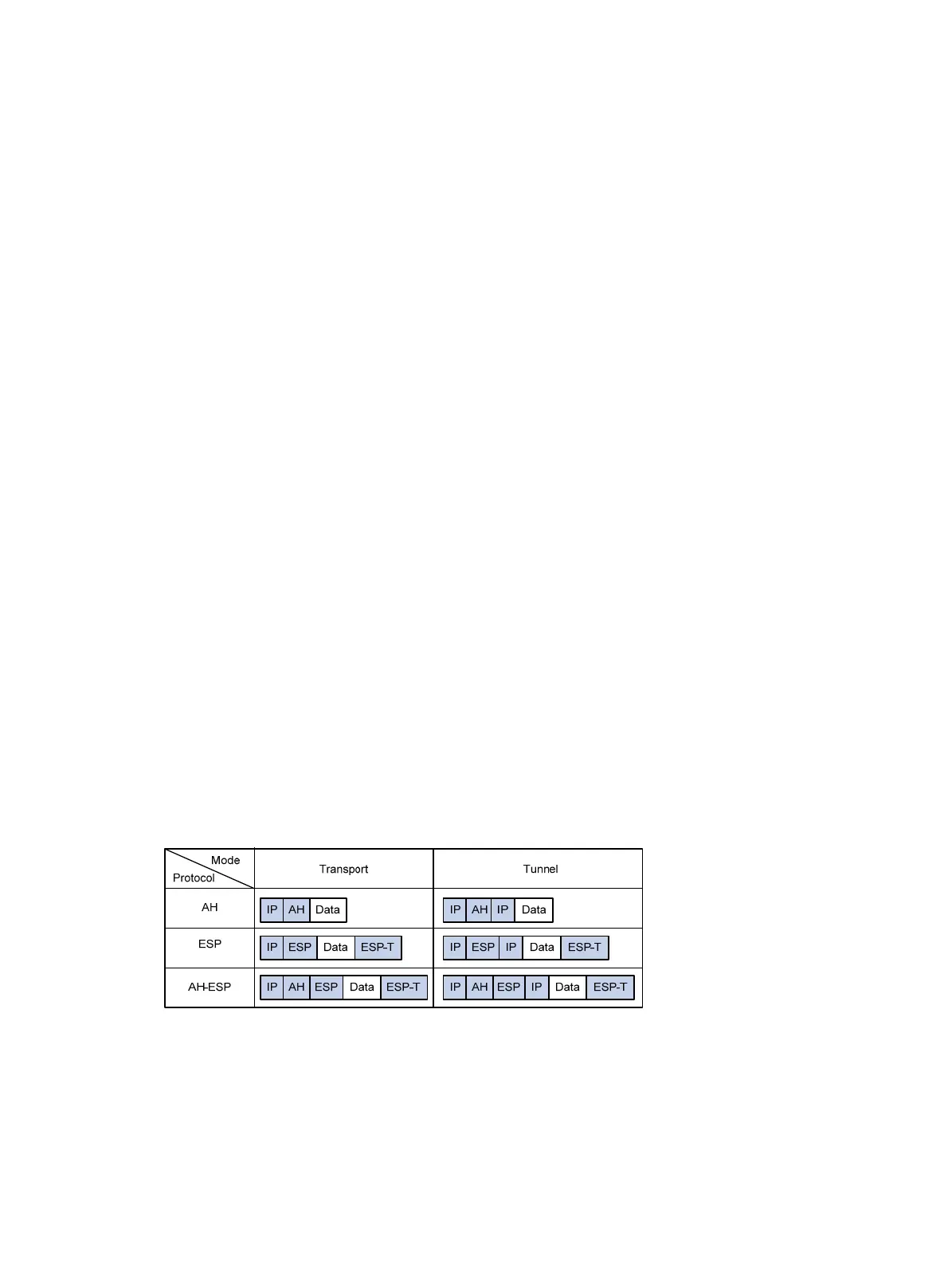
Figure 52 sh
ows how the security protocols encapsulate an IP packet in different encapsulation
modes.
Figure 52 Encapsulation by security protocols in different modes
Authentication algorithms and encryption algorithms
1. Authentication algorithms:
IPsec uses hash algorithms to perform authentication. A hash algorithm produces a
fixed-length digest for an arbitrary-length message. IPsec peers respectively calculate
message digests for each packet. If the resulting digests are identical, the packet is considered
intact.
 Loading...
Loading...




