1-7
Catalyst 3750-X and 3560-X Switch Software Configuration Guide
OL-25303-03
Chapter 1 Configuring Web-Based Authentication
Understanding Web-Based Authentication
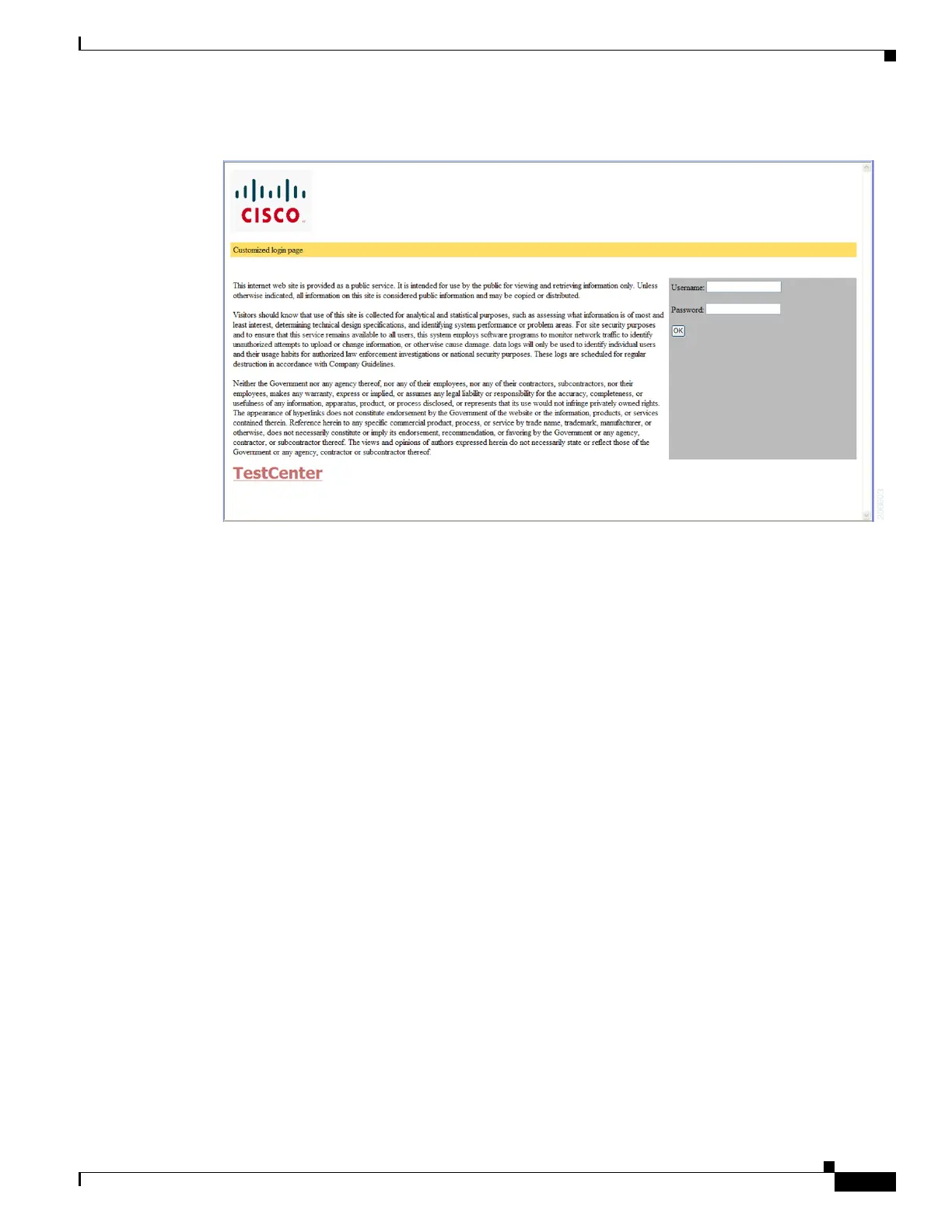
Figure 1-5 Customizeable Authentication Page
For more information, see the “Customizing the Authentication Proxy Web Pages” section on page 1-13.
Web-based Authentication Interactions with Other Features
• Port Security, page 1-7
• LAN Port IP, page 1-8
• Gateway IP, page 1-8
• ACLs, page 1-8
• Context-Based Access Control, page 1-8
• 802.1x Authentication, page 1-8
• EtherChannel, page 1-8
Port Security
You can configure web-based authentication and port security on the same port. Web-based
authentication authenticates the port, and port security manages network access for all MAC addresses,
including that of the client. You can then limit the number or group of clients that can access the network
through the port.
For more information about enabling port security, see the “Configuring Port Security” section on
page 1-8.
 Loading...
Loading...











