123
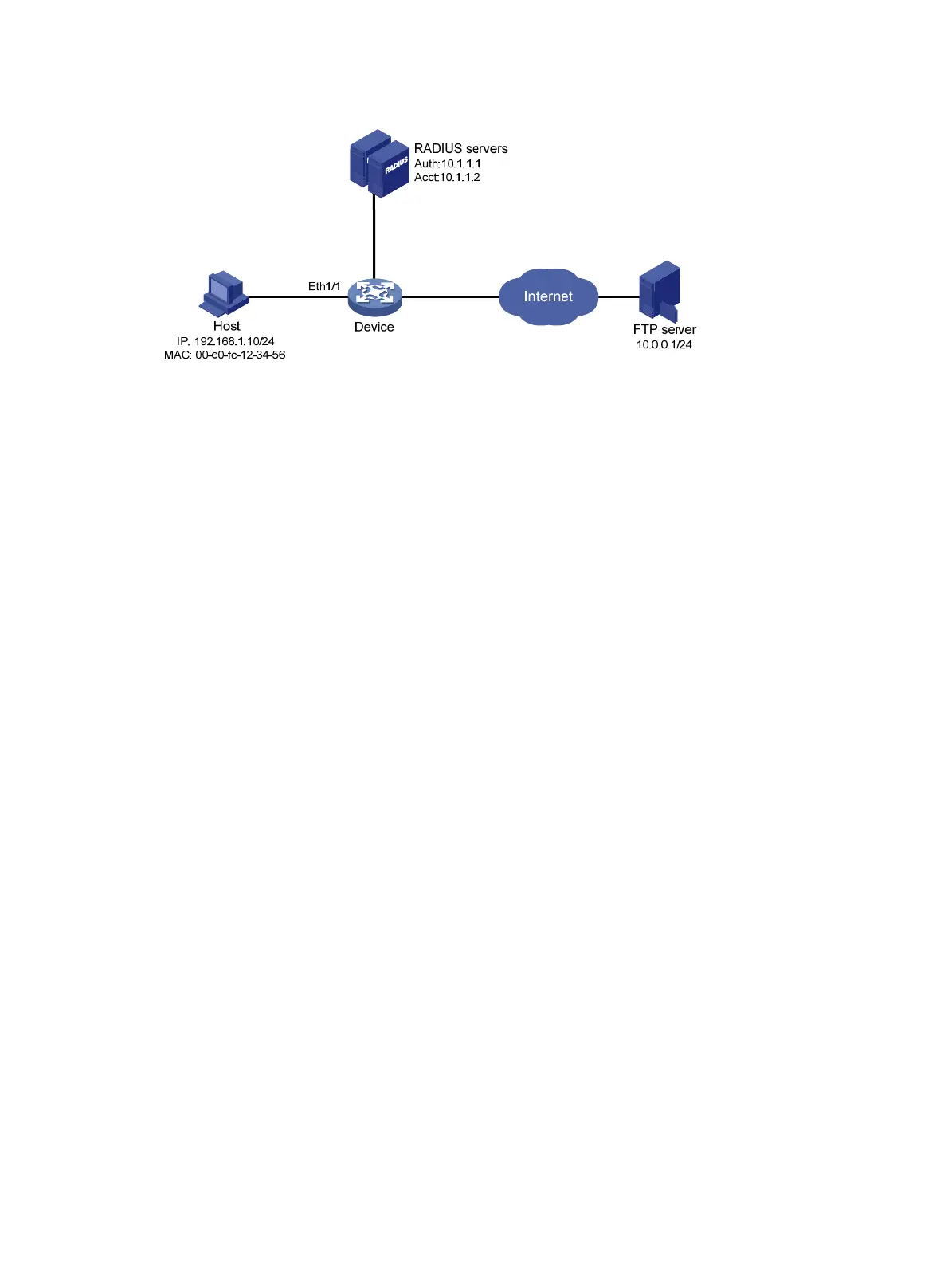
Figure 49 Network diagram
Configuration procedure
1. Make sure the RADIUS server and the access device can reach each other.
2. Configure the ACL assignment on the device:
Configure ACL 3000 to deny packets destined for 10.0.0.1.
<Sysname> system-view
[Sysname] acl number 3000
[Sysname-acl-adv-3000] rule 0 deny ip destination 10.0.0.1 0
[Sysname-acl-adv-3000] quit
3. Configure RADIUS-based MAC authentication on the device:
# Configure a RADIUS scheme.
[Sysname] radius scheme 2000
[Sysname-radius-2000] primary authentication 10.1.1.1 1812
[Sysname-radius-2000] primary accounting 10.1.1.2 1813
[Sysname-radius-2000] key authentication simple abc
[Sysname-radius-2000] key accounting simple abc
[Sysname-radius-2000] user-name-format without-domain
[Sysname-radius-2000] quit
# Apply the RADIUS scheme to an ISP domain for authentication, authorization, and
accounting.
[Sysname] domain 2000
[Sysname-isp-2000] authentication default radius-scheme 2000
[Sysname-isp-2000] authorization default radius-scheme 2000
[Sysname-isp-2000] accounting default radius-scheme 2000
[Sysname-isp-2000] quit
# Enable MAC authentication globally.
[Sysname] mac-authentication
# Specify the ISP domain for MAC authentication.
[Sysname] mac-authentication domain 2000
# Configure the device to use MAC-based user accounts, and the MAC addresses are hyphen
separated and in lowercase.
[Sysname] mac-authentication user-name-format mac-address with-hyphen lowercase
# Enable MAC authentication for port Ethernet 1/1.
[Sysname] interface ethernet 1/1
[Sysname-Ethernet1/1] mac-authentication

 Loading...
Loading...




