228
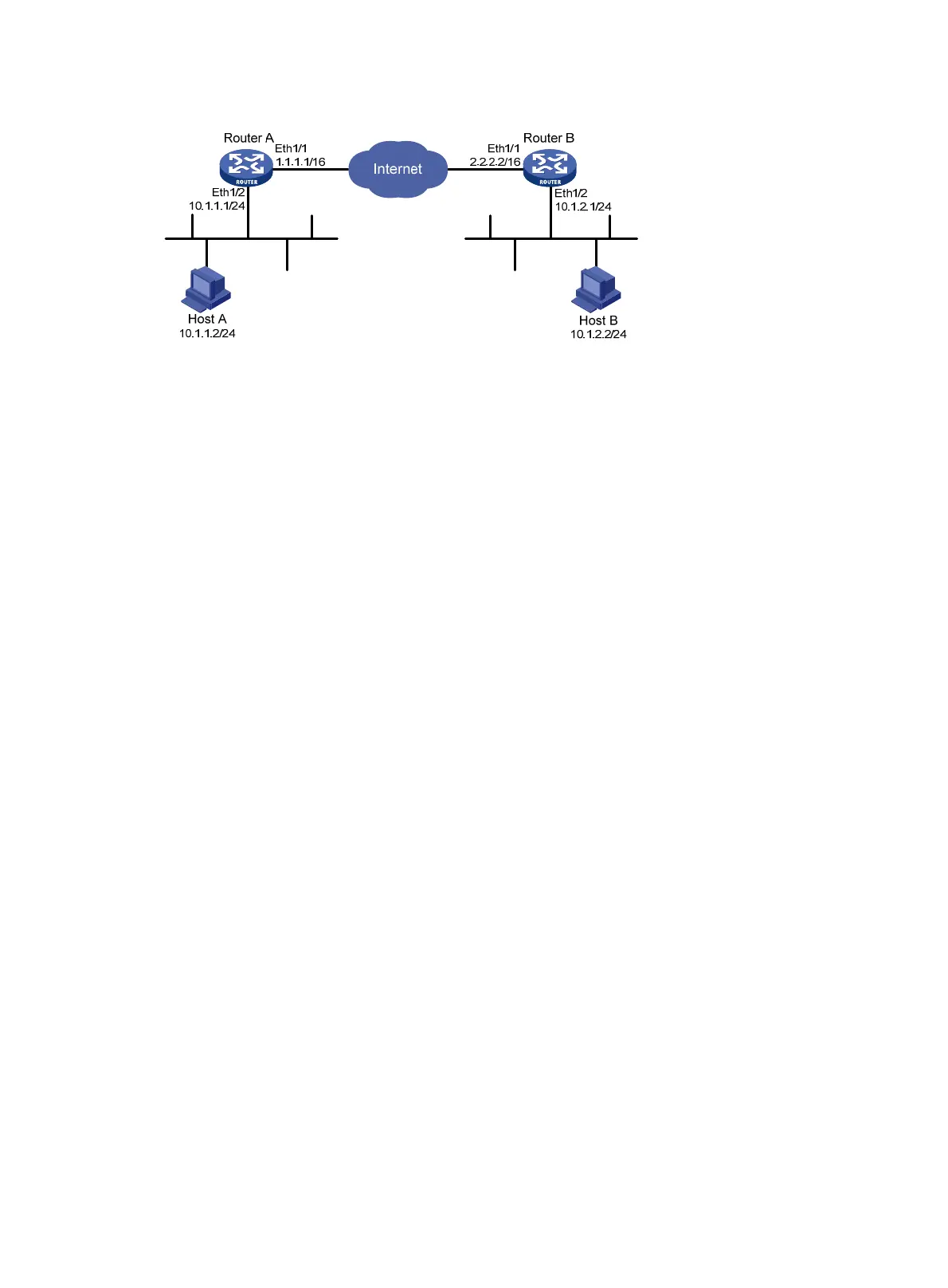
Figure 69 Network diagram
Configuration prerequisites
Make sure Router A and Router B can reach each other.
Configure the security gateway Router A
1. Configure ACL 3101 to identify traffic from subnet 10.1.1.0/24 to subnet 10.1.2.0/24.
<RouterA> system-view
[RouterA] acl number 3101
[RouterA-acl-adv-3101] rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0
0.0.0.255
[RouterA-acl-adv-3101] quit
2. Configure an IPsec transform set:
# Create IPsec transform set transform_a.
[RouterA] ipsec transform-set transform_a
# Configure the IPsec transform set to use the security protocol ESP, encryption algorithm DES,
and authentication algorithm SHA1.
[RouterA-ipsec-transform-set-transform_a] transform esp
[RouterA-ipsec-transform-set-transform_a] esp encryption-algorithm des
[RouterA-ipsec-transform-set-transform_a] esp authentication-algorithm sha1
[RouterA-ipsec-transform-set-transform_a] quit
3. Configure an IKEv2 proposal:
# Create IKEv2 proposal proposal_a.
[RouterA] ikev2 proposal proposal_a
# Configure the IKEv2 proposal to use the encryption algorithm AES-CBC-192, integrity
protection algorithm MD5, PRF algorithm MD5, and 1024-bit DH group.
[RouterA-proposal-proposal_a] encryption aes-cbc-192
[RouterA-proposal-proposal_a] integrity md5
[RouterA-proposal-proposal_a] prf md5
[RouterA-proposal-proposal_a] group 2
[RouterA-proposal-proposal_a] quit
4. Configure an IKEv2 policy:
# Create IKEv2 policy policy_a.
[RouterA] ikev2 policy policy_a
# Configure the IKEv2 policy to use IKEv2 proposal proposal_a.
[RouterA-policy-policy_a] proposal proposal_a
[RouterA-policy-policy_a] quit
5. Configure an IKEv2 keyring:

 Loading...
Loading...




