423
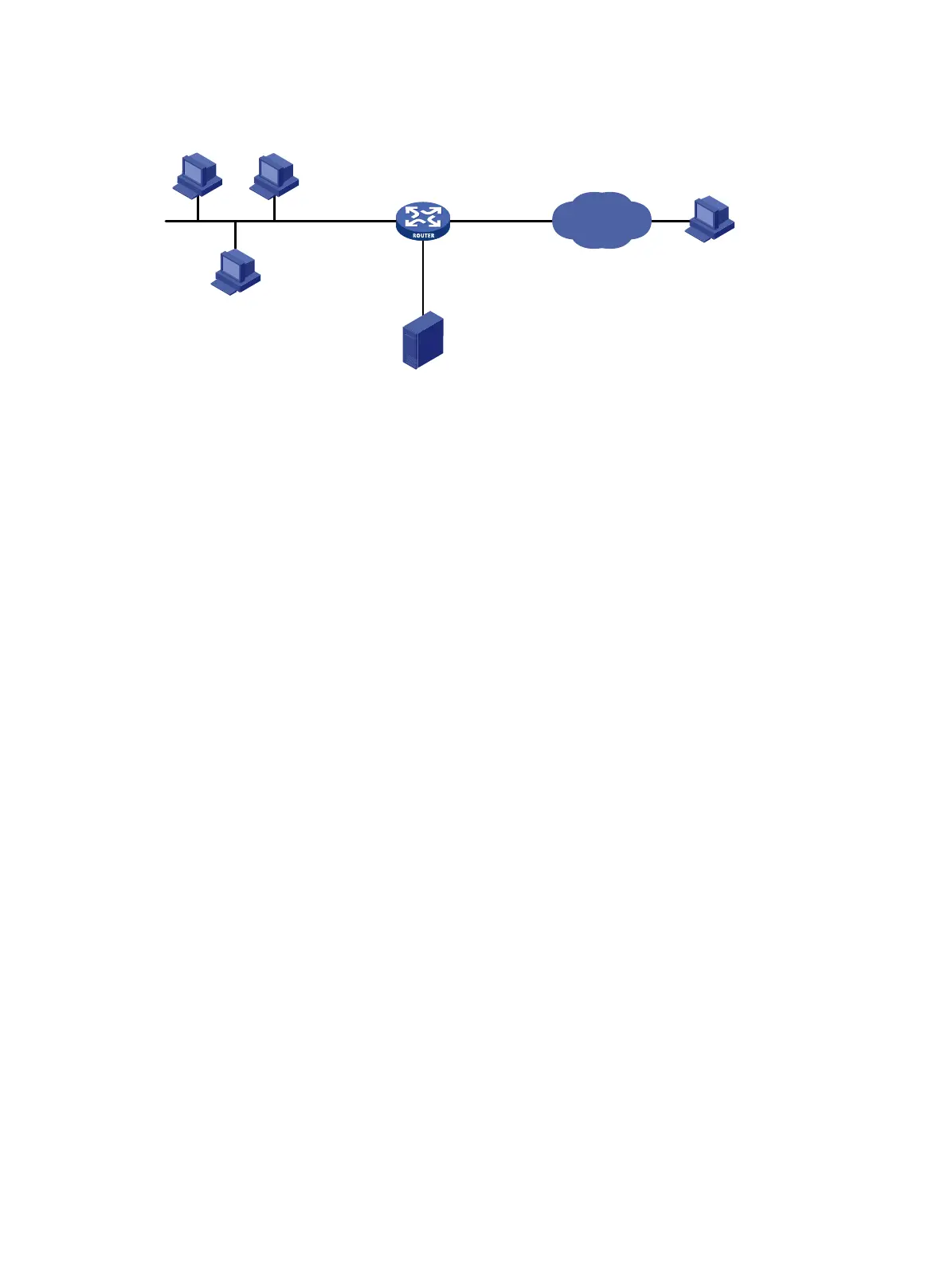
Figure 141 Network diagram
Configuration procedure
# Configure IP addresses for interfaces. (Details not shown.)
# Enable the blacklist function.
<Router> system-view
[Router] blacklist enable
# Create attack protection policy 1.
[Router] attack-defense policy 1
# Enable Smurf attack protection.
[Router-attack-defense-policy-1] signature-detect smurf enable
# Enable scanning attack protection
[Router-attack-defense-policy-1] defense scan enable
# Set the connection rate threshold that triggers scanning attack protection to 4500 connections per
second.
[Router-attack-defense-policy-1] defense scan max-rate 4500
# Enable the blacklist function for scanning attack protection.
[Router-attack-defense-policy-1] defense scan add-to-blacklist
[Router-attack-defense-policy-1] quit
# Apply policy 1 to GigabitEthernet 1/2.
[Router] interface gigabitethernet 1/2
[Router-GigabitEthernet1/2] attack-defense apply policy 1
[Router-GigabitEthernet1/2] quit
# Create attack protection policy 2.
[Router] attack-defense policy 2
# Enable SYN flood attack protection.
[Router-attack-defense-policy-2] defense syn-flood enable
# Configure SYN flood attack protection for the internal server 10.1.1.2 and set the action threshold
to 5000 and silence threshold to 1000.
[Router-attack-defense-policy-2] defense syn-flood ip 10.1.1.2 rate-threshold high 5000
low 1000
# Configure the policy to drop the subsequent packets after a SYN flood attack is detected.
[Router-attack-defense-policy-2] defense syn-flood action drop-packet
Internet
Router
Server
Host C
GE1/2GE1/1
GE1/3
Host A Host B
Attacker
Host D
5.5.5.5/24
202.1.0.1/16192.168.1.1/16
10.1.1.2/24
10.1.1.1/24
 Loading...
Loading...




