Chapter 7: Encryption Key Management
Scalar Key Manager Functions Available on the Library
Quantum Scalar i40 and Scalar i80 User’s Guide 195
Data encryption keys are generated. The library triggers the SKM
server to generate a set of unique data encryption keys. This takes
15 minutes to an hour or longer, depending on network
performance. The library notifies you when the process is complete.
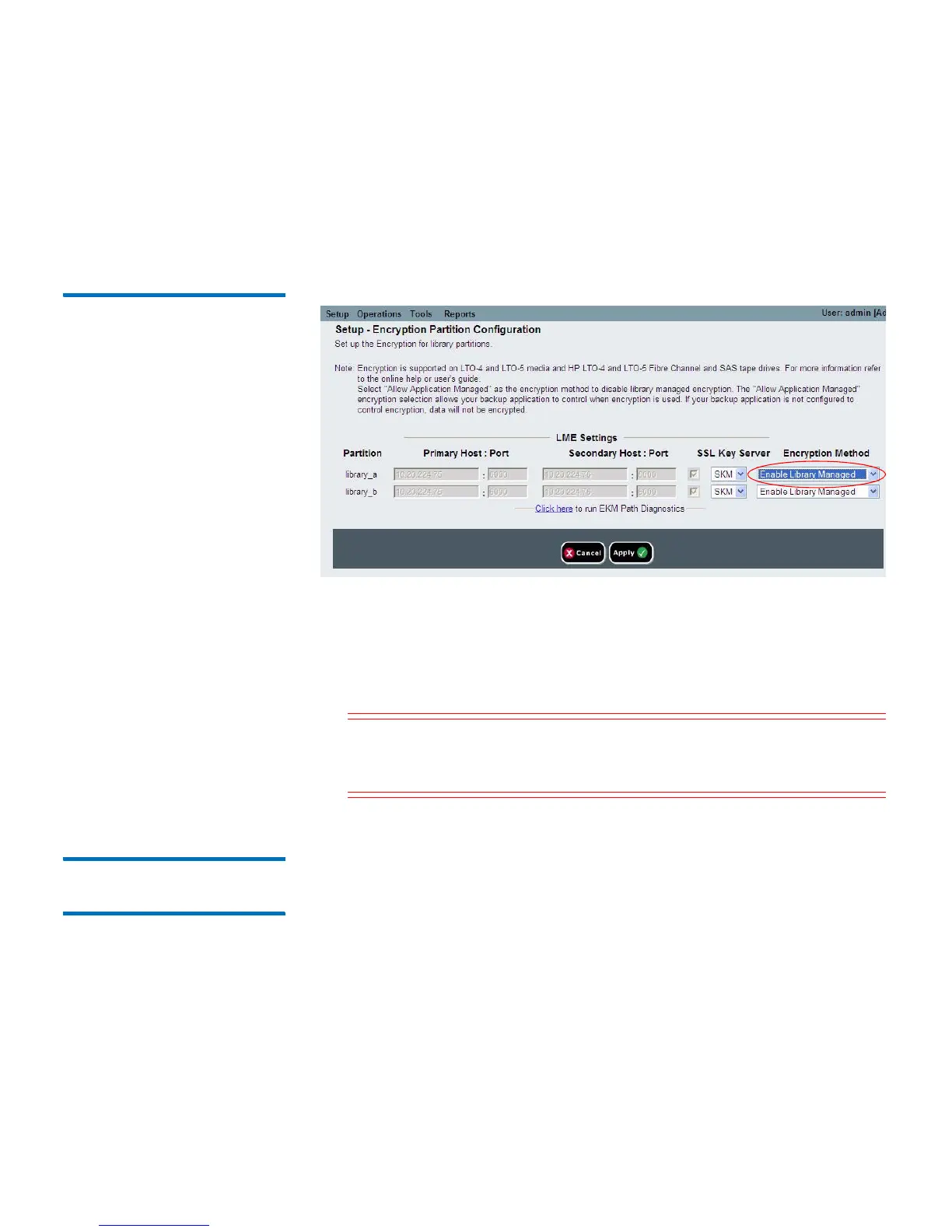
Figure 37 Changing
Encryption Method Back to
Enable Library Managed
8 Wait for the process to complete before resuming library
operations.
9 Back up
both SKM server keystores. See the
Scalar Key Manager
User’s Guide
for instructions on backing up the keystores.
Caution: You must back up the keystores every time you
generate new data encryption keys to protect against
catastrophic server failure.
Sharing Encrypted Tape
Cartridges
If you are using SKM, you can share encrypted tapes with other
companies and individuals who also use SKM for managing encryption
keys.

 Loading...
Loading...