To validate the identity of a received server certificate, the phone verifies the following:
• The certificate chain up to the trusted certificate authority in TRUSRCERTS
• The Signature
• The Revocation status through OCSP if OCSP_ENABLED is set to 1
• Certificate validity based on the current date and not-before and not-after attributes of the
certificate.
• Certificate usage restrictions.
• The Identity of the server certificate that is used to connect to the server. This is optional and
depends on the value of TLSSRVRID.
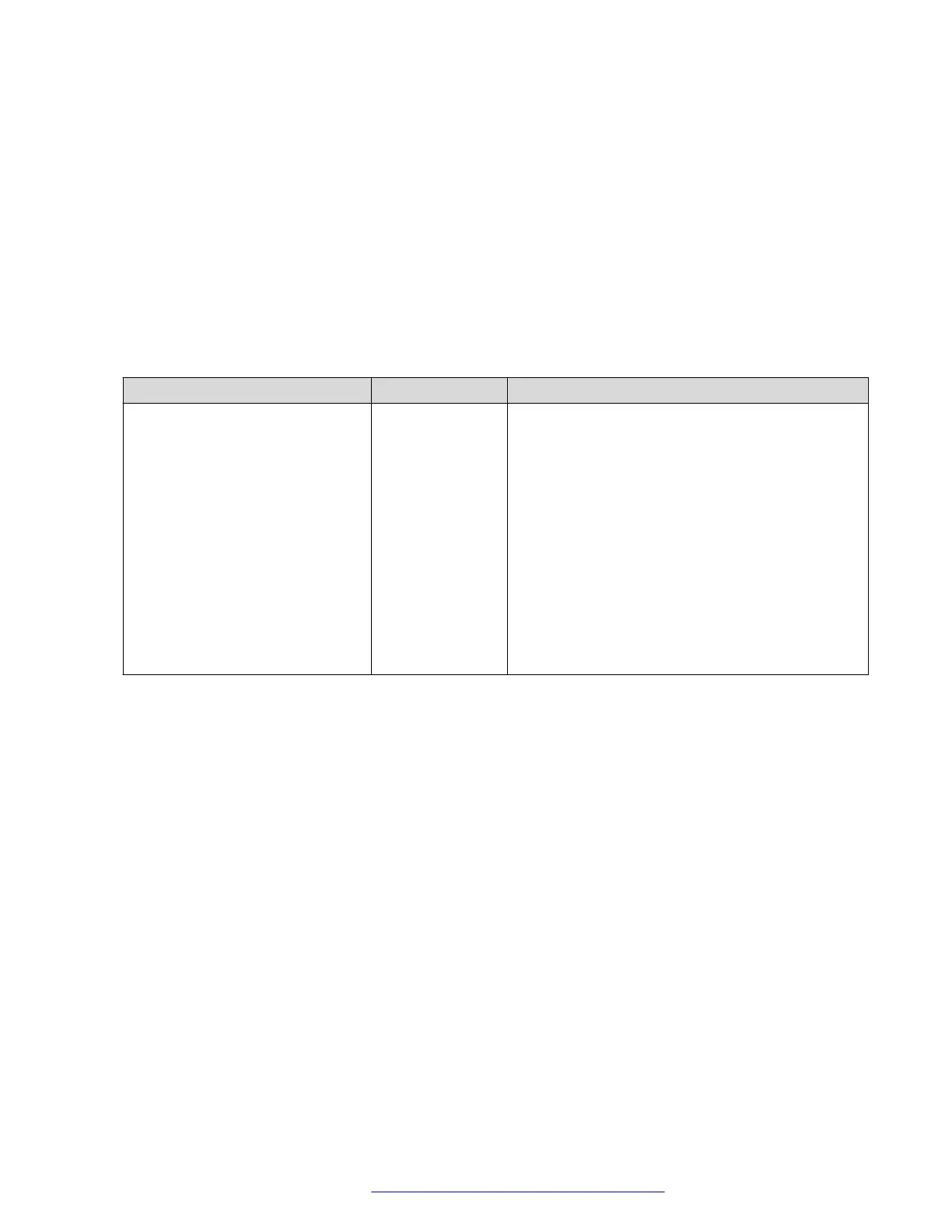
The following configuration parameter can be used in this context when applicable:
Parameter name Default value Description
TLSSRVRID 1 Specifies how a phone evaluates a certificate
trust .
The options are:
• 0: Identity matching is not performed.
• 1: The certificate is trusted only if the identity
used to connect to the server matches the
certificate identity, as per Section 3.1 of RFC
2818. For SIP-TLS connections, an additional
check is performed to validate the SIP domain
identified in the certificate, as per RFC 5922.
The parameter is configured through the
46xxsettings.txt.
Server certificate identity validation is only performed when TLSSRVRID is set to 1. When it is
enabled, the phone verifies the identity contained in the server certificate. The TLS connection
fails if any aspect of identity validation fails.
All TLS connections, that is, SIP-TLS and HTTPS-TLS, verify that the identity is contained in the
server certificate. The server identity that is used for verification is the address that is used to
connect to the server. This might be one of the following:
• IPv4 adress. For example, 192.168.1.2
• IPv6 address. For example, 2001:db8::2:1
• FQDN. For example, hostname.domain.com
This identity must match an identity found in the certificate. The matching is case insensitive. The
phone first checks for the server identity in the Subject Alternative Name (SAN). If it cannot be
found in the SAN, then the phone checks the certificate common name (CN). This validation is
based on RFC 2818.
The phone checks for an IP address server identity match with the following in the specified order
until a match is found:
1. Field of type IP address in the SAN extension
Security
December 2018 Installing and Administering Avaya J100 Series IP Phones 140
Comments on this document? infodev@avaya.com

 Loading...
Loading...