DMD1050TS Satellite Modem Board
Revision 1
Theory of Operation 3–41 MN-DMD1050TS
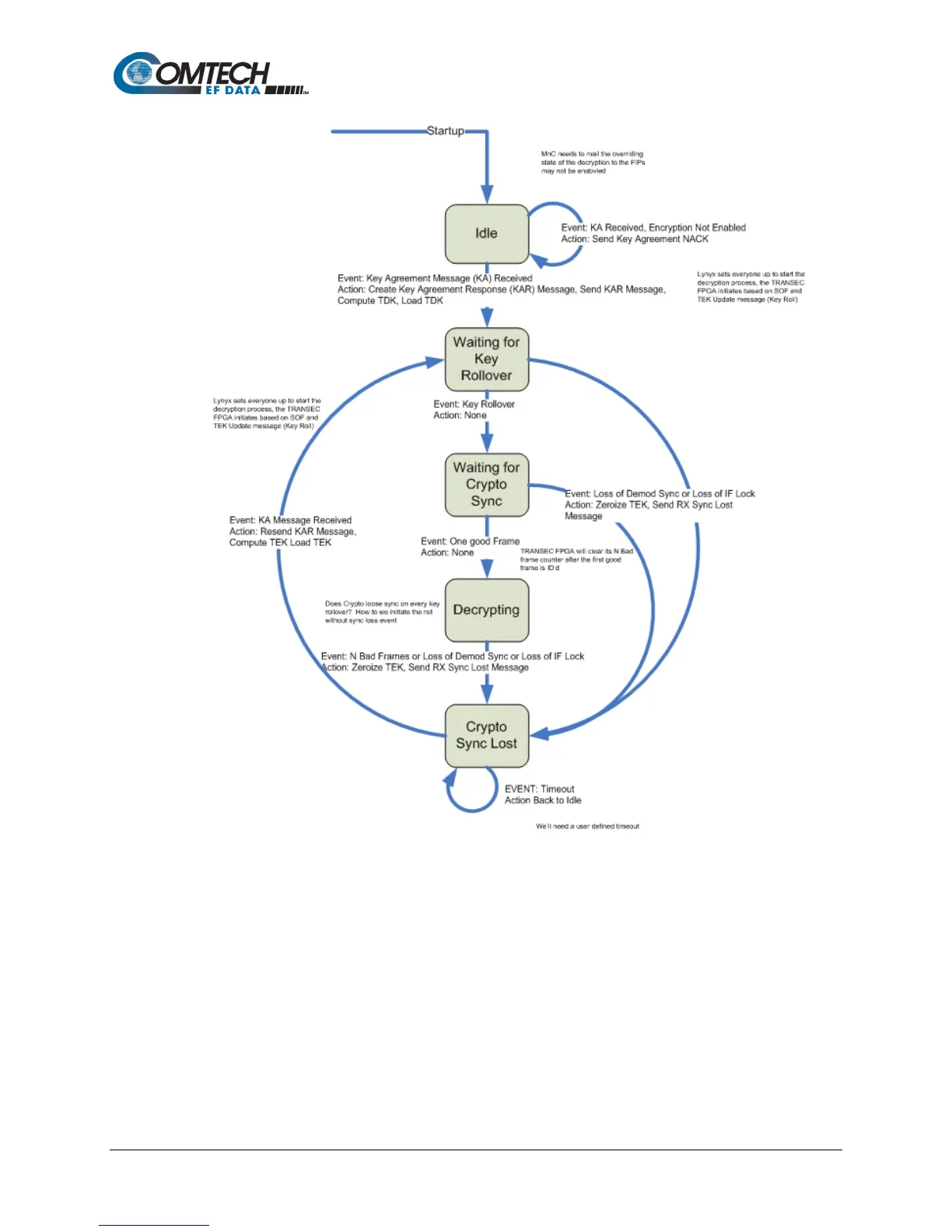
Figure 3-14. Traffic Decryption Key Negotiation
3.20.1.2 Key Agreement Algorithm
The key agreement algorithm used to negotiate a shared secret is the Ephemeral Unified Model,
Elliptic Curve Cryptography Cofactor Diffie-Hellman C(2,0,ECC CDH) as specified in the elliptic
curve parameters section of NIST SP 800-56A(3).
3.20.1.2.1 Key Derivation
Once the shared secret has been negotiated, the TEK is generated from the shared secret using
the Concatenation Key Derivation Function (KDF), as specified in NIST SP 800-56A, Section
5.8.1(3). All hashing algorithms use SHA-512, as defined in FIPS 180-2(4).

 Loading...
Loading...