Securing Access to Management Functions
December 2000 3 - 37
Foundry’s Vendor-ID is 1991, with Vendor-Type 1. The following table describes the Foundry vendor-specific
attributes.
Identifying the RADIUS Server to the Foundry Device
To use a RADIUS server to authenticate access to a Foundry device, you must identify the server to the Foundry
device. For example:
BigIron(config)# radius-server host 209.157.22.99
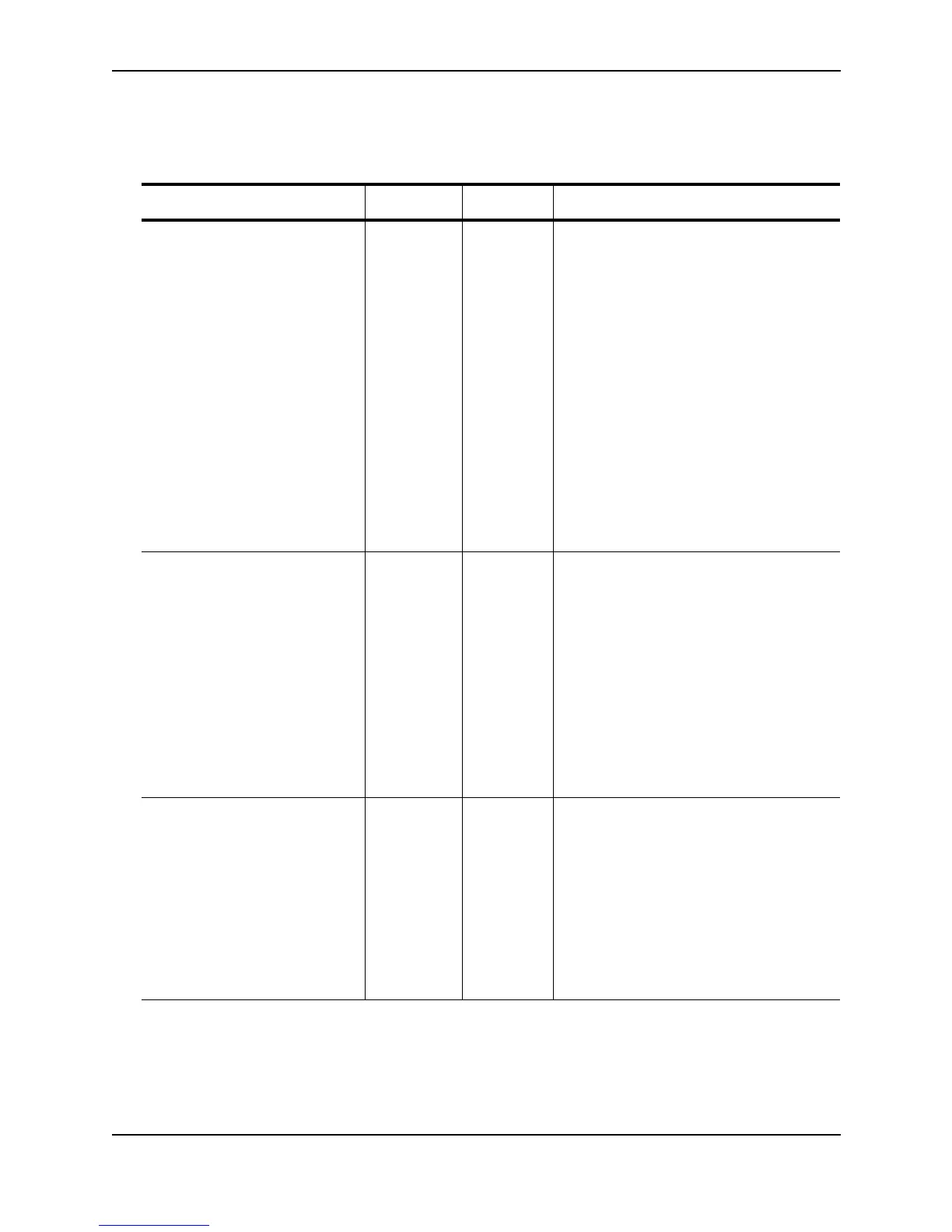
Table 3.4: Foundry vendor-specific attributes for RADIUS
Attribute Name Attribute ID Data Type Description
foundry-privilege-level 1 integer Specifies the privilege level for the user.
This attribute can be set to one of the
following:
0 Super User level – Allows complete
read-and-write access to the system.
This is generally for system
administrators and is the only
management privilege level that
allows you to configure passwords.
4 Port Configuration level – Allows read-
and-write access for specific ports but
not for global (system-wide)
parameters.
5 Read Only level – Allows access to
the Privileged EXEC mode and
CONFIG mode of the CLI but only
with read access.
foundry-command-string 2 string Specifies a list of CLI commands that are
permitted or denied to the user when
RADIUS authorization is configured.
The commands are delimited by semi-
colons (;). You can specify an asterisk (*)
as a wildcard at the end of a command
string.
For example, the following command list
specifies all show and debug ip
commands, as well as the write terminal
command:
show *; debug ip *; write term*
foundry-command-exception-flag 3 integer Specifies whether the commands indicated
by the foundry-command-string attribute
are permitted or denied to the user. This
attribute can be set to one of the following:
0 Permit execution of the commands
indicated by foundry-command-string,
deny all other commands.
1 Deny execution of the commands
indicated by foundry-command-string,
permit all other commands.
 Loading...
Loading...