Foundry Switch and Router Installation and Configuration Guide
C - 22 December 2000
must add all the policies to the group at one time. You cannot edit policy groups later. To change a policy group,
you must delete the group and then add a new group.
Policies within the group are applied in positional order from left to right. Make sure you specify the filters in the
order you want the device to apply them.
Syntax
Use the following CLI commands or Web management interface panels to configure TCP/UDP access policies.
Cache Server Redirection Policies
Cache server redirection polices apply only to a ServerIron configured for Transparent Cache Switching (TCS).
You configure the redirection policies to enable TCS.
Actions
A cache server redirection policy either redirects HTTP traffic to a cache server (permits) or sends the traffic to the
Internet (denies).
Scope
You can enable TCS globally or you can enable it locally, on specific ports. If you enable TCS locally, make sure
you enable TCS on the ports that are connected to the Internet. Enable TCS for outbound traffic.
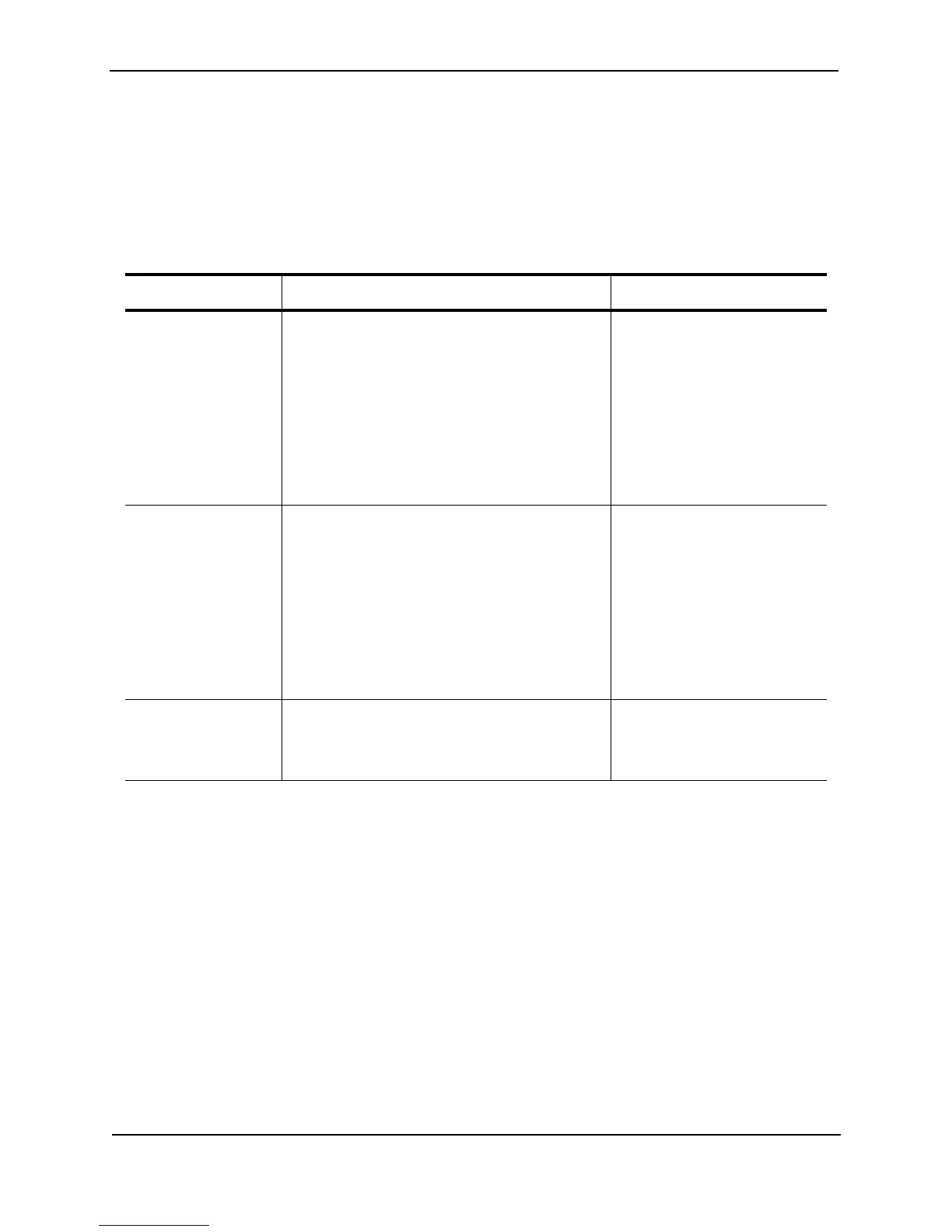
Table C.8: TCP/UDP Access Policies
Foundry Product CLI syntax Web management links
NetIron Internet
Backbone router,
BigIron, FastIron II,
TurboIron/8
BigIron(config)# ip access-policy <policy-num>
permit | deny <ip-addr> <ip-mask> | any
<ip-addr> <ip-mask> | any tcp | udp
[<operator> [<tcp/udp-port-num>]] [log]
BigIron(config-if-1/1)# ip access-policy-group in |
out <policy-list>
FastIronII(config) ip policy <policy-num> permit |
deny tcp | udp <tcp/udp-port-num> global | local
FastIronII(config-if-1/1) ip-policy <num>
Configure->IP->Access Policy
FastIron Workgroup,
FastIron Backbone,
TurboIron, NetIron
NetIron(config)# ip access-policy <policy-num>
permit | deny <ip-addr> <ip-mask> | any
<ip-addr> <ip-mask> | any tcp | udp
[<operator> [<tcp/udp-port-num>]] [log]
NetIron(config-if-1)# ip access-policy-group in |
out <policy-list>
FastIron(config)# ip policy <num> priority high |
normal tcp | udp <tcp/udp-port-num> global | local
FastIron(config-if-1)# ip-policy <num>
Configure->IP->Access Policy
ServerIron ServerIron(config)# ip filter <filter-num> permit |
deny <IP-addr> <ip-mask> | any
<IP-addr> <ip-mask> | any [icmp | tcp | udp |
<num>] [<operator>] [<tcp/udp-port-num>]
Configure->IP->Access Policy
 Loading...
Loading...