18
hmac-sha-384 | hmac-sha-512 |
md5 } { cipher | simple } string [ acl
ipv4-acl-number | ipv6 acl
ipv6-acl-number ] *
4.
trusted key.
ntp-service reliable authentication-keyid
keyid
By default, no
configured as a trusted key.
NTP authentication results differ when different configurations are performed on client and server.
For more information, see Table 2. (N/A in the table means that whether the configuration is
performed does not make any difference.)
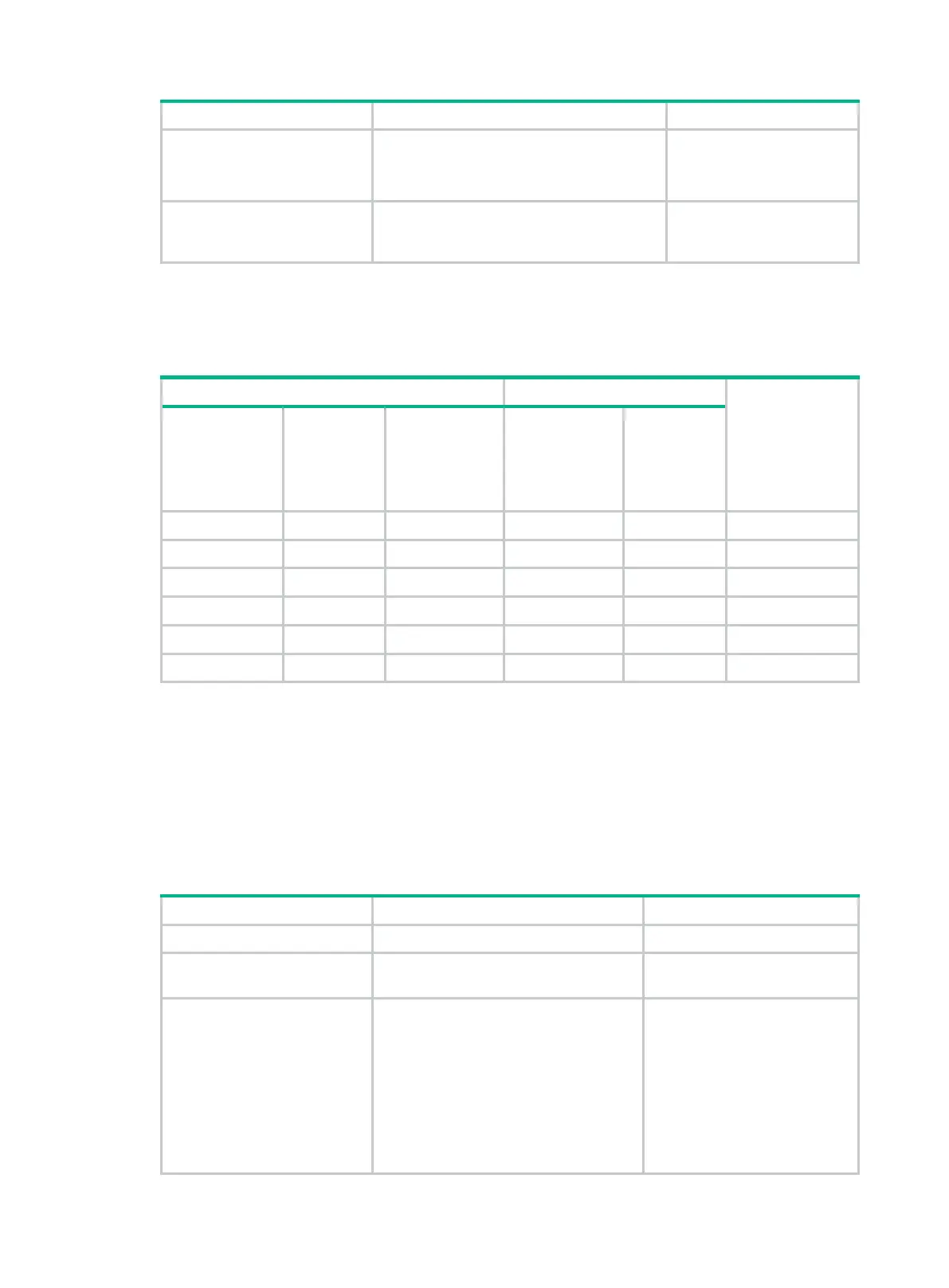
Table 2 NTP authentication results
Authentication
result
authenticatio
n
Configure
configure
Associate
server
authenticatio
n
Configure
configure
Yes Yes Yes Yes Yes Succeeded
Yes Yes Yes Yes No Failed
Yes Yes Yes No N/A Failed
Yes No Yes N/A N/A Failed
Yes N/A No N/A N/A No authentication
No N/A N/A N/A N/A No authentication
Configuring NTP authentication in symmetric active/passive
mode
To ensure a successful NTP authentication, configure the same authentication key ID, algorithm, and
key on the active peer and passive peer. Make sure the peer device is allowed to use the key ID for
authentication on the local device.
To configure NTP authentication for an active peer:
1. Enter system view.
system-view
N/A
2.
authentication.
ntp-service authentication enable
By default, NTP authentication
is disabled.
3.
authentication key.
• Release 1111:
ntp-service authentication-keyid
keyid authentication-mode md5
{ cipher | simple } value
• Release 1121 and later:
ntp-service authentication-keyid
keyid authentication-mode
{ hmac-sha-1 | hmac-sha-256 |
hmac-sha-384 | hmac-sha-512 |
md5 } { cipher | simple } string
By default, n
authentication key is
configured.

 Loading...
Loading...



















