4.4.12 Security Configuration
In this section, several Layer 2 security mechanisms are provided to increase the security level of
your Managed Switch. Layer 2 attacks are typically launched by or from a device that is physically
connected to the network. For example, it could be a device that you trust but has been taken over
by an attacker. By default, most security functions available in this Managed Switch are turned off,
to prevent your network from malicious attacks, it is extremely important for you to set up
appropriate security configurations. This section provides several security mechanisms to protect
your network from unauthorized access to a network or redirect traffic for malicious purposes,
such as Source IP Spoofing and ARP Spoofing.
Select the folder Security Configuration from the Switch Management menu and then eight
options within this folder will be displayed
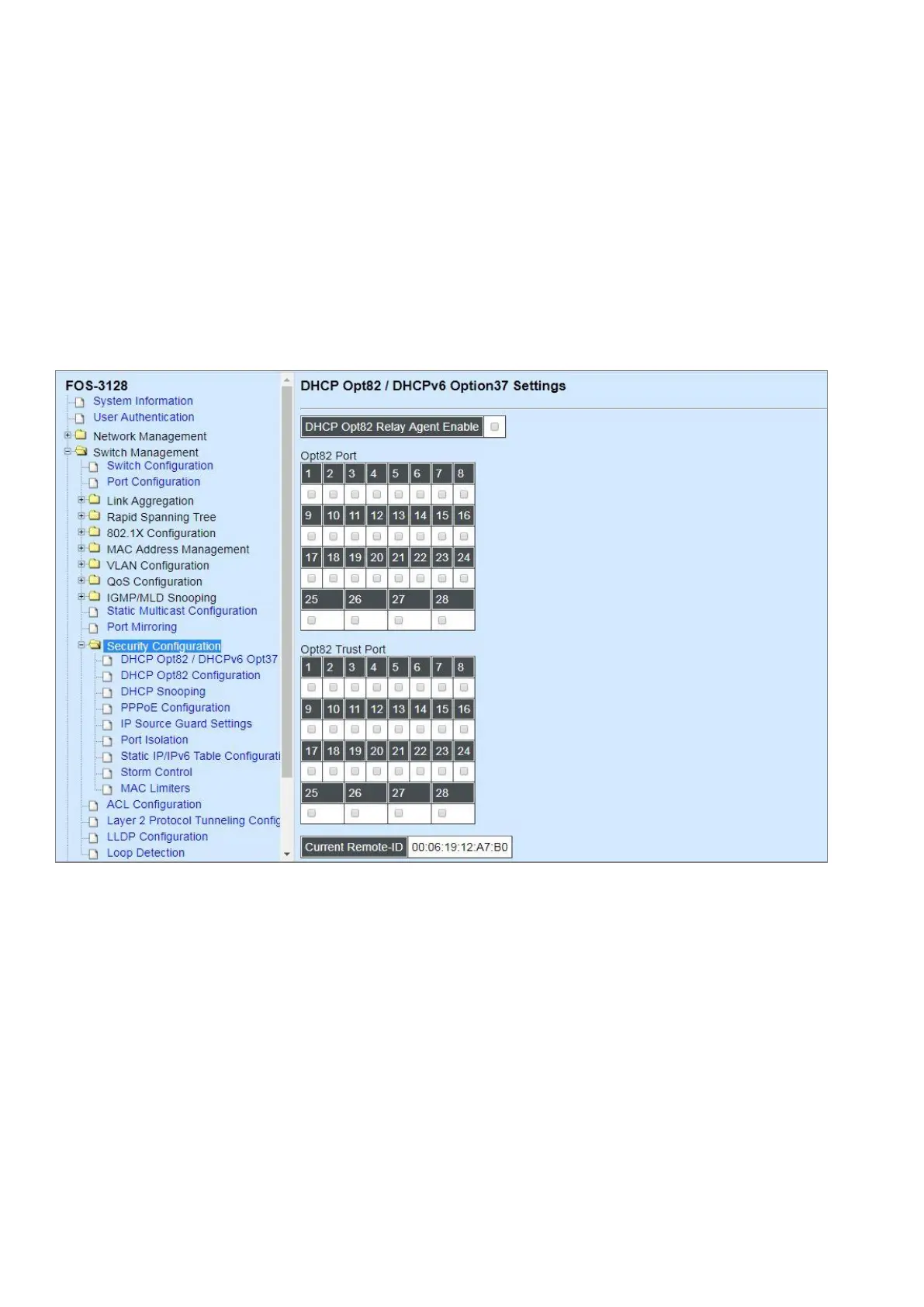
1. DHCP Opt82/DHCPv6 Opt37 Settings: To enable or disable DHCP Option 82 (for DHCPv4)
and Option 37 (for DHCPv6) relay agent global setting and show each port’s configuration.
2. DHCP Opt82 Configuration: Set up suboptions such as Circuit-ID and Remote-ID.
3. DHCP Snooping: Customer port filtering setting.
4. PPPoE Configuration: Set up the PPPoE-IA trust port(s) for security.
5. IP Source Guard Settings: Customer port DHCP snooping setting.
6. Port Isolation: Set up port’s communication availability that they can only communicate with a
given "uplink"

 Loading...
Loading...