S350 Series 24-Port (PoE+) and 48-Port Gigabit Ethernet Smart Managed Pro Switches
Configuration Examples User Manual348
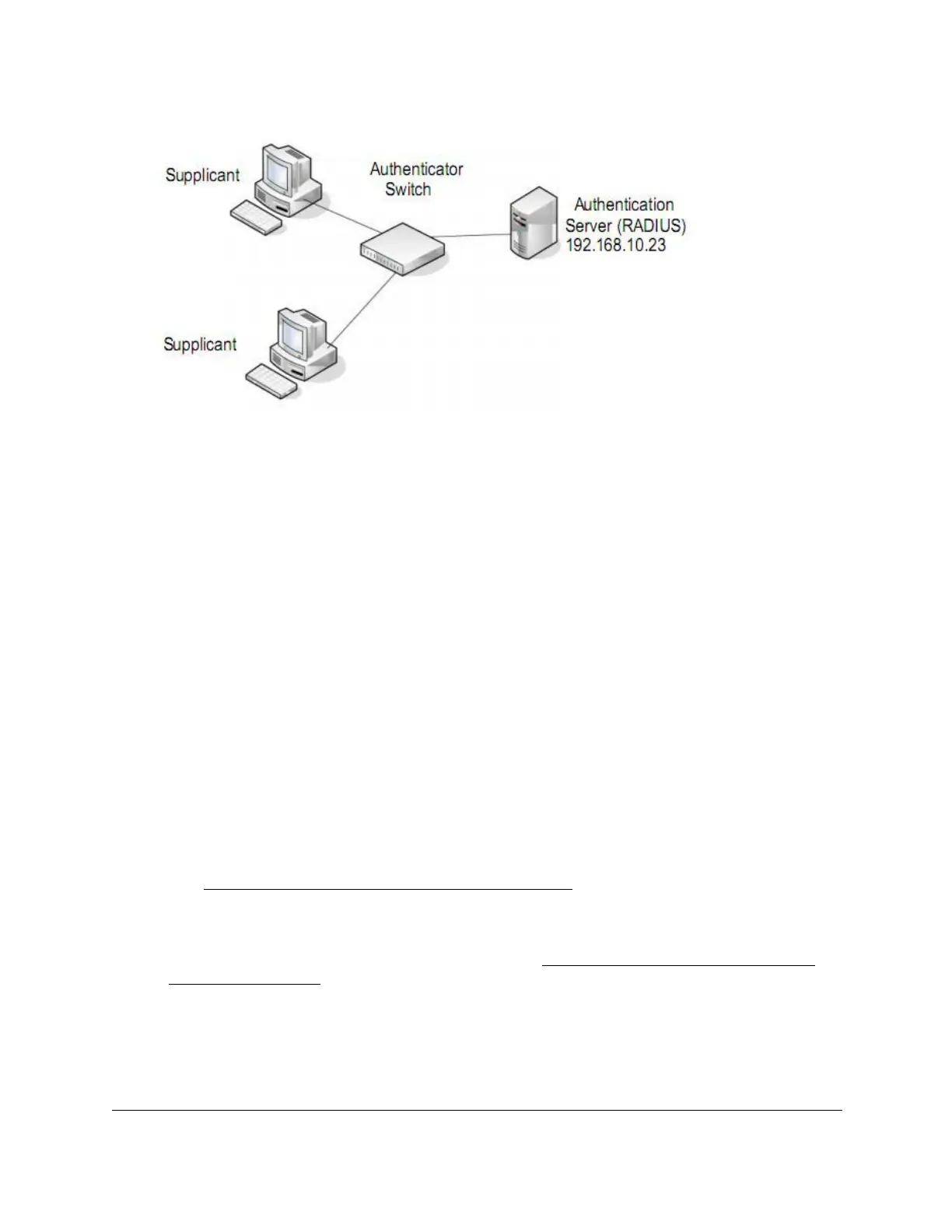
Figure 1. 802.1X authentication roles
802.1X Example Configuration
This example shows how to configure the switch so that 802.1X-based authentication is
required on the ports in a corporate conference room (1/0/5–1/0/8). These ports are available
to visitors and must be authenticated before access is granted to the network. The
authentication is handled by an external RADIUS server. When the visitor is successfully
authenticated, traffic is automatically assigned to the guest VLAN. This example assumes
that a VLAN was configured with a VLAN ID of 150 and VLAN name of Guest.
1. On the Port
Authentication page, select ports 1/0/5, 1/0/6
, 1/0/7, and 1/0/8.
2. From the Port Control menu, select Unauthorized.
The selection from the Port Control menu for all other ports on which authentication is
not needed must be Authorized. When the selection from the Port Control menu is
Authorized, the port is unconditionally put in a force-authorized state and does not
require any authentication. When the selection from the Port Control menu is Auto, the
authenticator PAE sets the controlled port mode.
3. In the Guest VLAN
field for ports 1/0/5–1/0/8, enter 150 to assign these ports to the guest
VLAN.
You can configure additional settings to control access to the network through the ports.
See
Configure a Port Security Interface on page 257 for information about the settings.
4. Click the Apply button.
5. On the 802.1X Configuration page, set the port based authentication state and guest VLAN
mode to Enable, and then the Apply button. (See
Configure the Global Port Security
Mode on page 256.)
This example uses the default values for the port authentication settings, but you can
configure several additional settings. For example, the EAPOL Flood Mode field allows
you to enable the forwarding of EAPoL frames when 802.1X is disabled on the device.

 Loading...
Loading...