Security Features
329
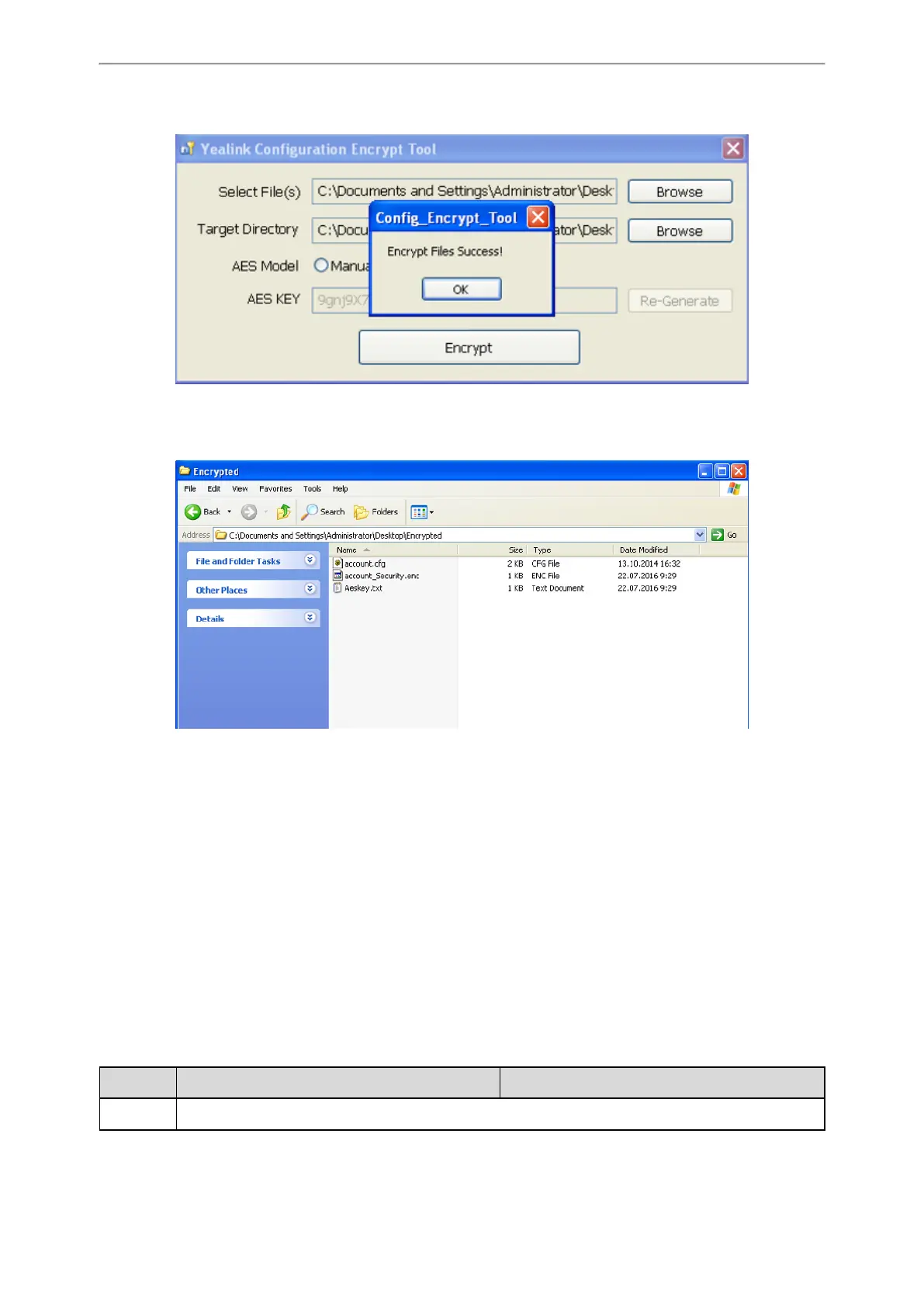
6. Click Encrypt to encrypt the configuration file(s).
7. Click OK.
The target directory will be automatically opened. You can find the encrypted CFG file(s), encrypted key file(s) and
an Aeskey.txt file storing plaintext AES key(s).
Incoming Network Signaling Validation
Yealink phones support the following three optional levels of security for validating incoming network signaling:
l Source IP address validation: ensure the request is received from an IP address of a server belonging to the set of
target SIP servers.
l Digest authentication: challenge requests with digest authentication using the local credentials for the associated
registered account.
l Source IP address validation and digest authentication: apply both of the above methods.
Topic
Incoming Network Signaling Validation Configuration
Incoming Network Signaling Validation Configuration
The following table lists the parameters you can use to configure the incoming network signaling validation.
Parameter sip.request_validation.source.list <y0000000000xx>.cfg
Description It configures the name of the request method for which source IP address validation will be applied.

 Loading...
Loading...