22. MyIC Phone VHE
22.1 Architecture
22.1.1 Software description
- IctIM : Instant Messaging
- WSManager : access to OpenTouch web services
- Telephony : Call management and SIP NOTIFY event from OpenTouch
- IctDirectory : Local contact management and UDA
- Comlog : call log and Voice mail box messages
- IctUser : Manager/assistant + lock/unlock
22.2 Log setting
To trace the interchange between OpenTouch and MyIC Phone refer to the wireshark chapter
To collect MyIC Phone logs refer to TG0065
To access to MyIC Phone use SSH, account admin / password deifine in 8770 device/advanced security /
SSH activation and password for SSH
The debug set command are located in /var/run/debug
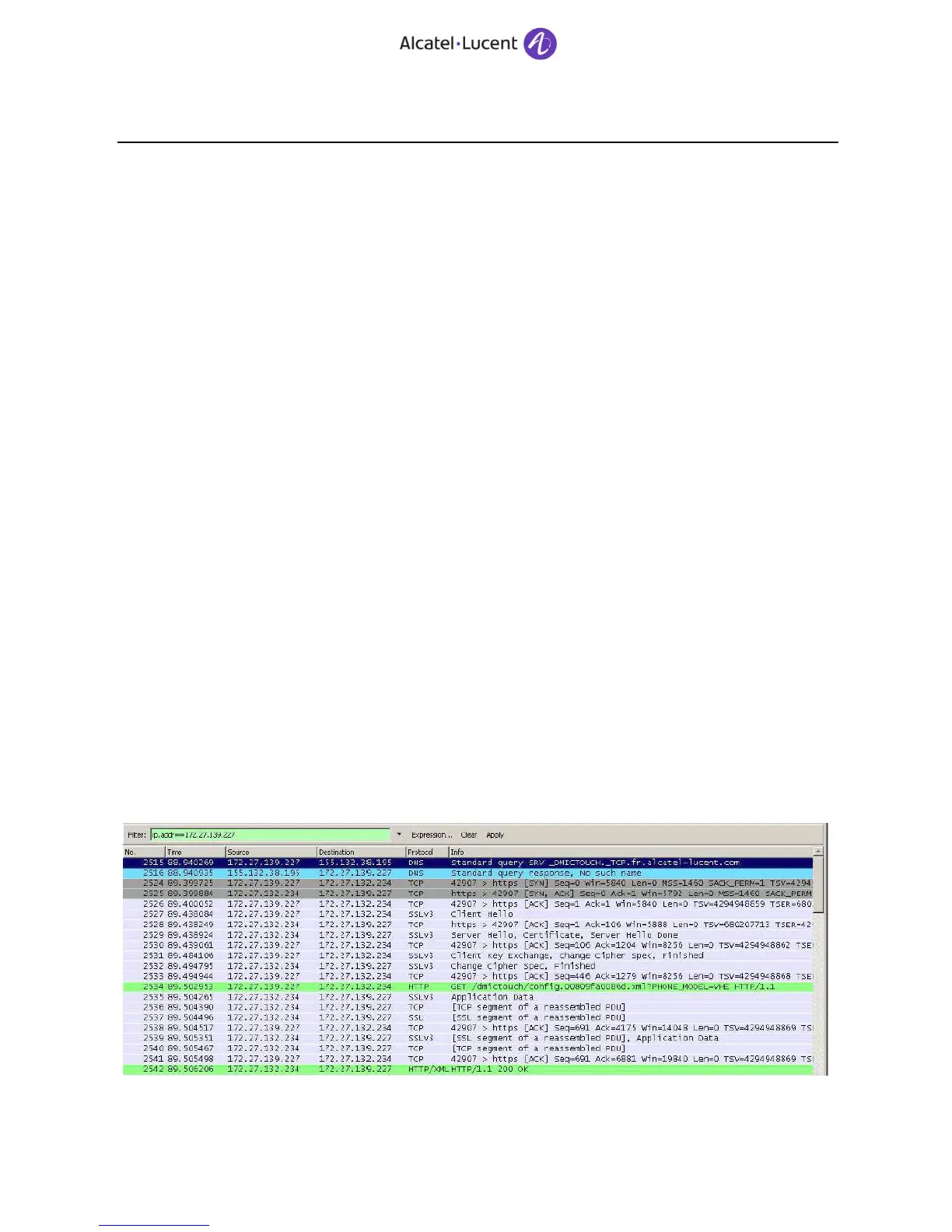
22.2.1 Wireshark to read MyIC Phone OpenTouch exchanges
1) Copy using SFTP the /usr/muser/rsa.XXXXXX.key.pem file with XXXX = your ICE server FQDN to your
computer (ex: in c:\temp)
2) Start wireshark then /preference / protocole / SSL.
Setup the 2 following fields (172.27.132.234 = ICE server @IP)
RSA key lists: 172.27.132.234,443,http,C:\temp\rsa.XXXXXX.key.pem
(ex: 172.27.132.234,443,http,C:\temp\rsa.tssd234.fr.alcatel-lucent.com.key.pem)
SSL debug file: C:\temp\ssl_traces.log
3) Start Wireshark trace and plug the VHE cable to put it on. Decoded packets will be in green
PS: this Wireshark packet trace can be decoded afterward if you get the correct .pem file (Pcap example +
.pem attached for testing)
22.2.2 Mirror the MyIC Phone port to the MyIC Phone PC Port

 Loading...
Loading...











