S350 Series 24-Port (PoE+) and 48-Port Gigabit Ethernet Smart Managed Pro Switches
Manage Device Security User Manual225
The default password is password.
The System Information page displays.
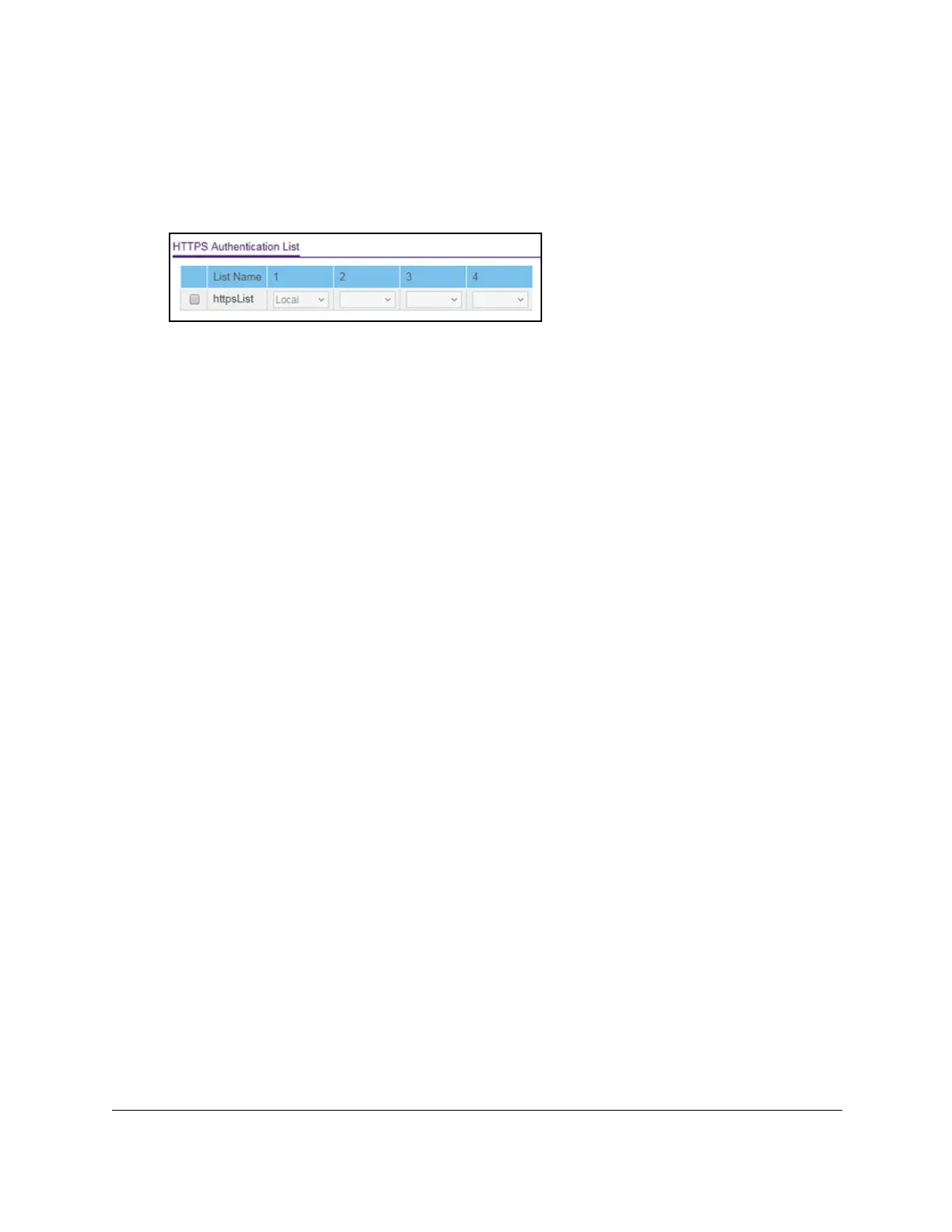
5. Select Security > Management Security > Authentication List > HTTPS Authentication
List
.
6. Select the check box next to the httpsList name.
7. From the menu in the 1 column, select the authentication method that must be used first in
the selected authentication login list.
If you select a method that does not time out as the first method, such as Local, no other
method is tried, even if you specified more than one method.
This setting does not
display when you first create a new login list. User authentication occurs in the order the
methods are selected. Possible methods are as follows:
• Local. The user
’s locally stored ID and password are used for authentication. Since
the Local method does not time out, if you select this option as the first method, no
other method is tried, even if you specified more than one method. This is the default
selection for Method 1.
•
RADIUS.
The user’s ID and password are authenticated using the RADIUS server. If
you select RADIUS or TACACS+ as the first method and an error occurs during the
authentication, the switch uses Method 2 to authenticate the user.
• TACACS+. The user’
s ID and password are authenticated using the TACACS+
server. If you select RADIUS or TACACS+ as the first method and an error occurs
during the authentication, the switch attempts user authentication Method 2.
• None. The authentication method is unspecified, that is, no authentication is required.
8. From the menu in the 2 column, select the authentication method, if any, that must be used
second in the selected authentication login list.
This is the method that is used if the first method times out. If you select a method that
does not time out as the second method, the third method is not tried.
9. From the menu in the 3 column, select the authentication method, if any, that must be used
third in the selected authentication login list.
10. From the menu in the 4 column, select the method, if any, that must be used fourth in the
selected authentication login list.
This is the method that is used if all previous methods time out.
1
1. Click the Apply
button.
Your settings are saved.

 Loading...
Loading...