Configuring Access Security Access Security Configurations
User Guide 515
Protocol V1 Select Enable to enable SSH version 1.
Protocol V2 Select Enable to enable SSH version 2.
Idle Timeout Specify the idle timeout time. The system will automatically release the
connection when the time is up.
Maximum
Connections
Specify the maximum number of the connections to the SSH server. New
connection will not be established when the number of the connections reaches
the maximum number you set.
Port Specify the port using for SSH.
2) In the Encryption Algorithm section, enable the encryption algorithm you want the
switch to support and click Apply.
3) In Data Integrity Algorithm section, enable the integrity algorithm you want the switch
to support and click Apply.
4) In Import Key File section, select key type from the drop-down list and click Browse to
download the desired key file.
Key Type Select the key type. The algorithm of the corresponding type is used for both key
generation and authentication.
Key File Select the desired public key to download to the switch. The key length of the
downloaded file ranges of 512 to 3072 bits.
Note:
It will take a long time to download the key file. Please wait without any operation.
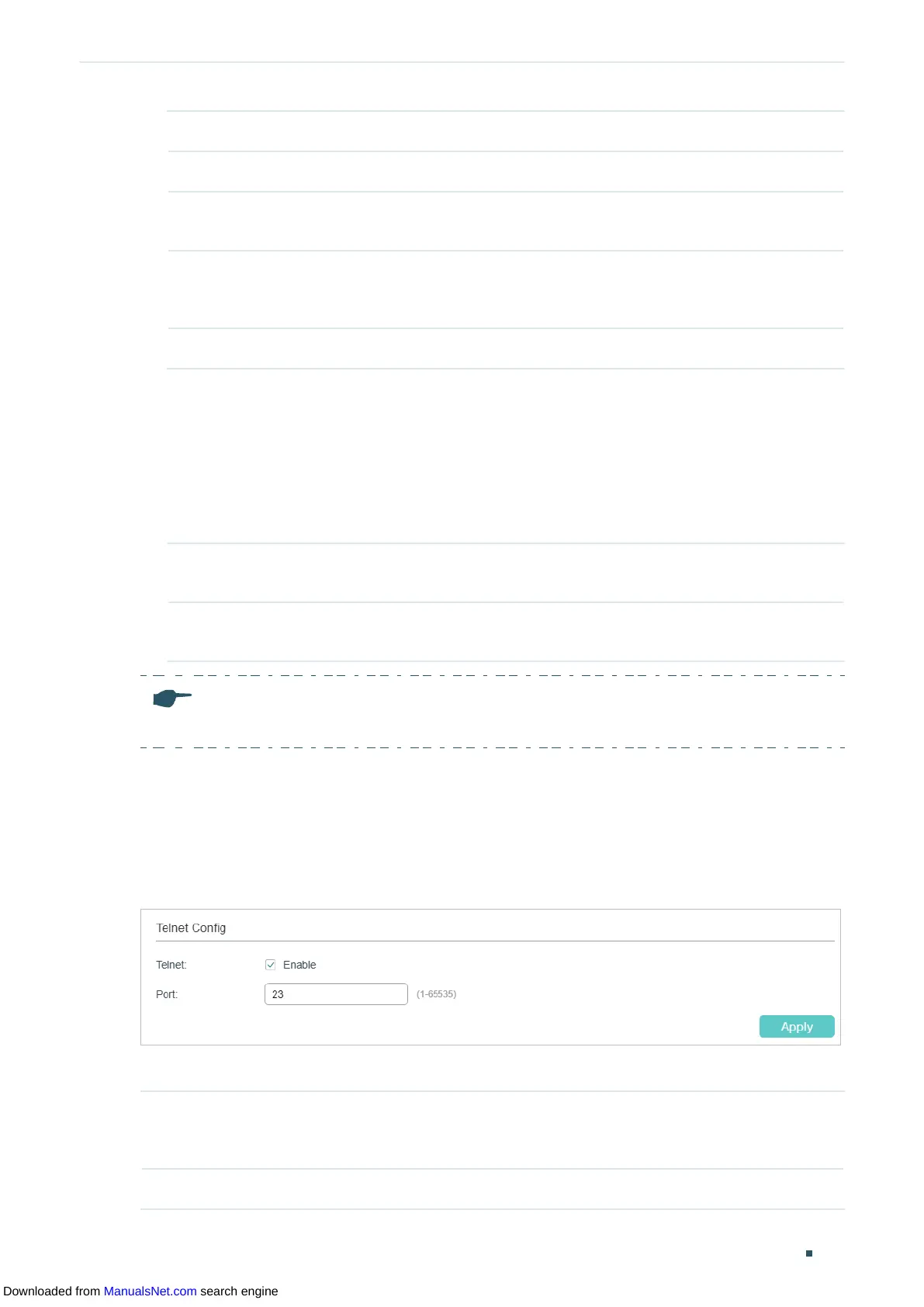
2.1.5 Configuring the Telnet Function
Choose the menu SECURITY > Access Security > Telnet Config to load the following
page.
Figure 2-8 Configuring the Telnet Function
Enable Telnet and click Apply.
Telnet Select Enable to make the Telnet function effective. Telnet function is based on the
Telnet protocol subjected to TCP/IP protocol. It allows users to log on to the switch
remotely.
Port Specify the port using for Telnet.
Downloaded from ManualsNet.com search engine

 Loading...
Loading...











