IP Configuration
IPv4 Management and Interfaces
Cisco 500 Series Managed Switch Administration Guide 360
18
The DHCP Snooping Binding database is also used by IP Source Guard and
Dynamic ARP Inspection features to determine legitimate packet sources.
DHCP Trusted Ports
Ports can be either DHCP trusted or untrusted. By default, all ports are untrusted.
To create a port as trusted, use the DHCP Snooping Interface Settings page.
Packets from these ports are automatically forwarded. Packets from trusted ports
are used to create the Binding database and are handled as described below.
If DHCP Snooping is not enabled, all ports are trusted by default.
How the DHCP Snooping Binding Database is Built
The following describes how the device handles DHCP packets when both the
DHCP client and DHCP server are trusted. The DHCP Snooping Binding database
is built in this process.
DHCP Trusted Packet Handling
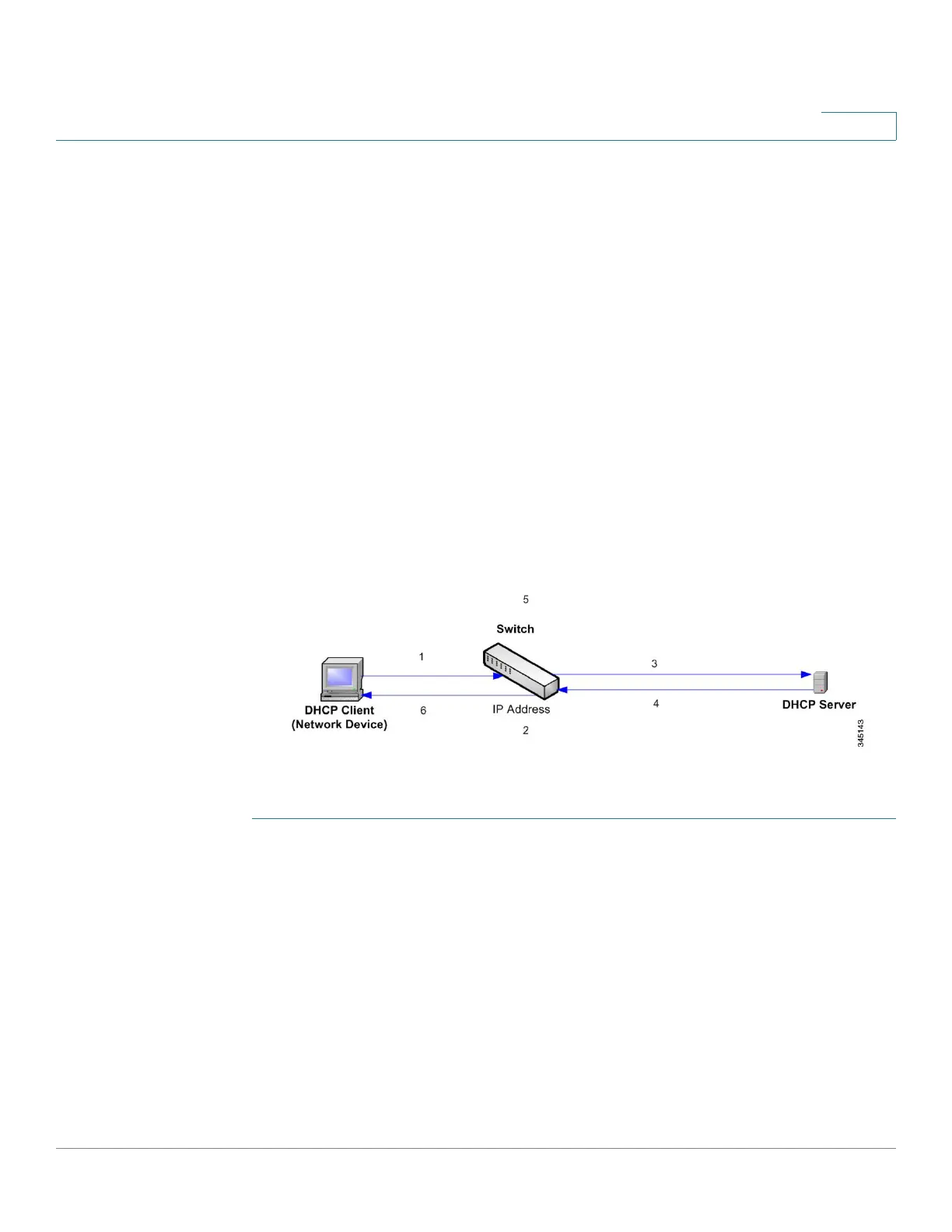
The actions are:
STEP 1 Device sends DHCPDISCOVER to request an IP address or DHCPREQUEST to
accept an IP address and lease.
STEP 2 Device snoops packet and adds the IP-MAC information to the DHCP Snooping
Binding database.
STEP 3 Device forwards DHCPDISCOVER or DHCPREQUEST packets.
STEP 4 DHCP server sends DHCPOFFER packet to offer an IP address, DHCPACK to
assign one, or DHCPNAK to deny the address request.
STEP 5 Device snoops packet. If an entry exists in the DHCP Snooping Binding table that
matches the packet, the device replaces it with IP-MAC binding on receipt of
DHCPACK.

 Loading...
Loading...


















