Configure System Information
118
S3300 Smart Managed Pro Switch
Interface Configuration
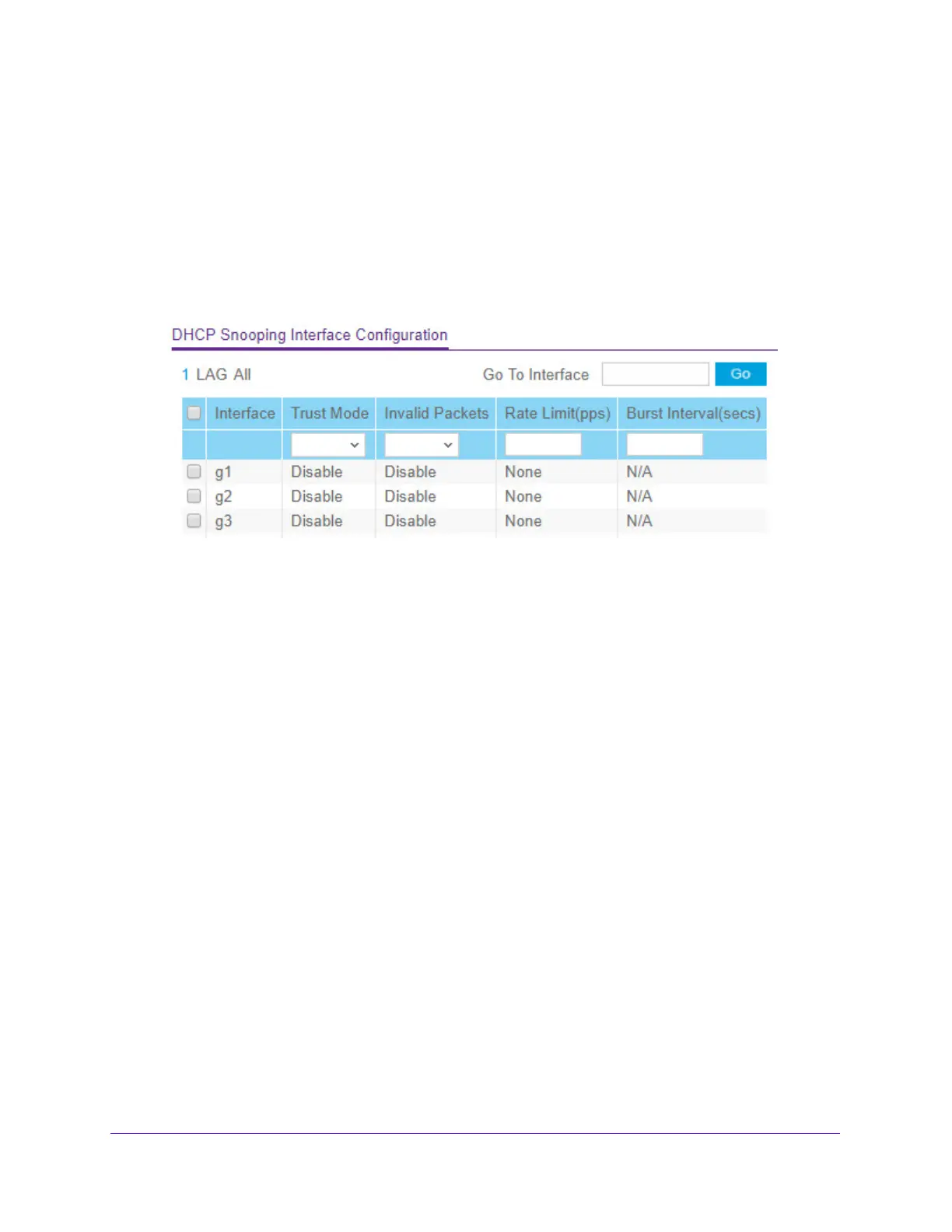
Use the DHCP Snooping Interface Configuration screen to view and configure each port as a
trusted or untrusted port. Any DHCP responses received on a trusted port are forwarded. If a
port is configured as untrusted, any DHCP (or BootP) responses received on that port are
discarded.
To configure DHCP snooping interface settings:
1. Select System> Servi
ces > DHCP Snooping > Interface Configuration.
Figure 68. DHCP Snooping Interface Configuration
2. Select one or more ports or LAGs to configure.
For information about how to select and configure one or more ports and LAGs, see
Configuring Interface Settings on p
age 32.
3. From
the Trust Mode list, select the desired trust mode.
• Disabled. The
interface is considered to be untrusted and could potentially be used to
launch a network attack. DHCP server messages are checked against the bindings
database. On untrusted ports, DHCP snooping enforces the following security rules:
- DH
CP packets from a DHCP server (DHCPOFFER, DHCPACK, DHCPNAK,
DHCPRELEASEQUERY) are dropped.
- DHCPRELEASE and
DHCPDECLINE messages are dropped if the MAC address
is in the snooping database but the binding’s interface is other than the interface
where the message was received.
- DHCP p
ackets are dropped when the source MAC address does not match the
client hardware address if MAC address validation is globally enabled.
• Enabled. The interface is considered
to be trusted and forwards DHCP server
messages without validation.
4. From t
he Logging Invalid Packets list, select the packet logging mode.
When enabled, the DHCP snooping feature generate
s a log message when an invalid
packet is received and dropped by the interface.
5. In
the Rate Limit (pps) field, specify the rate limit value for DHCP snooping purposes.

 Loading...
Loading...











