CHAPTER16 Services
Mediant 800 Gateway & E-SBC | User's Manual
➢ To configure the RADIUS Vendor ID:
1. Open the Authentication Server page (Setup menu > Administration tab > Web & CLI folder
> Authentication Server).
2. Under the RADIUS group, in the 'RADIUS VSA Vendor ID' field, enter the same vendor ID
number as set on the third-party RADIUS server.
3. Click Apply.
RADIUS-based Management User Authentication
You can enhance security for your device by implementing Remote Authentication Dial-In User
Service (RADIUS - RFC 2865) for authenticating multiple management user accounts of the
device’s embedded Web and Telnet (CLI) servers. Thus, RADIUS also prevents unauthorized
access to your device.
When RADIUS authentication is not used, the user's login username and password are locally
authenticated by the device using the Local Users table (see Configuring Management User
Accounts ). However, you can configure the device to use the Local Users table as a fallback
mechanism if the RADIUS server does not respond.
If you enable RADIUS- based user login authentication, when users with Security
Administrator privilege level log in to the device’s CLI, they are automatically given
access to the CLI privileged mode (“#”). For all other user privilege levels, the user
needs to run the enable command and then enter the password to access the CLI
privileged mode.
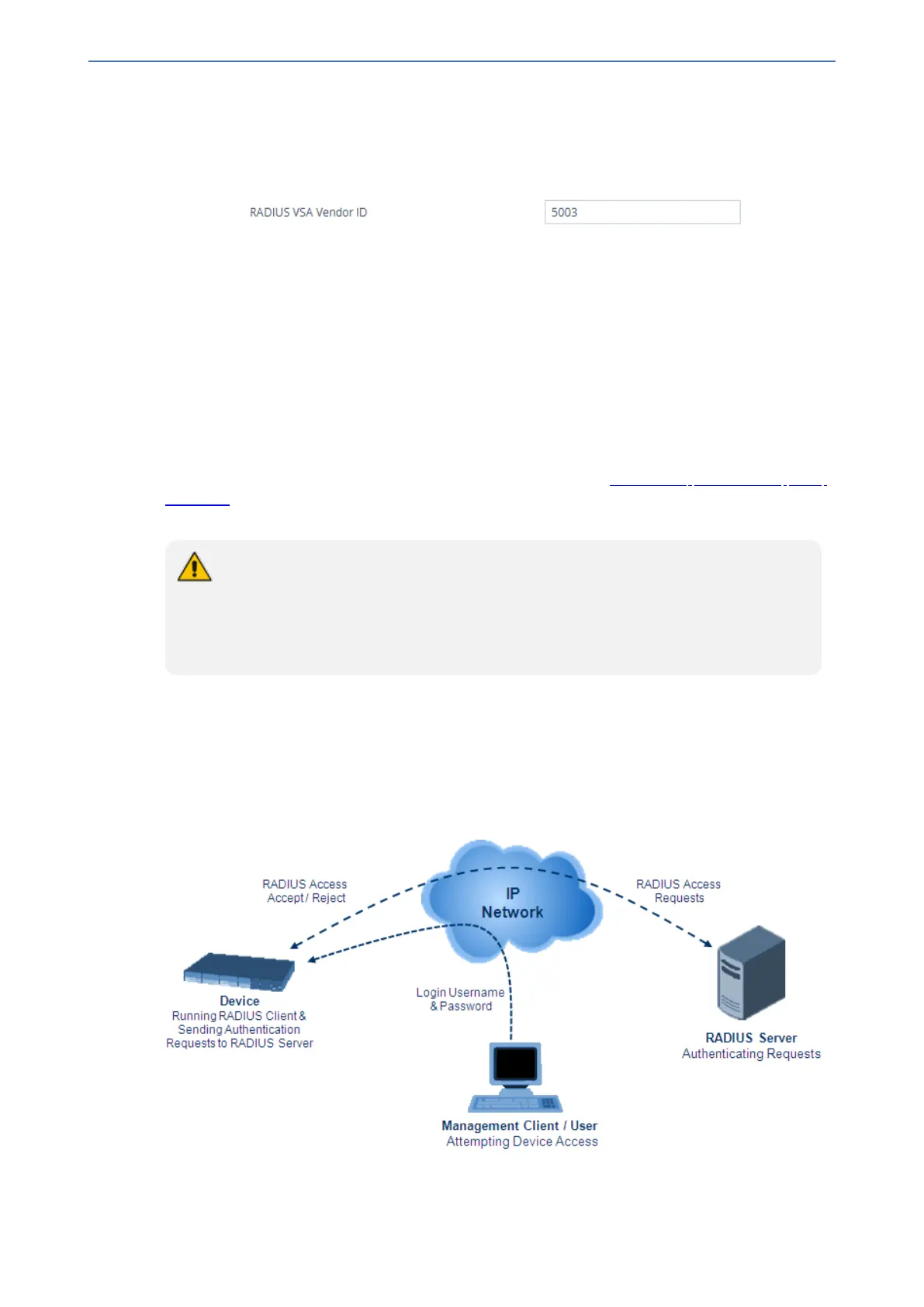
When RADIUS authentication is used, the RADIUS server stores the user accounts - usernames,
passwords, and access levels (authorization). When a management user (client) tries to access
the device, the device sends the RADIUS server the user's username and password for
authentication. The RADIUS server replies with an acceptance or a rejection notification. During
the RADIUS authentication process, the device’s Web interface is blocked until an acceptance
response is received from the RADIUS server. Communication between the device and the
RADIUS server is done using a shared secret, which is not transmitted over the network.
To implement RADIUS, you need to do the following:
- 220 -

 Loading...
Loading...
















