63
Figure 4 IKEv2 Initial exchange process
New features in IKEv2
DH guessing
In the IKE_SA_INIT exchange, the initiator guesses the DH group that the responder is most likely to
use and sends it in an IKE_SA_INIT request message. If the initiator's guess is correct, the
responder responds with an IKE_SA_INIT response message and the IKE_SA_INIT exchange is
finished. If the guess is wrong, the responder responds with an INVALID_KE_PAYLOAD message
that contains the DH group that it wants to use. The initiator then uses the DH group selected by the
responder to reinitiate the IKE_SA_INIT exchange. The DH guessing mechanism allows for more
flexible DH group configuration and enables the initiator to adapt to different responders.
Cookie challenging
Messages for the IKE_SA_INIT exchange are in plain text. An IKEv1 responder cannot confirm the
validity of the initiators and must maintain half-open IKE SAs, which makes the responder
susceptible to DoS attacks. An attacker can send a large number of IKE_SA_INIT requests with
forged source IP addresses to the responder, exhausting the responder's system resources.
IKEv2 introduces the cookie challenging mechanism to prevent such DoS attacks. When an IKEv2
responder maintains a threshold number of half-open IKE SAs, it starts the cookie challenging
mechanism. The responder generates a cookie and includes it in the response sent to the initiator. If
the initiator initiates a new IKE_SA_INIT request that carries the correct cookie, the responder
considers the initiator valid and proceeds with the negotiation. If the carried cookie is incorrect, the
responder terminates the negotiation.
The cookie challenging mechanism automatically stops working when the number of half-open IKE
SAs drops below the threshold.
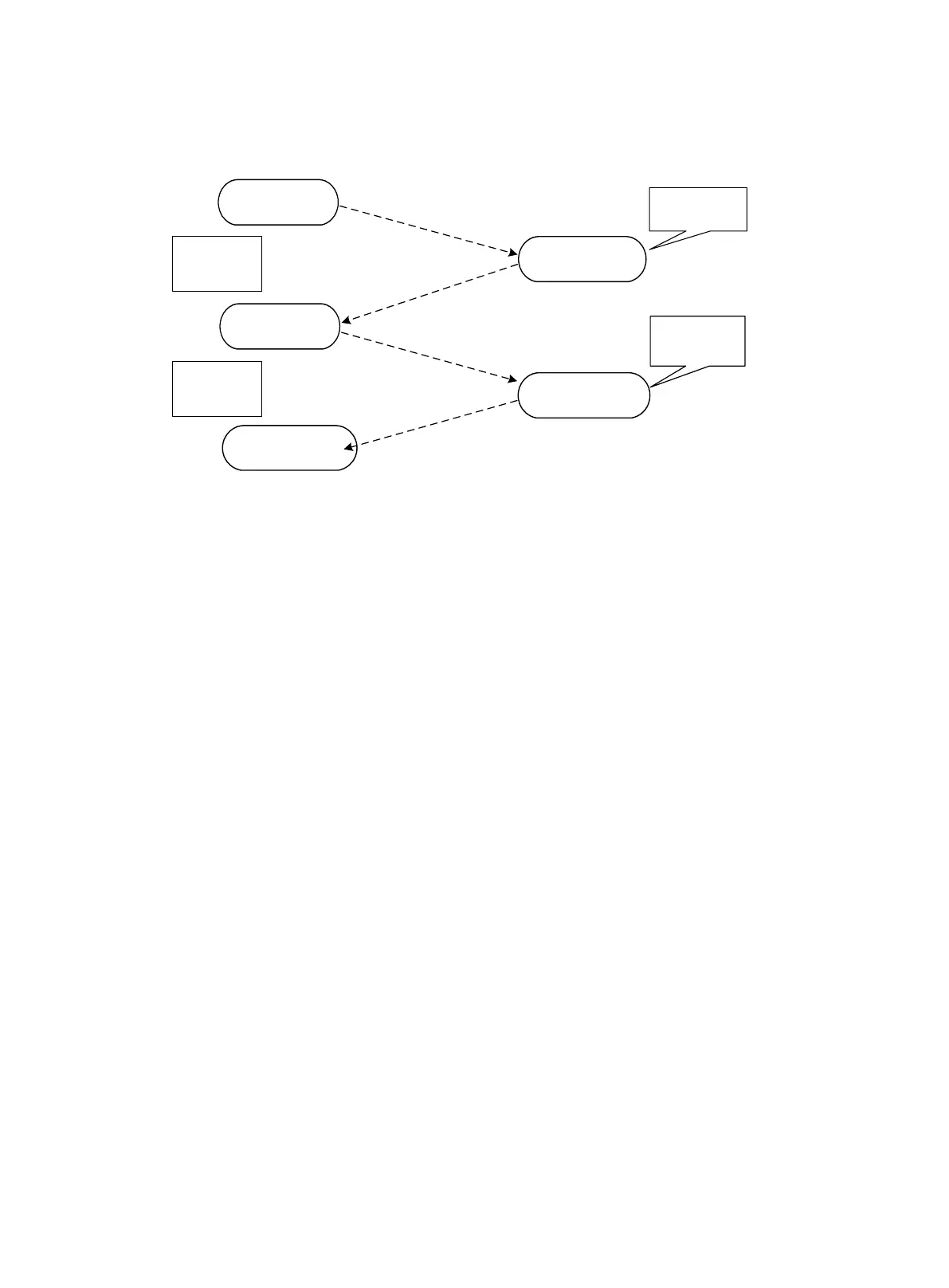
Initiator’
s policy and key
information
Peer
1
Peer
2
Confirmed policy and
key information
Initiator
’s identity
,
authentication data
, and
IPsec proposals
Responder’
s identity
,
authentication data
, and
IPsec proposals
Authenticate the
identity and
negotiate IPsec
SAs
Negotiate
algorithms and
generate the key
Perform ID and exchange
authentication and
negotiate IPsec SAs
Search for a
matched policy and
generate the key
Receive the
policy and
generate the key
Send the local
IKE policy and
key info
Perform ID and exchange
authentication and
negotiate IPsec SAs
ID exchange
,
authentication
,
IPsec SA setup
SA
exchange
,
key exchange

 Loading...
Loading...