Configuring Learned Port Security Configuring Learned Port Security
OmniSwitch AOS Release 8 Network Configuration Guide December 2017 page 33-17
-> port-security port 2/1-4 mac-range low 00:20:d0:59:0c:9a high
00:20:d0:59:0c:9f
To restore the range to the default values, use the port-security parameter followed by the port keyword
and slot/port designation of the port and the mac-range. The MAC address range is restored to
00:00:00:00:00:00 and ff:ff:ff:ff:ff:ff when the low and high MAC addresses are excluded. For example,
the following command sets the authorized MAC address range to the default values for port 12 of slot 4:
-> port-security port 4/12 mac-range
In addition, specifying a low end MAC and a high end MAC is optional. If either one is not specified, the
default value is used. For example, the following commands set the authorized MAC address range on the
specified ports to 00:da:25:59:0c:10–ff:ff:ff:ff:ff:ff and 00:00:00:00:00:00–00:da:25:00:00:9a:
-> port-security port 2/8 mac-range low pp:da:25:59:0c
-> port-security port 2/10 mac-range high 00:da:25:00:00:9a
Refer to the OmniSwitch AOS Release 8 CLI Reference Guide for more information about this command.
Selecting the Security Violation Mode
The port-security port violation command configures the violation mode (restrict, discard, or shutdown)
that is applied to an LPS port when the maximum number of bridged and filtered addresses allowed on the
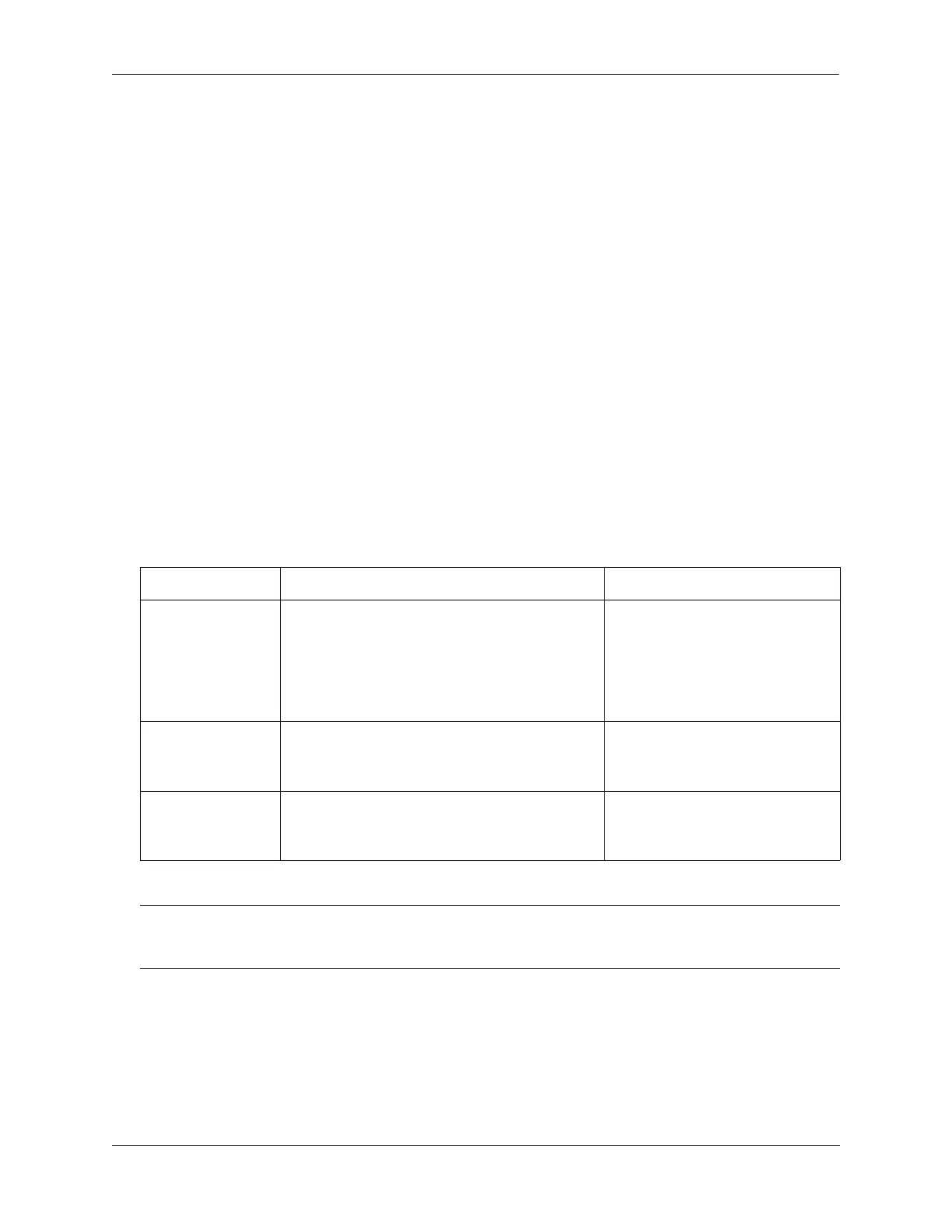
port is reached. Use the following table to determine how each violation mode is applied and which
actions or events will clear the violation state and return the port to normal operation:
By default, the security violation mode for an LPS port is set to restrict. To configure the security
violation mode for an LPS port, enter port-security followed by the slot/port designation of the port, then
violation followed by restrict, discard, or shutdown. For example, the following command selects the
shutdown mode for port 1/4:
-> port-security port 4/1 violation shutdown
Mode (Parameter) Violation Mode Description Violation Recovery
restrict Port remains up but unauthorized MAC
addresses are blocked. All other packets that
contain an authorized source MAC address are
allowed to continue forwarding on the port.
• Bridge and filtered MAC
addresses age out.
• MAC addresses are flushed.
• Use clear violation command.
• Link down/up event.
• LPS port is removed.
discard Port remains up but all traffic received on the
port is discarded. Dynamically learned MAC
addresses are flushed.
• Use clear violation command.
• Link down/up event.
• LPS port is removed.
shutdown Port is administratively disabled. All traffic is
stopped at the port; no traffic is forwarded.
• Use clear violation command.
• Link down/up event.
• LPS port is removed.
Note. Unauthorized source MAC addresses are not learned in the LPS table but are still recorded in the
source learning MAC address table with a filtered operational status. This allows the user to view MAC
addresses that were attempting unauthorized access to the LPS port.

 Loading...
Loading...











