Configuring VLANs Using Private VLANs
OmniSwitch AOS Release 8 Network Configuration Guide December 2017 page 4-15
Using Private VLANs
The Private VLAN (PVLAN) feature provides the ability to isolate Layer 2 data between devices that are
on the same VLAN. This type of data isolation improves security and simplifies system configuration.
A standard VLAN usually represents a single broadcast domain, but a PVLAN divides a VLAN (Primary)
into sub-VLANs (Secondary). The single broadcast domain is partitioned into smaller broadcast sub-
domains while keeping the existing Layer 3 configuration. When a VLAN is configured as a PVLAN, the
PVLAN is referred to as the Primary VLAN, and any subsequent VLANs that are associated with the
Primary VLAN are referred to as Secondary VLANs.
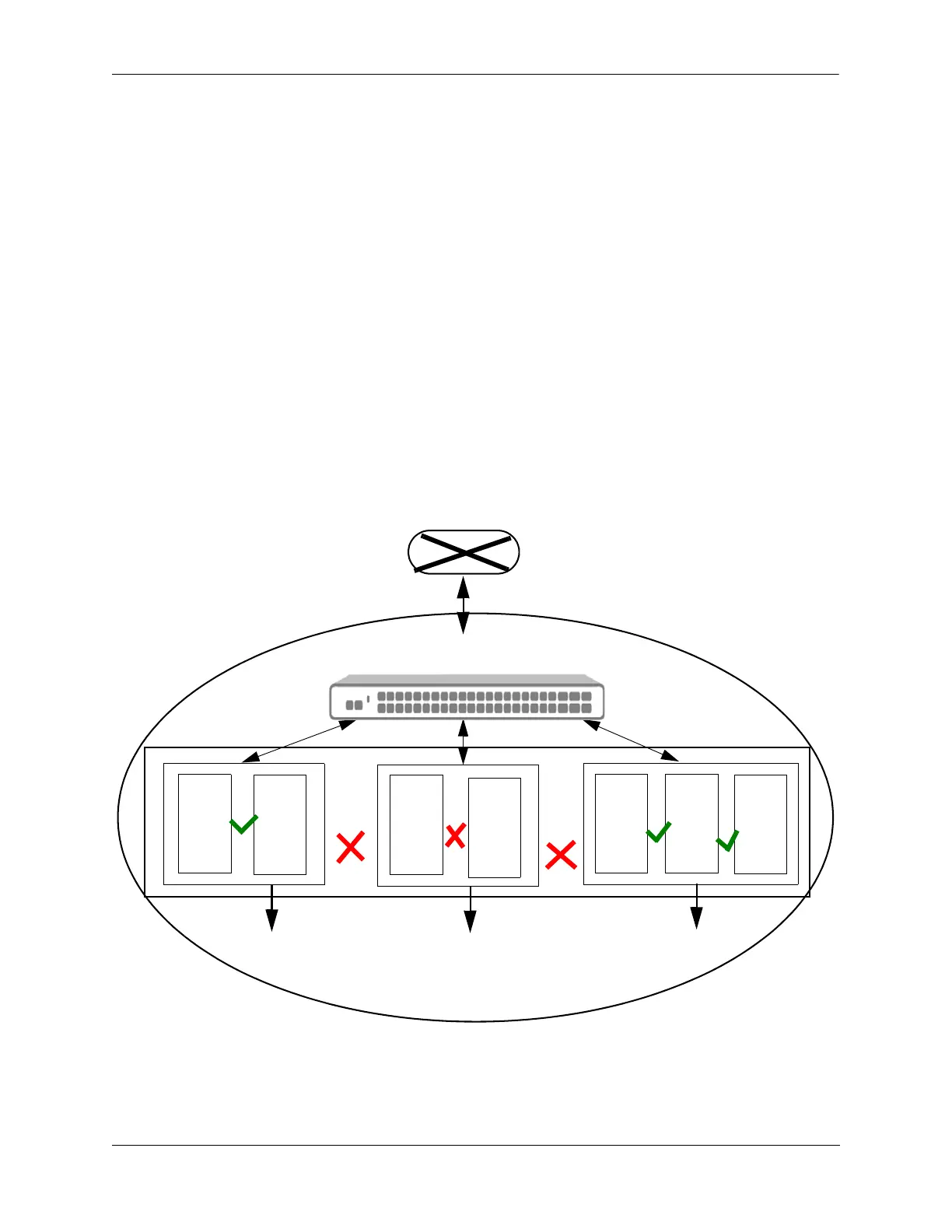
For example, consider an example where a single switch is used by different work groups. The users from
different work groups are all connected to the same VLAN. Having all the users operating in the same
VLAN domain can lead to compromise in data security and complexity in managing them.
To isolate the users from each other, Secondary VLANs can be created for each work group under the
Primary VLAN. The following diagram represents the scenario where W1, W2, and W3 are three different
work groups sharing the same PVLAN. To isolate them from communicating with each other, they are
assigned to individual Secondary VLANs. These Secondary VLANs cannot communicate with each other,
except the PVLAN port. The PVLAN communicates with the promiscuous port and exchanges data with
the respective Secondary VLANs.
There are two types of Secondary VLANs:
OmniSwitch
W1:A W1:B
W2:A
W2:B
W3:A
W3:B
W3:C
Community VLAN
Isolated VL.AN
Community VLAN
Router
Promiscuous Port
PVLAN
Secondary
VLAN

 Loading...
Loading...











