Version 7.2 249 Mediant 1000B Gateway & E-SBC
User's Manual 15. Services
sAMAccountName that equals "SueM".
Attribute (e.g., "memberOf") to return from objects that match the filter criteria:
The attribute is configured by the 'Management Attribute' parameter in the LDAP
Servers table (see ''Configuring LDAP Servers'' on page
244).
Therefore, the LDAP response includes only the groups of which the specific user is a
member.
Note:
• The search filter is applicable only to LDAP-based login authentication and
authorization queries.
• The search filter is a global setting that applies to all LDAP-based login
authentication and authorization queries, across all configured LDAP servers.
To configure the LDAP search filter for management users:
1. Open the LDAP Settings page (Setup menu > IP Network tab > RADIUS & LDAP
folder > LDAP Settings).
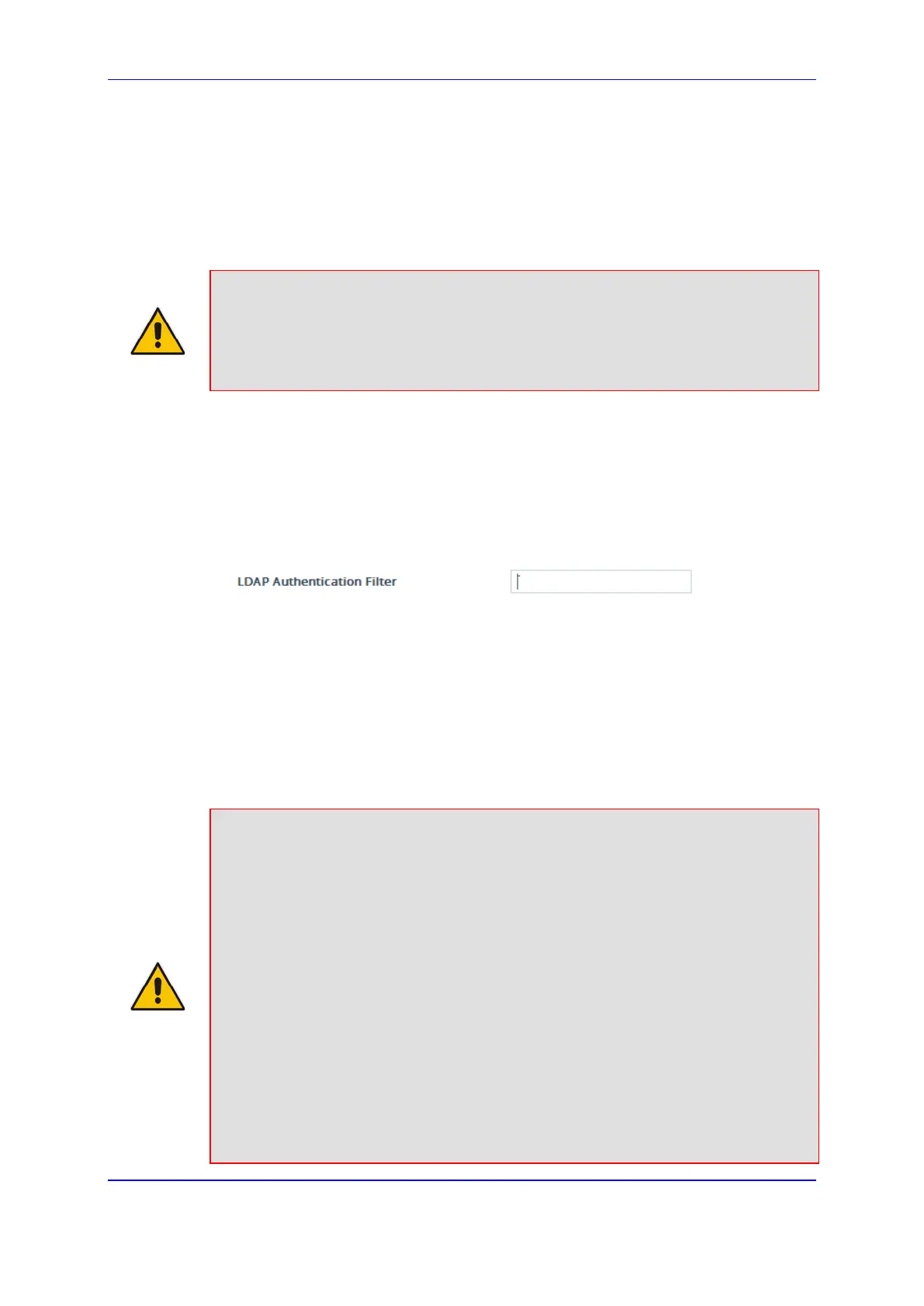
2. In the 'LDAP Authentication Filter' field, enter the LDAP search filter attribute for
searching the login username for user authentication:
Figure 15-21: Configuring LDAP Search Filter
3. Click Apply.
15.3.7 Configuring Access Level per Management Groups Attributes
The Management LDAP Groups table lets you configure LDAP group objects and their
corresponding management user access level. The table is a "child" of the LDAP Servers
table (see ''Configuring LDAP Servers'' on page 244) and configuration is done per LDAP
server. For each LDAP server, you can configure up to three table row entries of LDAP
group(s) and their corresponding access level.
Note:
• The Management LDAP Groups table is applicable only to LDAP-based login
authentication and authorization queries.
• If the LDAP response received by the device includes multiple groups of which the
user is a member and you have configured different access levels for some of
these groups, the device assigns the user the highest access level. For example, if
the user is a member of two groups where one has access level "Monitor" and the
other "Administrator", the device assigns the user the "Administrator" access level.
• When the access level is unknown, the device assigns the default access level to
the user, configured by the 'Default Access Level' parameter as used also for
RADIUS (see ''Configuring RADIUS-based User Authentication'' on page 237).
This can occur in the following scenarios:
√ The user is not a member of any group.
√ The group of which the user is a member is not configured on the device (as
described in this section).
√ The device is not configured to query the LDAP server for a management
attribute (see ''Configuring LDAP Servers'' on page 244).

 Loading...
Loading...















