User's Manual 666 Document #: LTRT-27055
Mediant 1000B Gateway & E-SBC
Note: The voice-
related coder configuration (Allowed and Extension coders) is
independent of the fax-related coder configuration, with the exception of the G.711
coder. If the G.711 coder is restricted by the Allowed Audio Coders Groups table, it is
not used for fax processing even if it is listed in the Coder Groups table for faxes.
However, support for G.711 coders for voice is not dependent upon which fax coders
are listed in the Coder Groups table.
29.7 Limiting SBC Call Duration
You can configure the maximum allowed call duration (in minutes) per SBC call. If an
established call reaches this user-defined limit, the device terminates the call. The feature
ensures that calls are properly terminated, allowing available resources for new calls. The
following procedure describes how to configure the feature for all calls (globally). To
configure the feature per specific calls, use IP Profiles (IpProfile_SBCMaxCallDuration).
To configure maximum call duration:
1. Open the SBC General Settings page (Setup menu > Signaling & Media tab > SBC
folder > SBC General Settings).
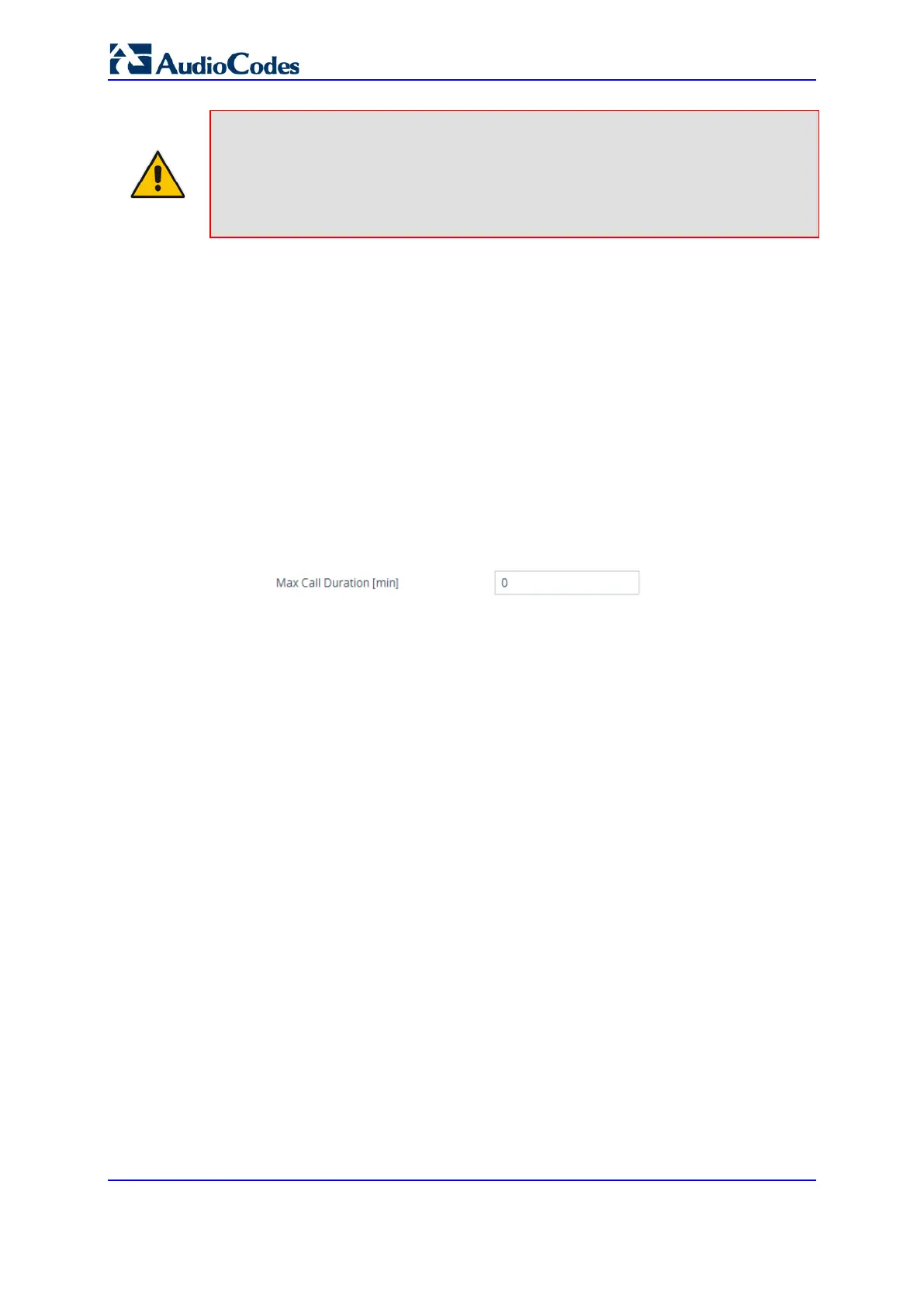
2. In the 'Max Call Duration' field (SBCMaxCallDuration), enter the maximum call
duration per SBC call:
Figure 29-6: Configuring Maximum Call Duration
3. Click Apply.
29.8 SBC Authentication
The device can authenticate SIP servers and SBC users (clients). The different
authentication methods are described in the subsequent subsections.
29.8.1 SIP Authentication Server Functionality
The device can function as an Authentication server for authenticating received SIP
message requests, based on HTTP authentication Digest with MD5. Alternatively, such
requests can be authenticated by an external, third-party server.
When functioning as an Authentication server, the device can authenticate the following
SIP entities:
SIP servers: This is applicable to Server-type IP Groups. This provides protection
from rogue SIP servers, preventing unauthorized usage of device resources and
functionality. To authenticate remote servers, the device challenges the server with a
user-defined username and password that is shared with the remote server. When the
device receives an INVITE request from the remote server, it challenges the server by
replying with a SIP 401 Unauthorized response containing the WWW-Authenticate
header. The remote server then re-sends the INVITE containing an Authorization
header with authentication information based on this username-password combination
to confirm its identity. The device uses the username and password to authenticate
the message prior to processing it.
SIP clients: These are clients belonging to a User-type IP Group. This support
prevents unauthorized usage of the device's resources by rogue SIP clients. When the
device receives an INVITE or REGISTER request from a client (e.g., SIP phone) for
SIP message authorization, the device processes the authorization as follows:

 Loading...
Loading...















