NXP Semiconductors
UM11227
NTM88 family of tire pressure monitor sensors
UM11227 All information provided in this document is subject to legal disclaimers. © NXP B.V. 2020. All rights reserved.
User manual Rev. 6 — 24 April 2020
175 / 205
aaa-031078
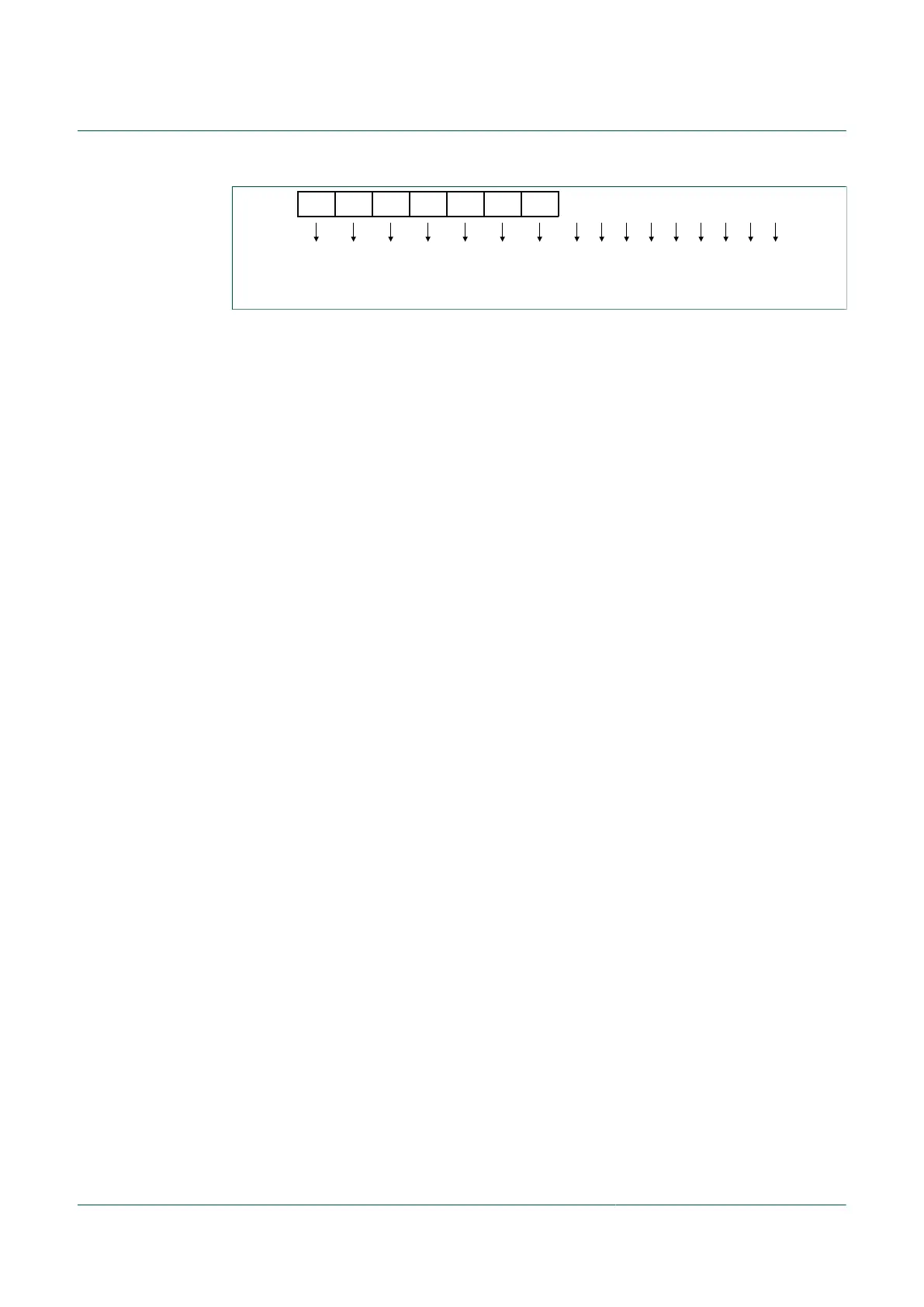
FPS7 FPS6 FPS5 FPS4 FPS3 FPS2 FPS1 1 1 1 1 1 1 1 1 1
A15 A14 A13 A12 A11 A10 A9 A8 A7 A6 A5 A4 A3 A2 A1 A0
Figure 57. Flash block protection protocol
10.24.7 FMC vector redirection
Vector redirection is not recommended for TPMS applications where NXP firmware has
been included in the final image.
Whenever any block protection is enabled, the reset and interrupt vectors will be
protected. Vector redirection allows users to modify interrupt vector information without
unprotecting boot loader and reset vector space. Vector redirection is enabled by
programming the FNORED bit in the NVOPT register located at address $FFBF to zero.
For redirection to occur, at least some portion but not all of the FLASH memory must be
block protected by programming the NVPROT register located at address $FFBD. All of
the interrupt vectors (memory locations $FFC0–$FFFD) are redirected, though the reset
vector ($FFFE:FFFF) is not.
For example, if 512 bytes of FLASH are protected, the protected address region is
from $FE00 through $FFFF. The interrupt vectors ($FFC0–$FFFD) are redirected to
the locations $FDC0–$FDFD. If an SPI interrupt is taken for instance, the values in the
locations $FDE0:FDE1 are used for the vector instead of the values in the locations
$FFE0:FFE1. This allows the user to reprogram the unprotected portion of the FLASH
with new program code including new interrupt vector values while leaving the protected
area, including the default vector locations, unchanged.
10.24.8 FMC security
Circuitry is included to prevent unauthorized access to the contents of FLASH and RAM
memory. When security is engaged, FLASH and RAM are considered secure resources.
Direct-page registers, high-page registers, and the BACKGROUND DEBUG controller
are considered unsecured resources. Programs executing within secure memory have
normal access to any MCU memory locations and resources. Attempts to access a
secure memory location with a program executing from an unsecured memory space or
through the BACKGROUND DEBUG interface are blocked (writes are ignored and reads
return all 0s).
Security is engaged or disengaged based on the state of two nonvolatile register bits
(SEC0[1:0]) in the FOPT register. During reset, the contents of the nonvolatile location
NVOPT are copied from FLASH into the working FOPT register in high-page register
space. A user engages security by programming the NVOPT location, which can be done
at the same time the FLASH memory is programmed. The 1:0 state disengages security
and the other three combinations engage security. Notice the erased state (1:1) makes
the MCU secure. During development, whenever the FLASH is erased, it is good practice
to immediately program the SEC00 bit to 0 in NVOPT so SEC[1:0] = 1:0. This would
allow the MCU to remain unsecured after a subsequent reset.
The on-chip debug module cannot be enabled while the MCU is secure. The separate
BACKGROUND DEBUG controller can still be used for background memory access
commands, but the MCU cannot enter ACTIVE BACKGROUND mode except by holding
BKGD/MS low at the rising edge of reset.
 Loading...
Loading...