Firewall
294
8.3
The BAT Firewall
BAT54-Rail/F..
Release
7.54
06/08
If the "close port" action is executed, an entry in a block list is made, by
which all packets, which are sent at the respective computer and port,
get rejected. For the "close port" object a timeout can be given in sec-
onds, minutes or hours, which is inserted directly behind the object ID.
This time value is composed of the designator of the time unit (h, m, s for
hour, minute and second), and the actual time. Thus e.g. %pm10 closes
a port for 10 minutes. If no time unit is provided, then implicitly "minutes"
apply (and thus %p10 is equivalent to %pm10).
If the "Deny host" action is executed, then the sender of the packet is
registered in a block list. Starting from this moment, all packets received
from the blocked server will be rejected. Also the "Deny host" object can
be provided with a time-out, which is formed similarly to the "CLOSE
port" option.
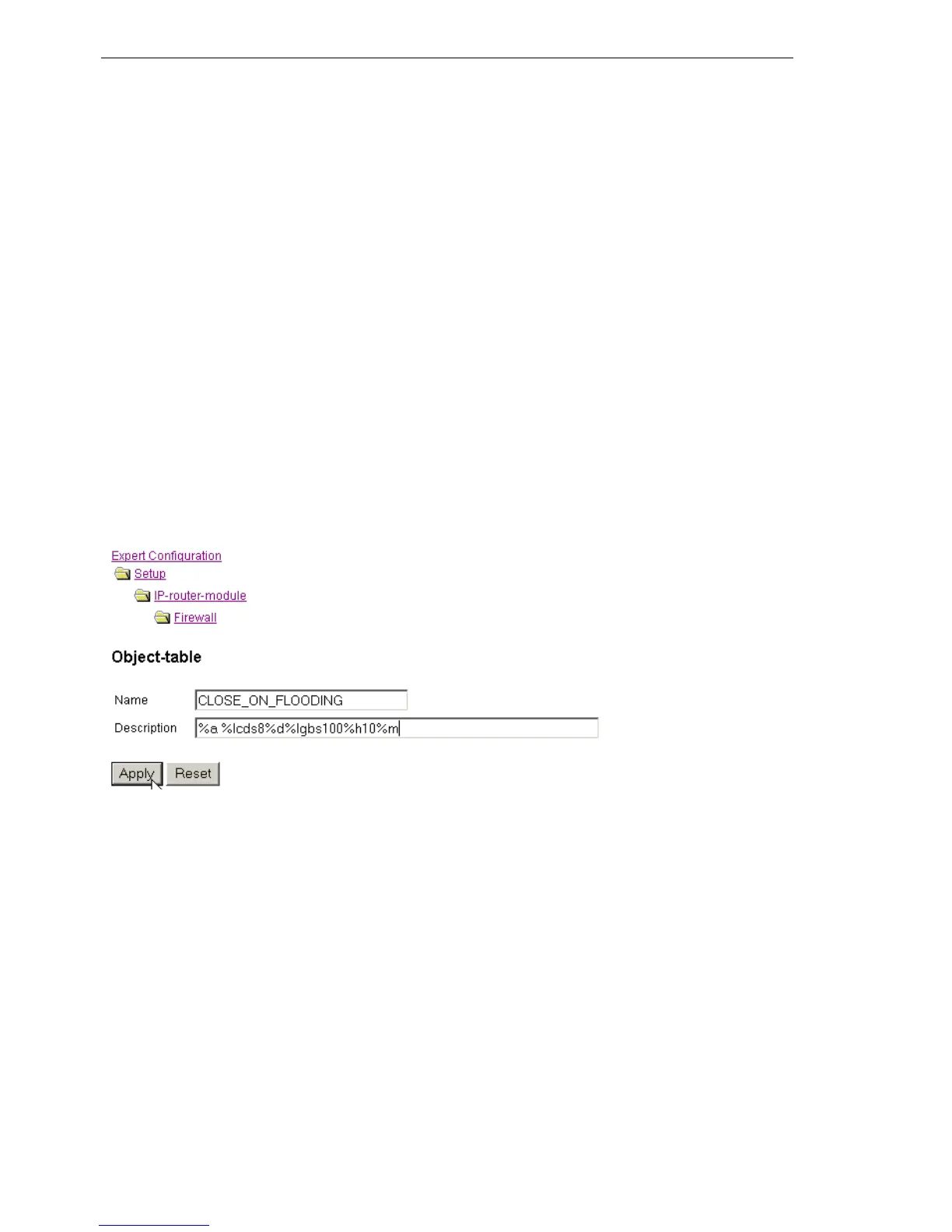
If you want to limit e.g. the permissible data rate for a connection to 8 kbps
and to lock out the aggressor committing a flooding attempt, and furthermore
send at the same time an email to the administrator, then the description of
the object for the action reads as follows:
D This description permits traffic (
%a
) at the beginning. A simple %a at the
beginning of the description is equivalent to a %lp0%a (= accept, if the
limit was exceeded on zero packets, i.e. with the first packet).
D If over the current connection now 8 kbit (
%lcds8
) is transferred in one sec-
ond, then all further packets - up to the expiration of the second - will be
silently discarded (
%d
), thus automatically creating a Traffic Shaping.
D If 100 packets for the server (destination address of the connection) arrive
(
%lgbs100
) in one second, then the remote host (source address) is locked
for 10 minutes (
%h10
), and an email is sent to the administrator (
%m
) .
Similar to the address and service objects of the object table, action objects
can be provided with a name, and can arbitrarily be combined recursively,
whereby the maximum recursion depth is limited to 16. In addition, they can
be entered directly into the action field of the rule table.
 Loading...
Loading...