Routing and WAN connections
BAT54-Rail/F..
Release
7.54
06/08
11.5
Demilitarized Zone (DMZ)
381
11.5.3 Address check with DMZ and intranet
interfaces
To shield the DMZ (demilitarized zone) and the Intranet from unauthorized
attacks, you can activate an additional address check for each interface us-
ing the firewall's Intrusion Detection System (IDS).
The relevant buttons are called 'DMZ check' or 'Intranet check' and can have
the values 'loose' or 'strict':
D If the button is set to 'loose', then every source address is accepted if the
BAT is addressed directly.
D If the switch is set to 'strict', then a return route has to be explicitly avail-
able so that no IDS alarm is triggered. This is usually the case if the data
packet contains a sender address to which the relevant interface can also
route data. Sender addresses from other networks to which the interface
cannot route, or sender addresses from its own address range therefore
lead to an IDS alarm.
Note: For all devices, the default is 'loose'. The default is set to 'strict' for BAT
7011 VPN only, as a more precise address check has already already
been used for this device.
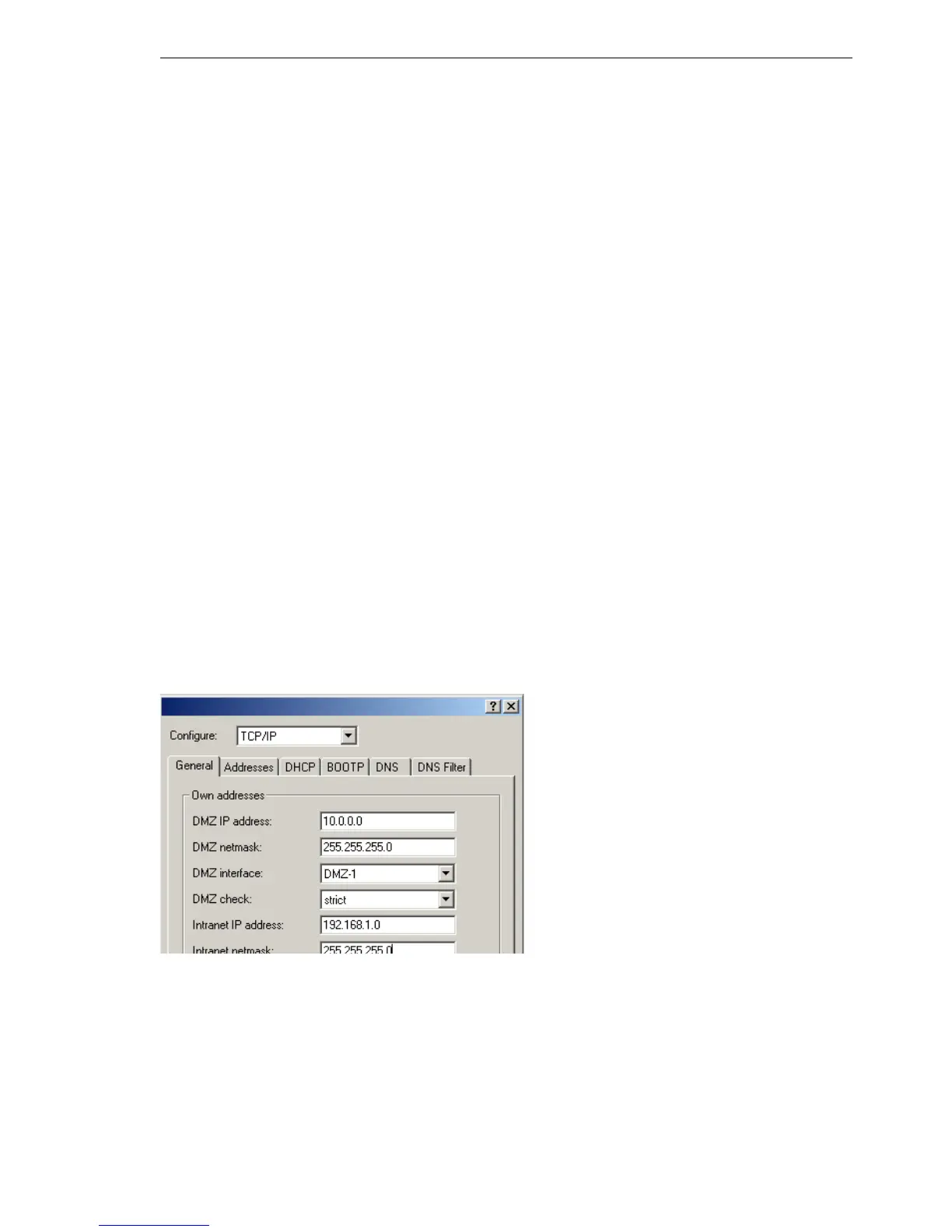
Configuration with LANconfig
You will find the button for activating the DMZ and Intranet address check in
LANconfig in the 'TCP-IP' configuration area on the 'General' tab page.
 Loading...
Loading...