Routing and WAN connections
358
11.2
IP routing
BAT54-Rail/F..
Release
7.54
06/08
11.2.2 Policy-based routing
Policy-based routing does not rely exclusively upon the destination IP ad-
dress to define the destination route (meaning the remote device that is to be
used to transfer the data). Further information can be used-such as the ser-
vice or the protocol used, sender addresses or the destination for the data
packets-for the selection of the destination route. Policy-based routing can
be used to achieve a significantly finer-grained routing behavior, such as in
the following application scenarios:
D The LAN's entire Internet traffic is diverted to a proxy without entering the
proxy address into the browsers. As the users do not notice the proxy
routing, the scenario is named "transparent" proxy.
D With load balancing, the data traffic for selected protocols is diverted over
a certain DSL port that uses an additional external ADSL modem.
D A server in the local network is only supposed to be accessible from the
WAN via a fixed IP address; this is routed via a certain WAN interface.
D VPN traffic is forwarded to a VPN tunnel with dynamic end points by using
the routing tag '0'; the company's remaining Internet traffic is diverted to
another firewall by means of another suitable routing tag.
Suitable entries can be made in the firewall to select channels according to
information other than just the destination IP address. These entries are sup-
plemented with a special routing tag that is used to control the channel se-
lection with the routing table. For example, a rule adds the routing tag '2' to
the entire data traffic for a local group of computers (defined by an IP address
range). Alternatively, certain protocols receive a different supplementary
routing tag.
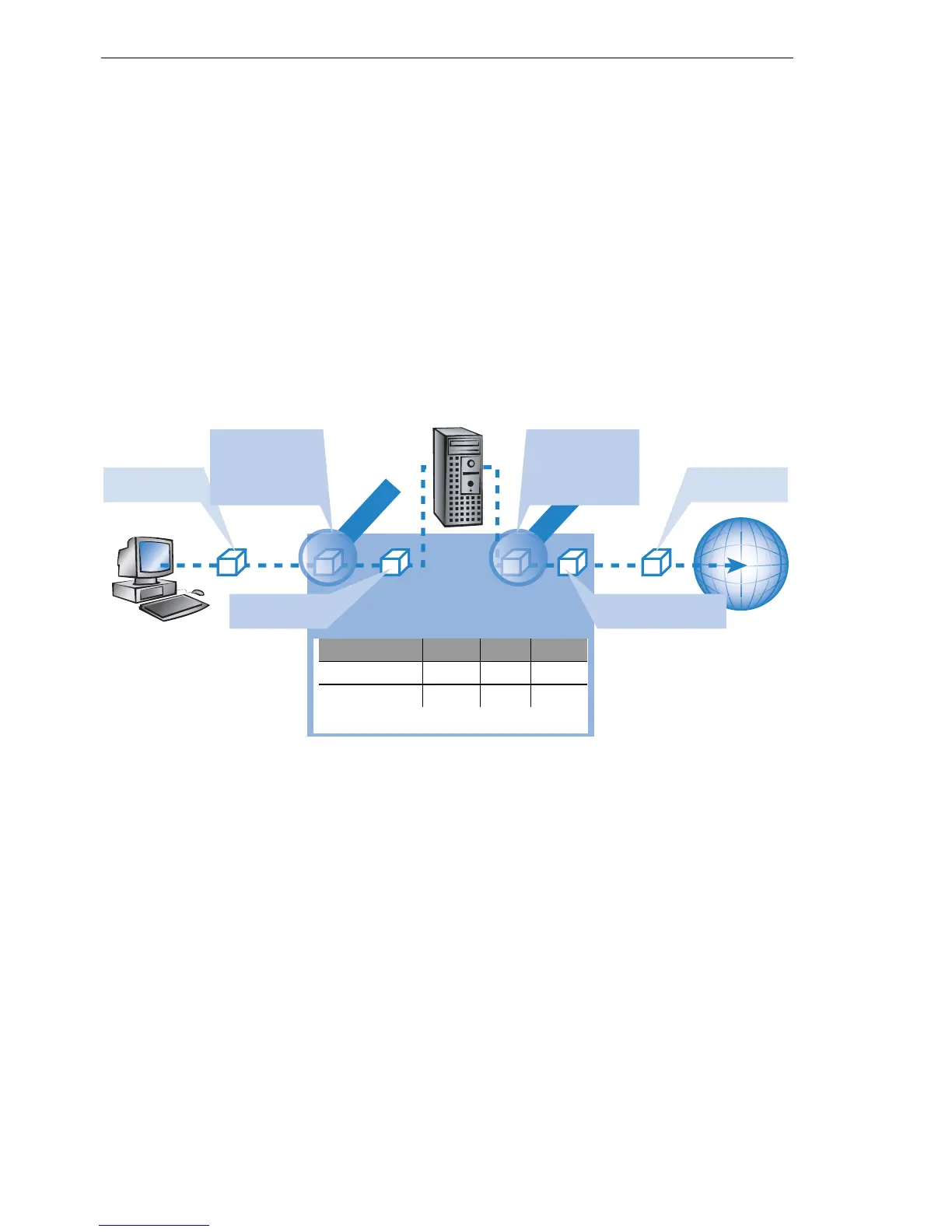
The diagram demonstrates the application of policy-routing with load balanc-
ing:
Data packet with
target address in
Internet
IP address Netmask Rt-Tag Router
255.255.255.255 0.0.0.0 1 Proxy
255.255.255.255 0.0.0.0 0 Internet
Extract of IP routing table
Source: local Net-
work
Destination: all
Port: 80
Action: Transfer
Tag: 1
Data packet with desti-
nation address and IP
routing tag '1'
Firewall rule
Source: Proxy
Destination: all
Port: 80
Action: Transfer
Tag: 0
Firewall rule
Data packet with desti-
nation address and IP
routing tag '0'
Data packet rout-
ed to the Internet
 Loading...
Loading...