Firewall
308
8.5
Denial of Service
BAT54-Rail/F..
Release
7.54
06/08
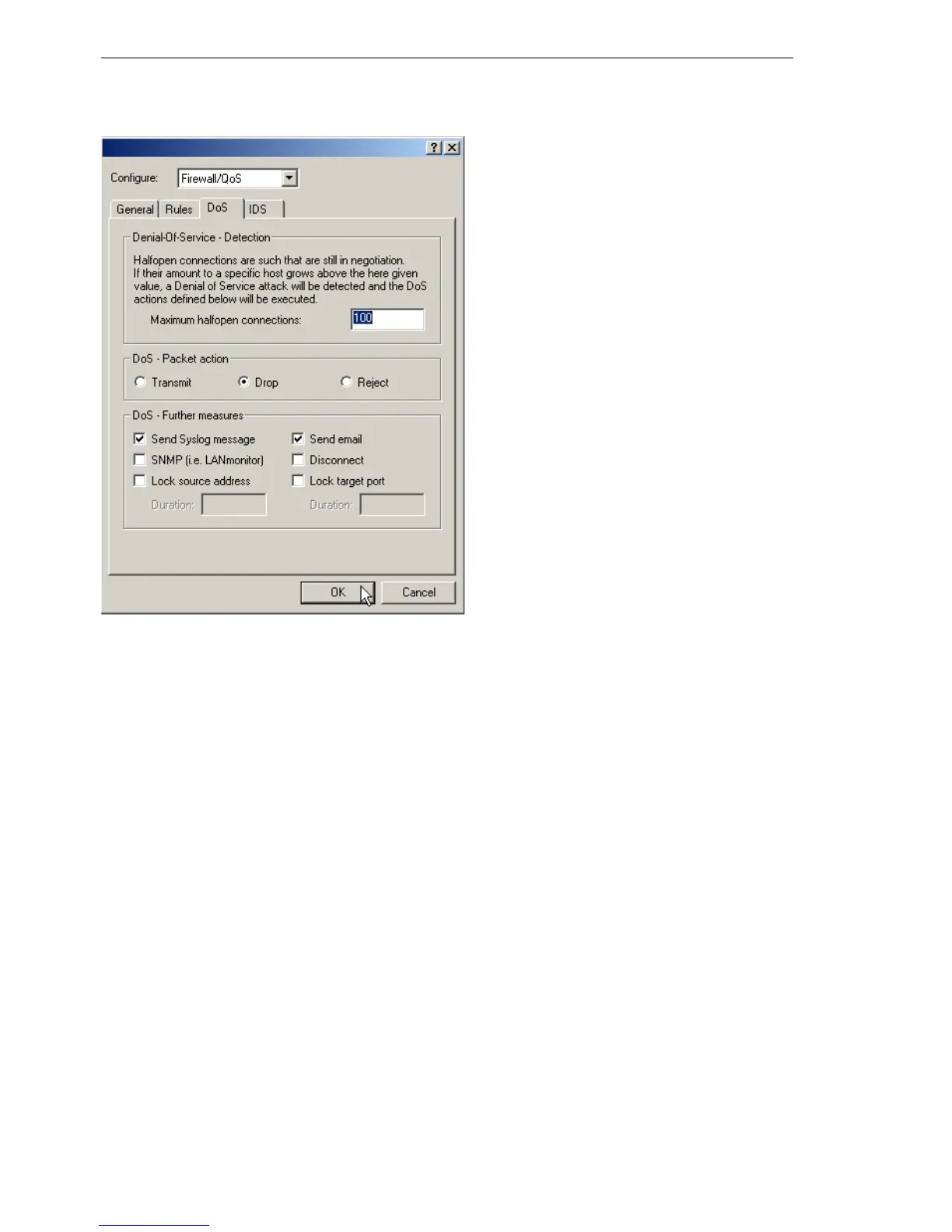
Note: In order to drastically reduce the susceptibility of the network for DoS
attacks in advance, packets from distant networks may be only accepted,
if either a connection has been initiated from the internal network, or the
incoming packets have been accepted by an explicit filter entry (source:
distant network, destination: local area network). This measure already
blocks a multitude of attacks.
For all permitted accesses explicitly connection state, source addresses and
correctness of fragments are tracked in a BAT. This happens for incoming
and for outgoing packets, since an attack could be started also from within
the local area network.
This part is configured centrally in order not to open a gate for DoS attacks
by incorrect configuration of the Firewall. Apart from specifying the maximum
number of half-open connections, fragment action and possible notification
mechanisms, also these more extensive possibilities of reaction exist:
D The connection will be cut off.
D The sender address will be blocked for an adjustable period of time.
D The destination port of the scan will be blocked for an adjustable period
of time.
 Loading...
Loading...