476 | Security
www.dell.com | support.dell.com
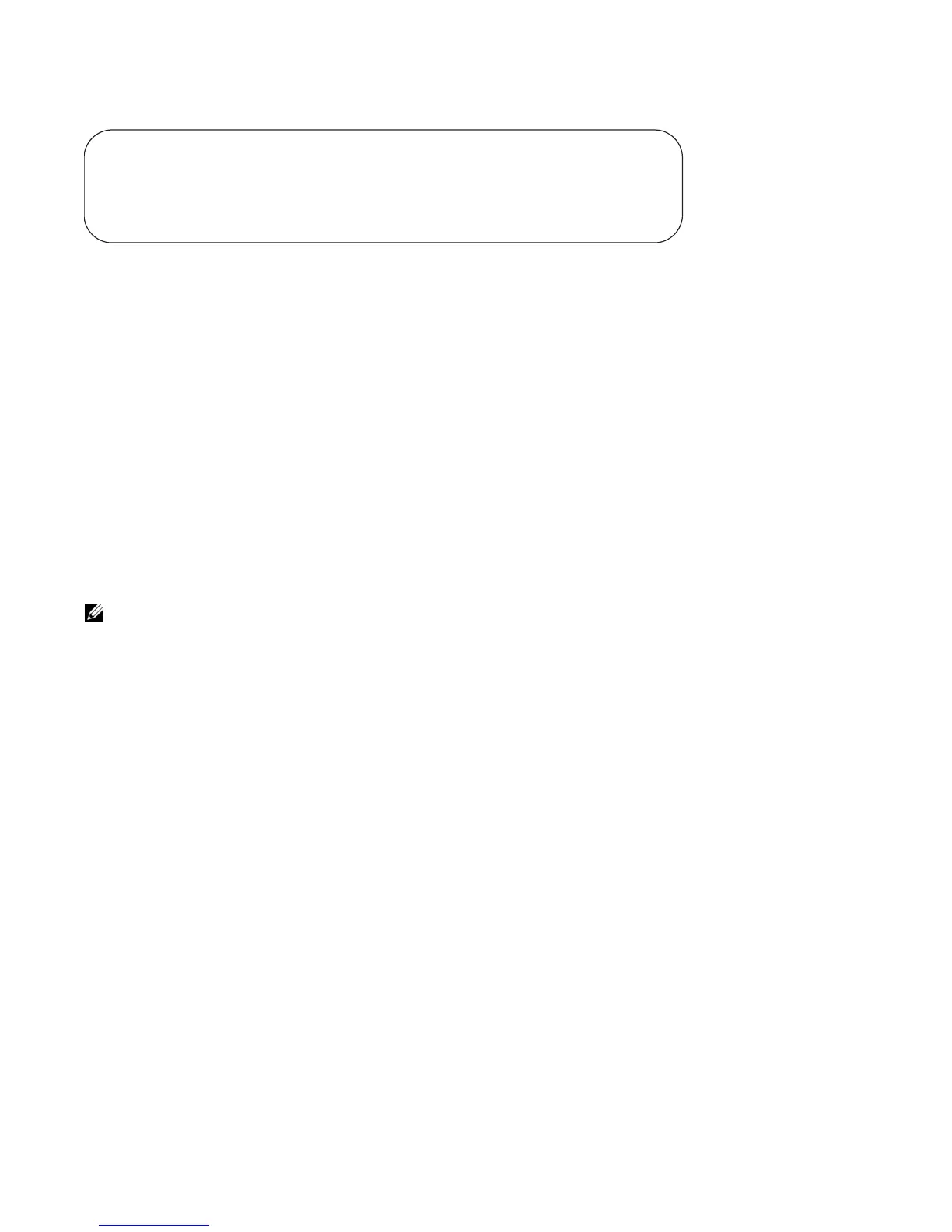
Figure 28-3. show accounting Command Example
AAA Authentication
FTOS supports a distributed client/server system implemented through authentication, authorization, and
accounting (AAA) to help secure networks against unauthorized access. In the Dell Force10
implementation, the system acts as a remote authentication dial-in service (RADIUS) or TACACS+ client
and sends authentication requests to a central RADIUS or TACACS+ server that contains all user
authentication and network service access information.
Dell Force10 uses local usernames/passwords (stored on the Dell Force10 system) or AAA for login
authentication. With AAA, you can specify the security protocol or mechanism for different login methods
and different users. In FTOS, AAA uses a list of authentication methods, called method lists, to define the
types of authentication and the sequence in which they are applied. You can define a method list or use the
default method list. User-defined method lists take precedence over the default method list.
Configuration Task List for AAA Authentication
The following sections provide the configuration tasks:
• Configure Login Authentication for Terminal Lines
• Configure AAA Authentication Login Methods
• Enable AAA Authentication
• AAA Authentication—RADIUS
For a complete listing of all commands related to login authentication, refer to the Security chapter in the
FTOS Command Reference Guide.
Configure Login Authentication for Terminal Lines
You can assign up to five authentication methods to a method list. FTOS evaluates the methods in the order
in which you enter them in each list. If the first method list does not respond or returns an error, FTOS
applies the next method list until the user either passes or fails the authentication. If the user fails a method
list, FTOS does not apply the next method list.
Note: If a console user logs in with RADIUS authentication, the privilege level will be applied from the
RADIUS server if the privilege level is configured for that user in RADIUS whether or not RADIUS
authorization is configured.
FTOS#show accounting
Active accounted actions on tty2, User admin Priv 1
Task ID 1, EXEC Accounting record, 00:00:39 Elapsed, service=shell
Active accounted actions on tty3, User admin Priv 1
Task ID 2, EXEC Accounting record, 00:00:26 Elapsed, service=shell
FTOS#

 Loading...
Loading...











