Intrusion Protection Custom signatures
FortiGate Version 3.0 MR4 Administration Guide
01-30004-0203-20070102 355
Creating custom signatures
Use custom signatures to block or allow specific traffic. For example, to block
traffic containing pornography, add custom signatures similar to the following:
F-SBID (--protocol tcp; --flow established; --content "nude cheerleader"; --
no_case)
When adding the signature, set action to Drop Session.
For more information on custom signature syntax, see the FortiGate Intrusion
Protection System (IPS) Guide.
To create a custom signature, go to Intrusion Protection > Signature > Custom.
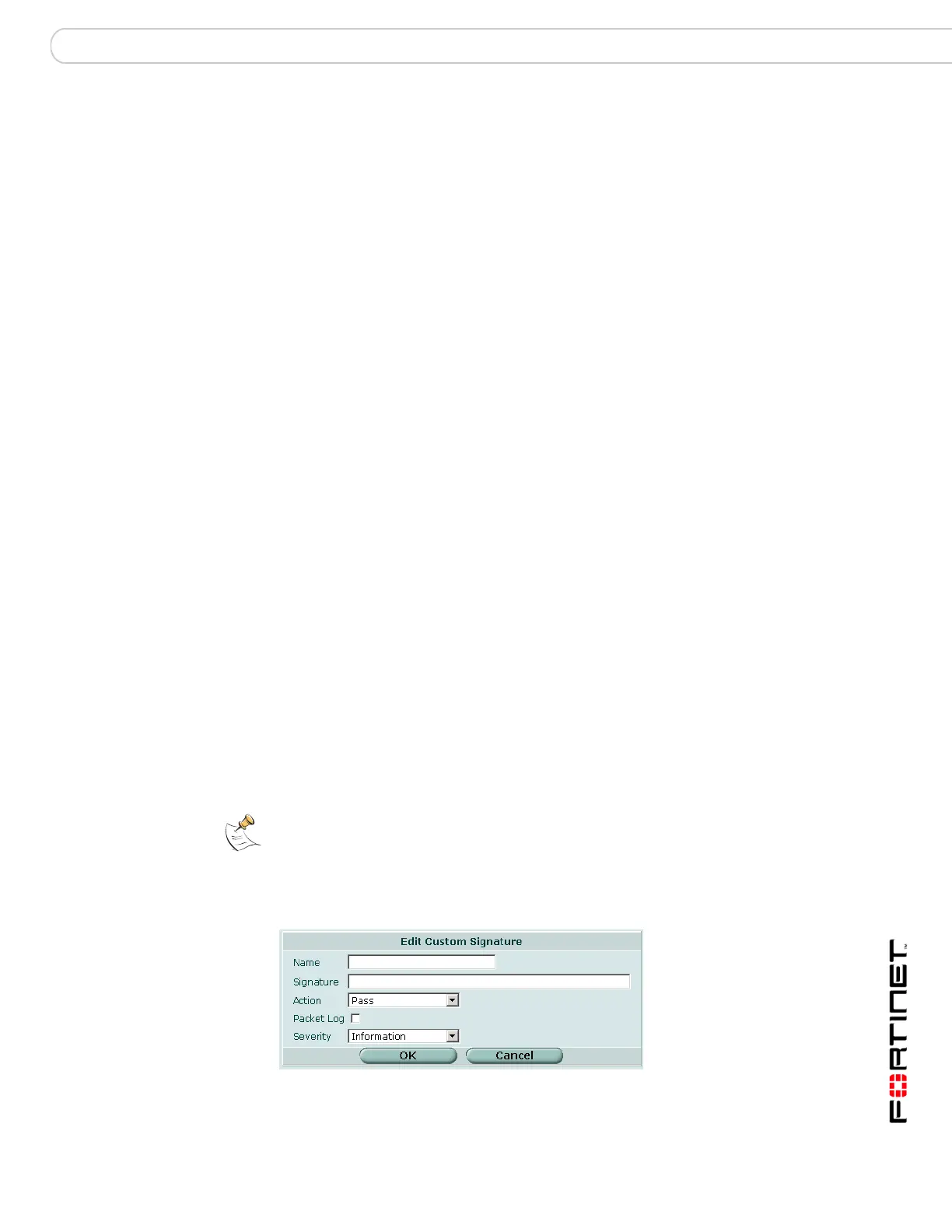
Figure 233:Edit Custom Signature
View custom
signatures with
severity
Select filters then select Go to view only those custom signatures that
match the filter criteria. Sort criteria can be <=, =, >= to All, Information,
Low, Medium, High, or Critical.
Create New Select to create a new custom signature.
Clear all custom
signatures icon
Remove all the custom signatures.
Reset to
recommended
settings icon
Reset all the custom signatures to the recommended settings.
Name The custom signature name.
Enable The status of each custom signature. A check mark in the box indicates
the signature is enabled.
Logging The logging status of each custom signature. A check mark in the box
indicates logging is enabled for the custom signature.
Action The action set for each custom signature. Action can be Pass, Drop,
Reset, Reset Client, Reset Server, Drop Session, Clear Session, or
Pass Session. If logging is enabled, the action appears in the status field
of the log message generated by the signature. See Table 36 for
descriptions of the actions.
Severity The severity level set for each custom signature. Severity level can be
Information, Low, Medium, High, or Critical. Severity level is set for
individual signatures.
Delete icon Select to delete the custom signature.
Edit icon Select to edit the following information: Name, Signature, Action, Packet
Log, and Severity.
Note: Custom signatures are an advanced feature. This document assumes the user has
previous experience creating intrusion detection signatures.

 Loading...
Loading...











