Firewall
BAT54-Rail/F..
Release
7.54
06/08
8.3
The BAT Firewall
283
U Set-up of an explicit "Deny All" strategy
For maximum protection and optimum control of the data traffic it is recom-
mended to prevent first any data transfer by the Firewall. Then only the nec-
essary functions and communication paths are allowed selectively. This
offers e.g. protection against so-called "Trojans" and/or e-mail viruses, which
set up actively an outgoing connection on certain ports.
Some typical applications are shown in the following.
Note: All filters described here can be installed very comfortably with the
Firewall wizard, and if necessary be further refined with e.g. LANconfig.
D Example configuration “Basic Internet”
U Deny All: The most important Firewall rule!
The Deny All rule is by far the most important rule to protect local networks.
By this rule the Firewall operates according to the principle: “All actions,
which are not explicitly allowed, remain forbidden!“ Only by this strategy
the administrator can be sure not to have “forgotten” an access method,
because only those accesses exist, which have been opened explicitly by
himself.
We recommend to set up the Deny All rule before connecting the LAN via
a BAT to the Internet. Then you can analyse in the logging table (to start e.
g. via LANmonitor), which connection attempts have been blocked by the
Firewall. With the help of this information the Firewall and the “Allow rules“
can be gradually extended.
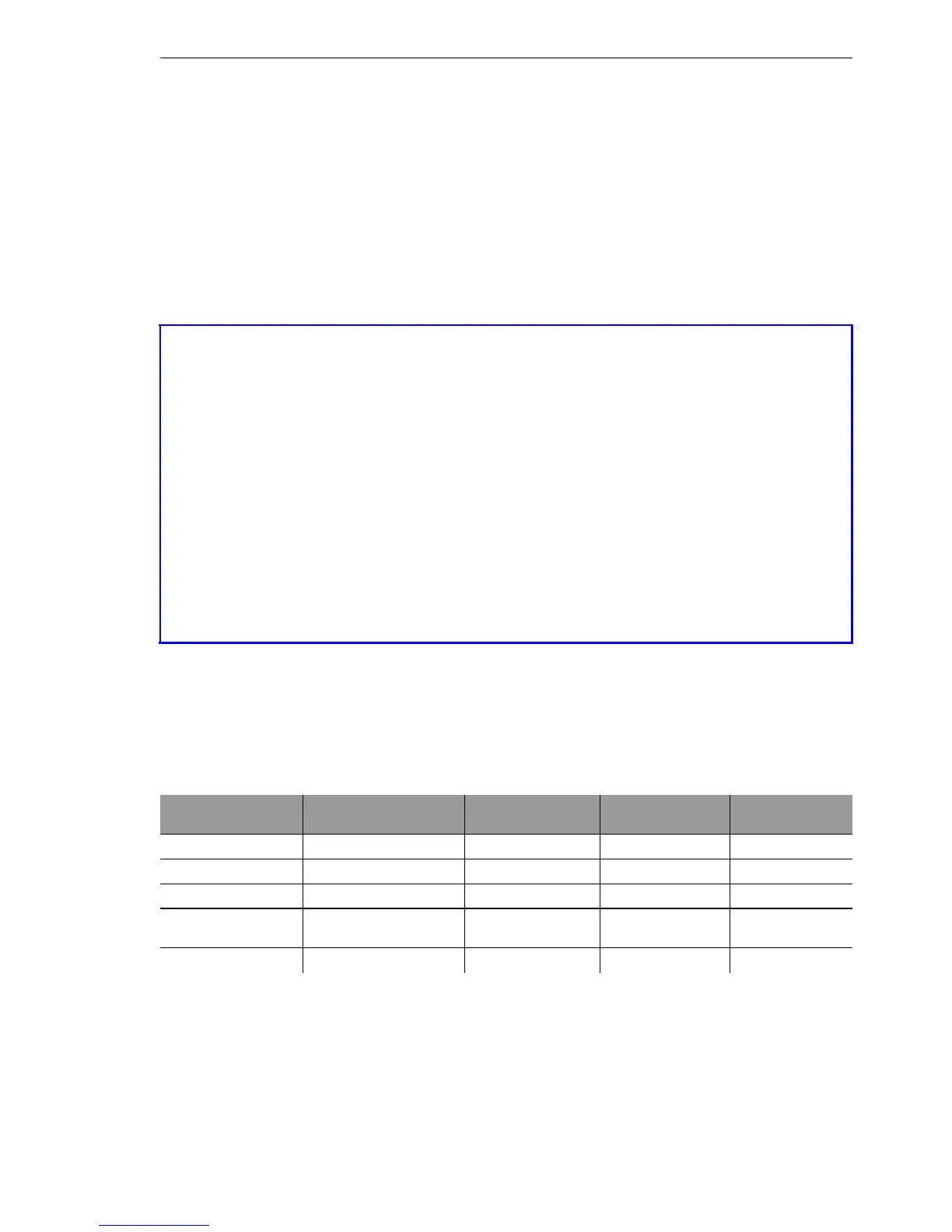
Rule name Source Destination Action Service
(target port)
ALLOW_HTTP Local network All stations transmit HTTP, HTTPS
ALLOW_FTP Local network All stations transmit FTP
ALLOW_EMAIL Local network All stations transmit MAIL, NEWS
ALLOW_DNS_FOR
WARDING
IP address of LANOM
(or: Local network)
transmit transmit DNS
DENY_ALL All stations reject reject ANY
 Loading...
Loading...