5 - 44 WiNG 5.6 Access Point System Reference Guide
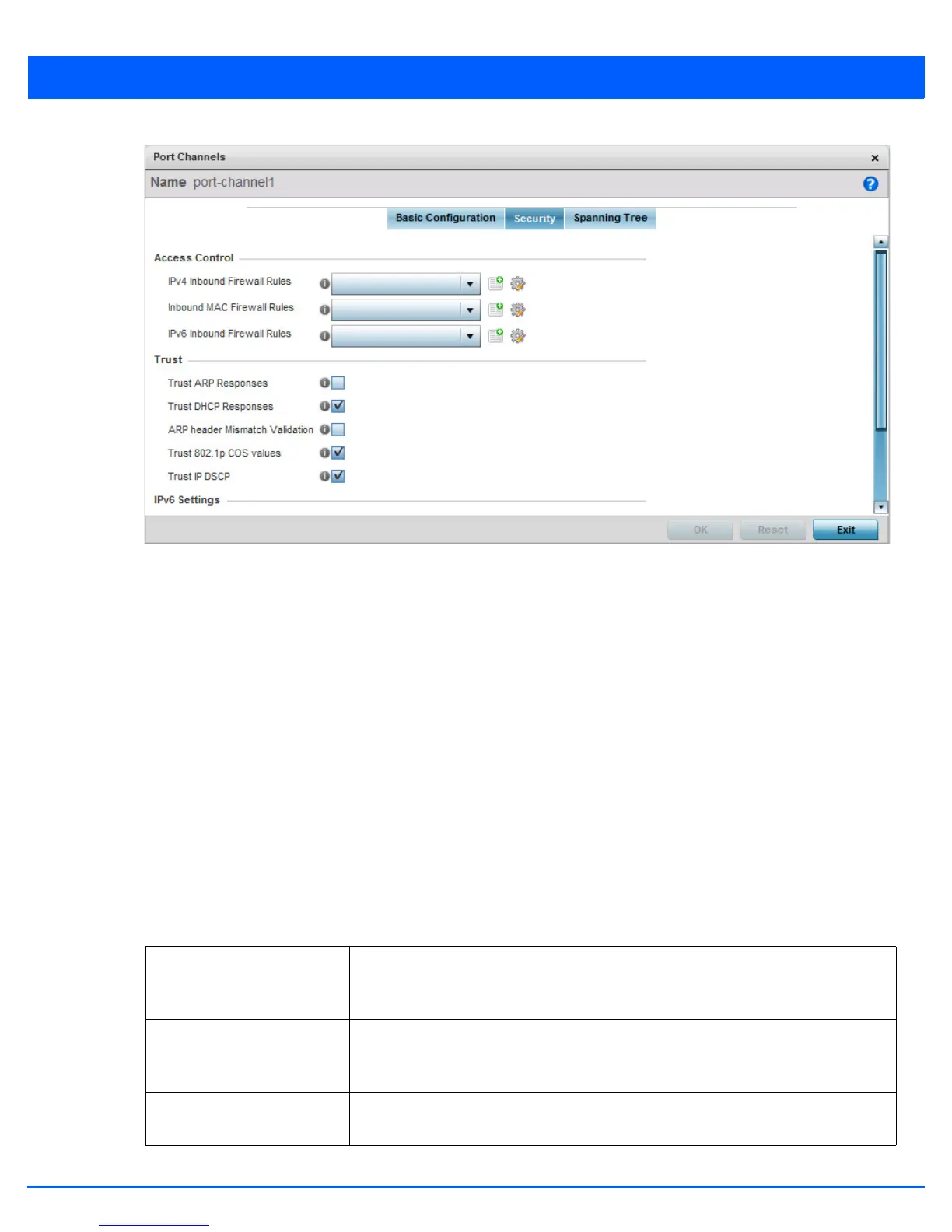
Figure 5-29 Port Channels - Security tab
12. Refer to the Access Control section. As part of the port channel’s security configuration, Inbound IPv4 IP, IPv6 IP and MAC
address firewall rules are required.
Use the Inbound IP Firewall Rules and Inbound MAC Firewall Rules drop-down menus to select the firewall rules to
apply to this profile’s port channel configuration. The firewall inspects IP and MAC traffic flows and detects attacks typically
not visible to traditional wired firewall appliances
Use the IPv4 Firewall Rules drop-down menu to select the IPv4 specific firewall rules to apply to this profile’s port channel
configuration. IPv4 is a connection less protocol for packet switched networking. IPv4 operates as a best effort delivery
method, as it does not guarantee delivery, and does not ensure proper sequencing or duplicate delivery (unlike (TCP). IPv4
hosts can use link local addressing to provide local connectivity.
Use the IPv6 Firewall Rules drop-down menu to select the IPv6 specific firewall rules to apply to this profile’s port channel
configuration. IPv6 is the latest revision of the Internet Protocol (IP) designed to replace IPv4. IPV6 provides enhanced
identification and location information for computers on networks routing traffic across the Internet. IPv6 addresses are
composed of eight groups of four hexadecimal digits separated by colons.
If a firewall rule does not exist suiting the data protection needs of the target port channel configuration, select the Create
icon to define a new rule configuration or the Edit icon to modify an existing firewall rule configuration.
13. Refer to the Trust field to define the following:
Trust ARP Responses Select this option to enable ARP trust on this port channel. ARP packets received on this
port are considered trusted and information from these packets is used to identify rogue
devices within the managed network. The default value is disabled.
Trust DHCP Responses Select this option to enable DHCP trust. If enabled, only DHCP responses are trusted
and forwarded on this port channel, and a DHCP server can be connected only to a
DHCP trusted port. The default value is enabled.
ARP header Mismatch
Validation
Select this option to enable a mismatch check for the source MAC in both the ARP and
Ethernet header. The default value is enabled.

 Loading...
Loading...











