Security Configuration 8 - 23
8.3 Device Fingerprinting
Security Configuration
With the increase in popularity of Bring Your Own Devices (BYOD) for use in the corporate environment, there is an increase in
the number of possible vectors of attacks on the network. BYOD devices are inherently unsafe as the organization does not
have control on the level of security on these devices. The organizations can protect their network by limiting how and what
these BYODs can access on and through the corporate network.
Device fingerprinting feature enables administrators to control how BYOD devices access the network and control their access
permissions.
To configure device fingerprinting:
1. Select Configuration tab from the Web user interface.
2. Select Security
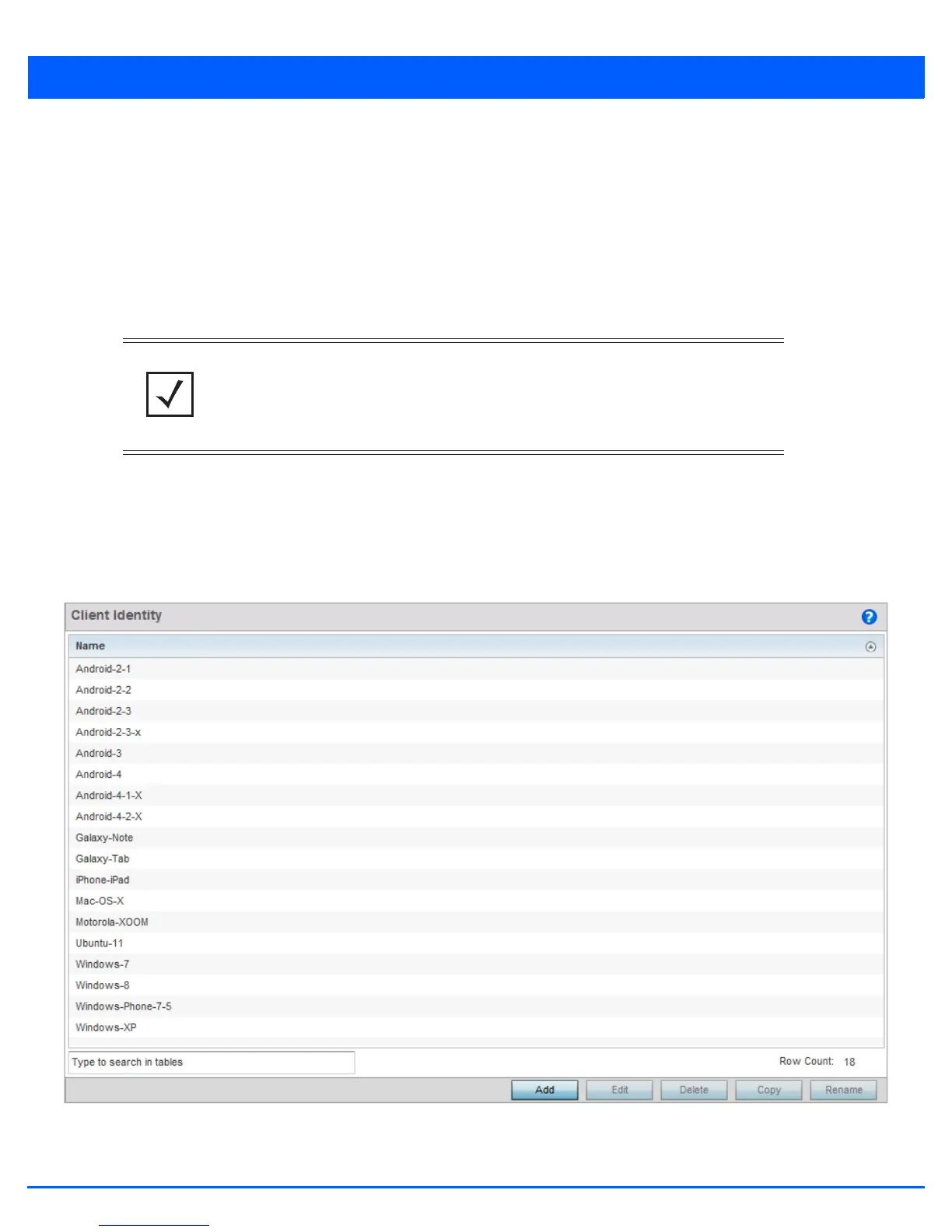
3. Select Device Fingerprinting to display existing device fingerprinting configuration screens. The Client Identity screen
displays:
Figure 8-11 Security - Device Fingerprinting - Client Identity screen
NOTE: Ensure DHCP is enabled on the WLAN on which device fingerprinting is to be
enabled.

 Loading...
Loading...











