5 - 136 WiNG 5.6 Access Point System Reference Guide
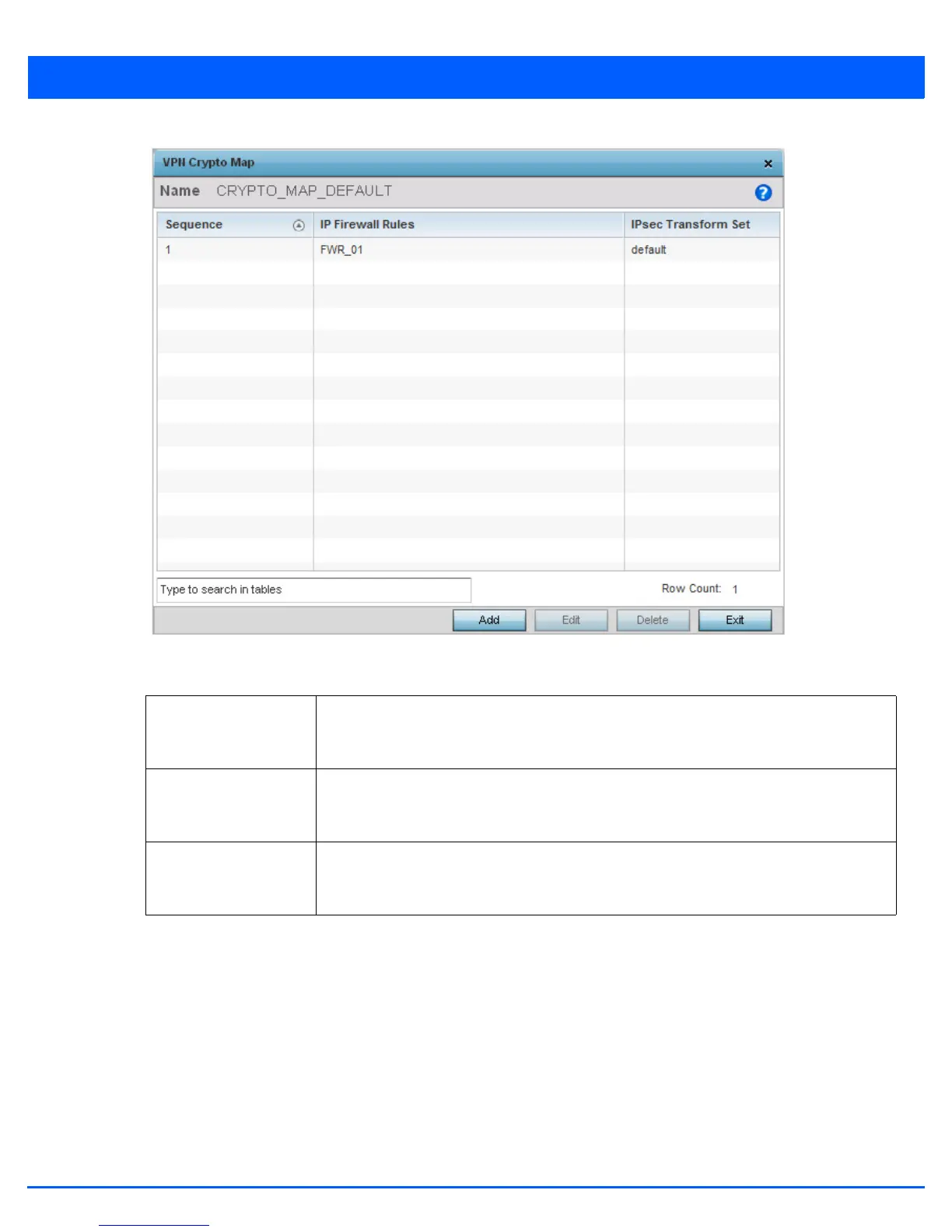
Figure 5-87 Profile Security - VPN Crypto Map screen
24. Review the following before determining whether to add or modify a crypto map configuration:
25. If requiring a new crypto map configuration, select the Add button. If updating the configuration of an existing crypto map,
select it from amongst those available and select the Edit button.
Sequence Each crypto map configuration uses a list of entries based on a sequence number. Specifying
multiple sequence numbers within the same crypto map, provides the flexibility to connect
to multiple peers from the same interface, based on the sequence number (from 1 - 1,000).
IP Firewall Rules Lists the IP firewall rules defined for each displayed crypto map configuration. Each firewall
policy contains a unique set of access/deny permissions applied to the VPN tunnel and its
peer connection.
IPSec Transform Set Displays the transform set (encryption and hash algorithms) applied to each listed crypto map
configuration. Thus, each crypto map can be customized with its own data protection and
peer authentication schemes.

 Loading...
Loading...











