Newtec Proprietary
Confidentiality: Unrestricted
R3.2_v1.0
311/387
Feature Descriptions
MDM9000 Satellite Modem
16.18.4.2 64-Bit Keys
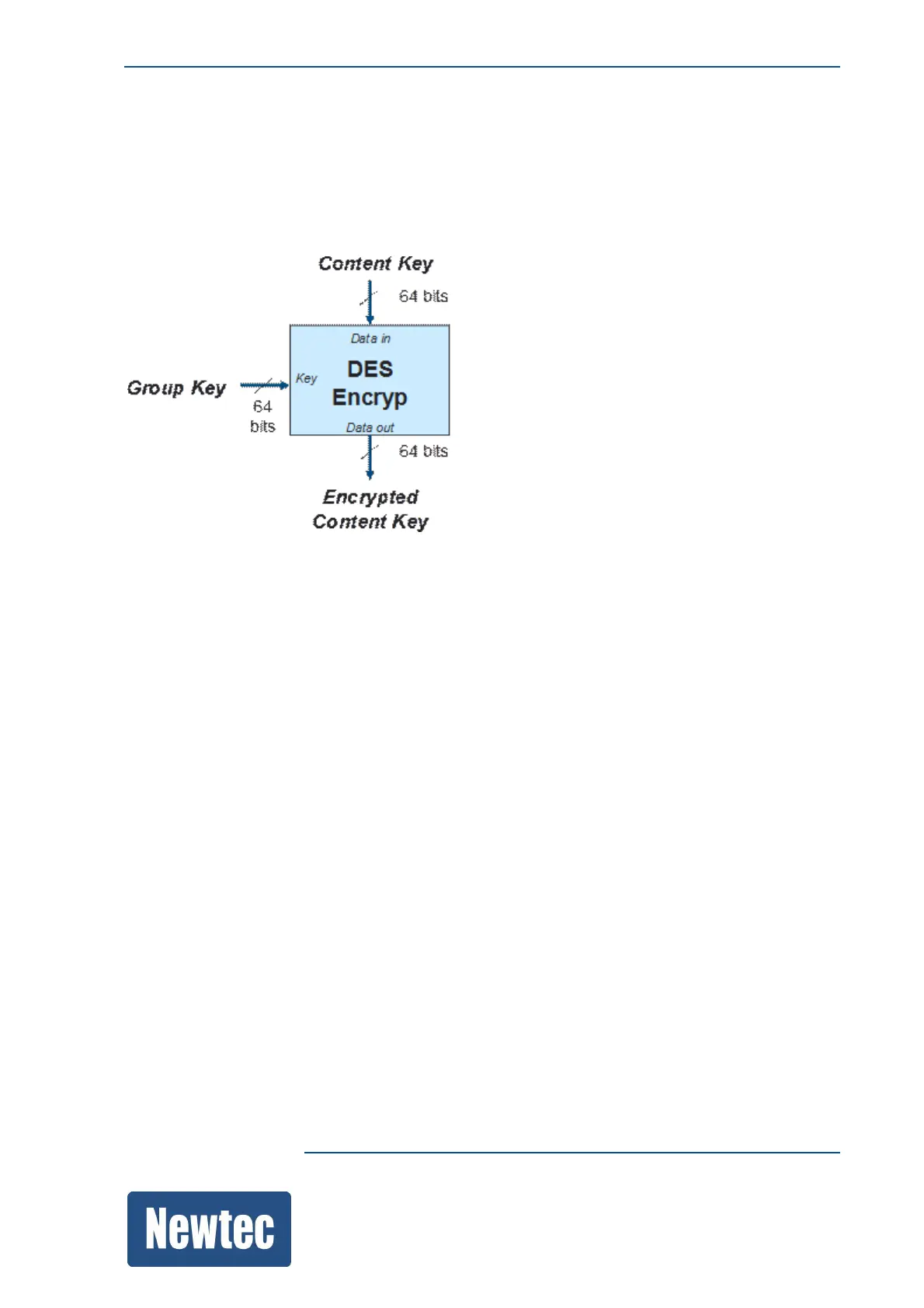
A similar process is used for the computation of encrypted content keys in the 64-bit mode. The
computation of the encrypted content key from a given content key is depicted in the following
figure:
The DES algorithm used is the one described in the FIPS-46-3 standard from the NIST.
The following lines provide a few examples of key computations for reference:
Example 1:
• Content Key: 278da56a0f06aa1f
• Group Key: fb5f9c585dd359aa
• Encrypted Content Key: bf561dd5e15890b7
Example 2:
• Content Key: 1234567890abcdef
• Group Key: fb5f9c585dd359aa
• Encrypted Content Key: d46f63e2cc998eec
Example 3:
• Content Key: 1234567890abcdef
• Group Key: 7fae81fad3154384
• Encrypted Content Key: be407096c6104b1e
 Loading...
Loading...